D-Link International
Confidential and proprietary
5
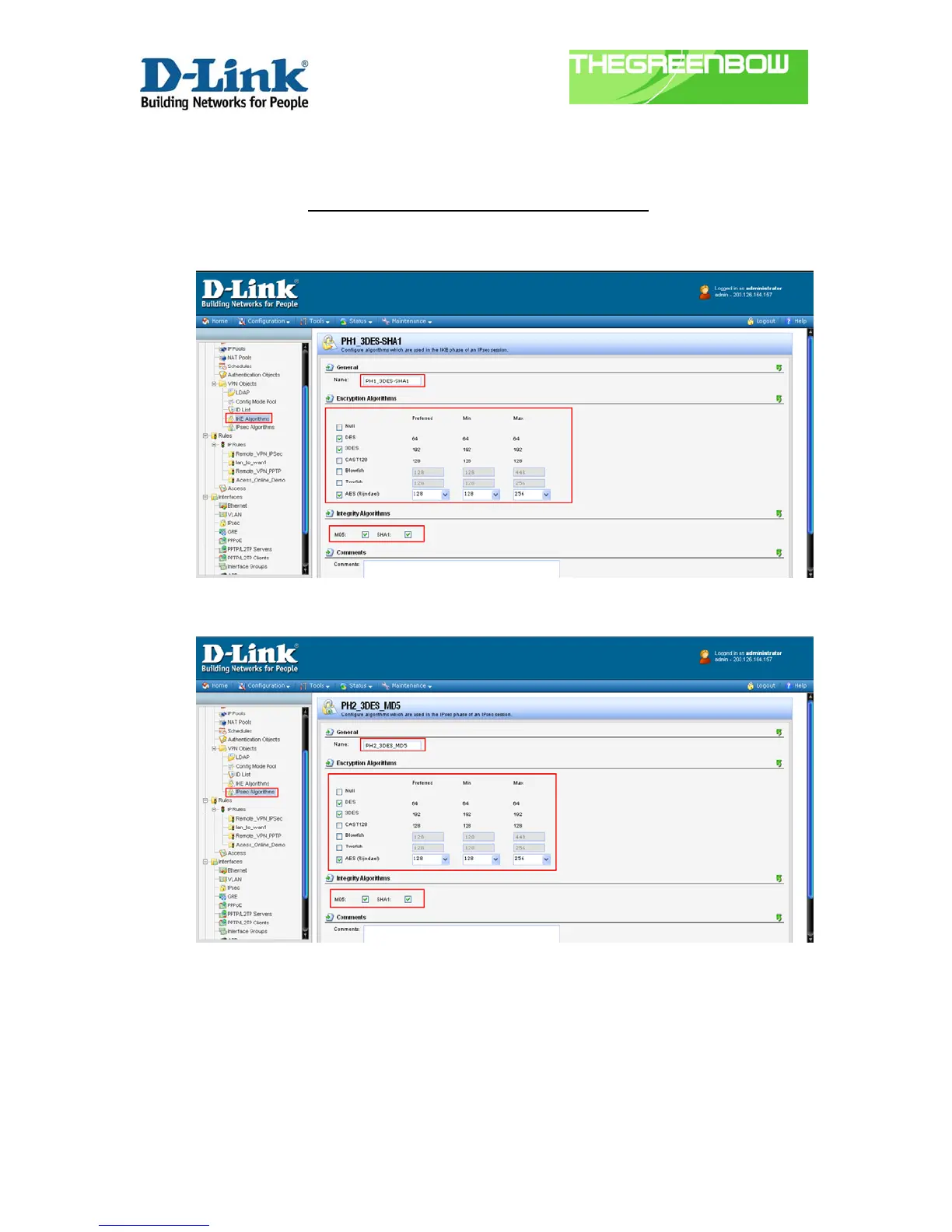
6.1.1.2) Phase 1 and Phase 2 algorithms setup
1) At the “IKE Algorithms”, select the Encryption and Integrity
algorithms for your phase 1 authenticate.
2) Next is the “IPSec Algorithms”, select the Encryption and
Integrity algorithms for the Phase 2.

 Loading...
Loading...