16
Cisco 2811 and Cisco 2821 Integrated Services Router FIPS 140-2 Non Proprietary Security Policy
OL-8663-01
Cisco 2811 and Cisco 2821 Routers
• no set session-key inbound ah spi hex-key-data
• no set session-key outbound ah spi hex-key-data
• no set session-key inbound esp spi cipher hex-key-data [authenticator hex-key-data]
• no set session-key outbound esp spi cipher hex-key-data [authenticator hex-key-data]
The DRAM running configuration must be copied to the start-up configuration in NVRAM in order to
completely zeroize the keys.
The following commands will zeroize the pre-shared keys from the DRAM:
• no crypto isakmp key key-string address peer-address
• no crypto isakmp key key-string hostname peer-hostname
The DRAM running configuration must be copied to the start-up configuration in NVRAM in order to
completely zeroize the keys.
The module supports the following keys and critical security parameters (CSPs). Note that keys stored
in NVRAM are in plaintext unless the configuration file encryption key is configured via the “key
config-key” command is used.
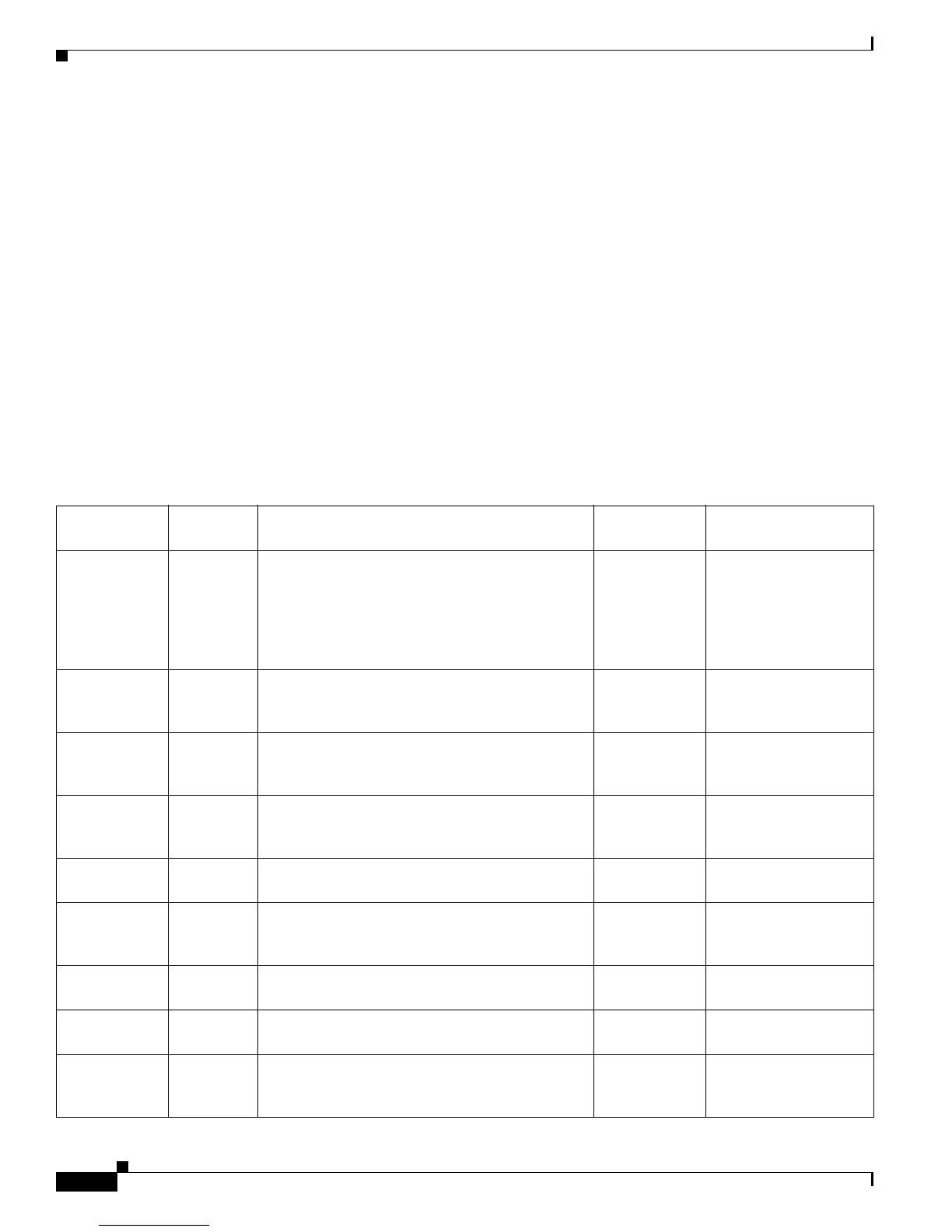
Table 9 Cryptographic Keys and CSPs
Name Algorithm Description Storage
Zeroization
Method
PRNG Seed X9.31 This is the seed for X9.31 PRNG. This CSP is
stored in DRAM and updated periodically after
the generation of 400 bytes – after this it is
reseeded with router-derived entropy; hence, it is
zeroized periodically. Also, the operator can turn
off the router to zeroize this CSP.
DRAM
(plaintext)
Automatically every
400 bytes, or turn off
the router.
Diffie Hellman
private
exponent
DH The private exponent used in Diffie-Hellman
(DH) exchange. Zeroized after DH shared secret
has been generated.
DRAM
(plaintext)
Automatically after
shared secret generated.
Diffie Hellman
public key
DH The public key used in Diffie-Hellman (DH)
exchange as part of IKE. Zeroized after the DH
shared secret has been generated.
DRAM
(plaintext)
Automatically after
shared secret generated.
skeyid Keyed
SHA-1
Value derived from the shared secret within IKE
exchange. Zeroized when IKE session is
terminated.
DRAM
(plaintext)
Automatically after IKE
session terminated.
skeyid_d Keyed
SHA-1
The IKE key derivation key for non ISAKMP
security associations.
DRAM
(plaintext)
Automatically after IKE
session terminated.
skeyid_a HMAC-
SHA-1 or
DES MAC
The ISAKMP security association authentication
key.
DRAM
(plaintext)
Automatically after IKE
session terminated.
skeyid_e DES/TDES
/AES
The ISAKMP security association encryption key. DRAM
(plaintext)
Automatically after IKE
session terminated.
IKE session
encrypt key
DES/TDES
/AES
The IKE session encrypt key. DRAM
(plaintext)
Automatically after IKE
session terminated.
IKE session
authentication
key
HMAC-
SHA-1 or
DES MAC
The IKE session authentication key. DRAM
(plaintext)
Automatically after IKE
session terminated.
 Loading...
Loading...