before executing a command, the request of authorization is sent to the Tacacs Server and, only if
it replies and accepts, the command will be executed, otherwise the command is refused.
We suppose to have configured in the database of the Server, a user called limited which has the
possibility to execute only some of the available commands. The configuration of the database
changes according to the Tacacs Server used. For example:
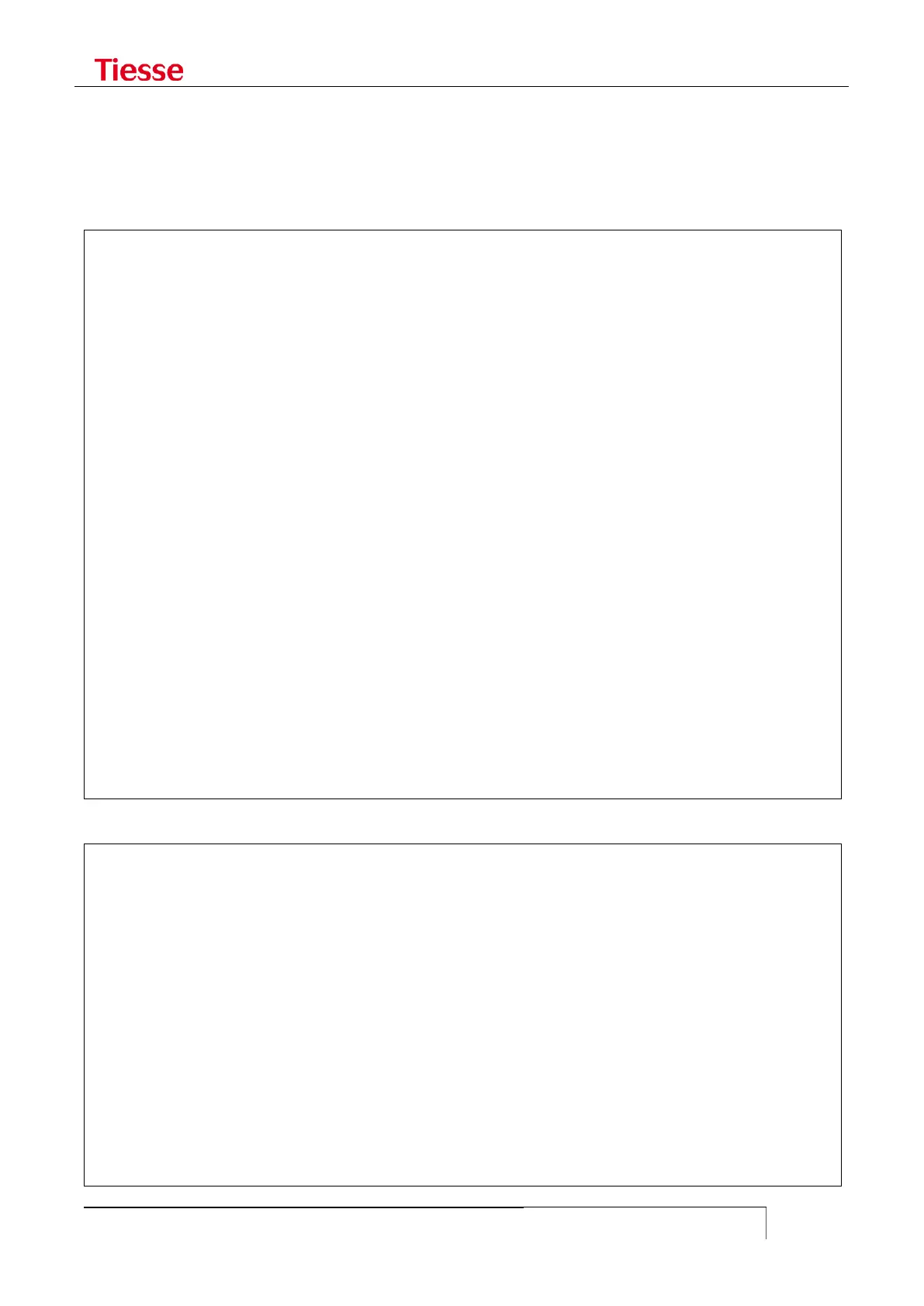
user = limited {
login = cleartext limited
service = exec {
priv-lvl=15
}
cmd = "set" {
permit "eth1 .*"
permit "gprs apn .*"
permit "isdn dialer ippp1 *"
}
cmd = "ping" {
permit .*
}
cmd = "show" {
deny "interface *"
deny "ip bgp .*"
permit .*
}
cmd = "traceroute" {
permit .*
}
cmd = "shell" {
deny .*
}
cmd = "iptables" {
deny .*
}
}
A few examples of execution of forbidden commands are:
vll$ telnet 10.10.113.1
---------------------------------------------------------------
(IMOLA) (port 0)
---------------------------------------------------------------
login: limited
Password:
TACACS+: Authentication OK
Service Type is: Administrative-User
Privilige Level is: 15
Idle timeout is set to 3600 seconds
Connected Users:
pts/0 limited@IMOLA
You are logged on pts/0
limited@IMOLA> set loopback 7.1.1.123
% Command "set loopback 7.1.1.123" rejected by TACACS+
 Loading...
Loading...