2
Secure Installation 2-1
2
Secure Installation
This section outlines the planning and implementation process for a secure installation
and configuration, describes several recommended deployment topologies for the
systems, and explains how to secure a tape library.
Understand Your Environment
To better understand security needs, the following questions must be asked:
Which resources need to be protected?
Many resources in the production environment can be protected. Consider the
resources needing protection when deciding the level of security that you must
provide.
From whom are the resources being protected?
The library must be protected from everyone on the Internet. But should the library be
protected from the employees on the intranet in your enterprise?
What will happen if the protections on strategic resources fail?
In some cases, a fault in a security scheme is easily detected and considered nothing
more than an inconvenience. In other cases, a fault might cause great damage to
companies or individual clients that use the tape drive. Understanding the security
ramifications of each resource will help protect it properly.
Securing the Library
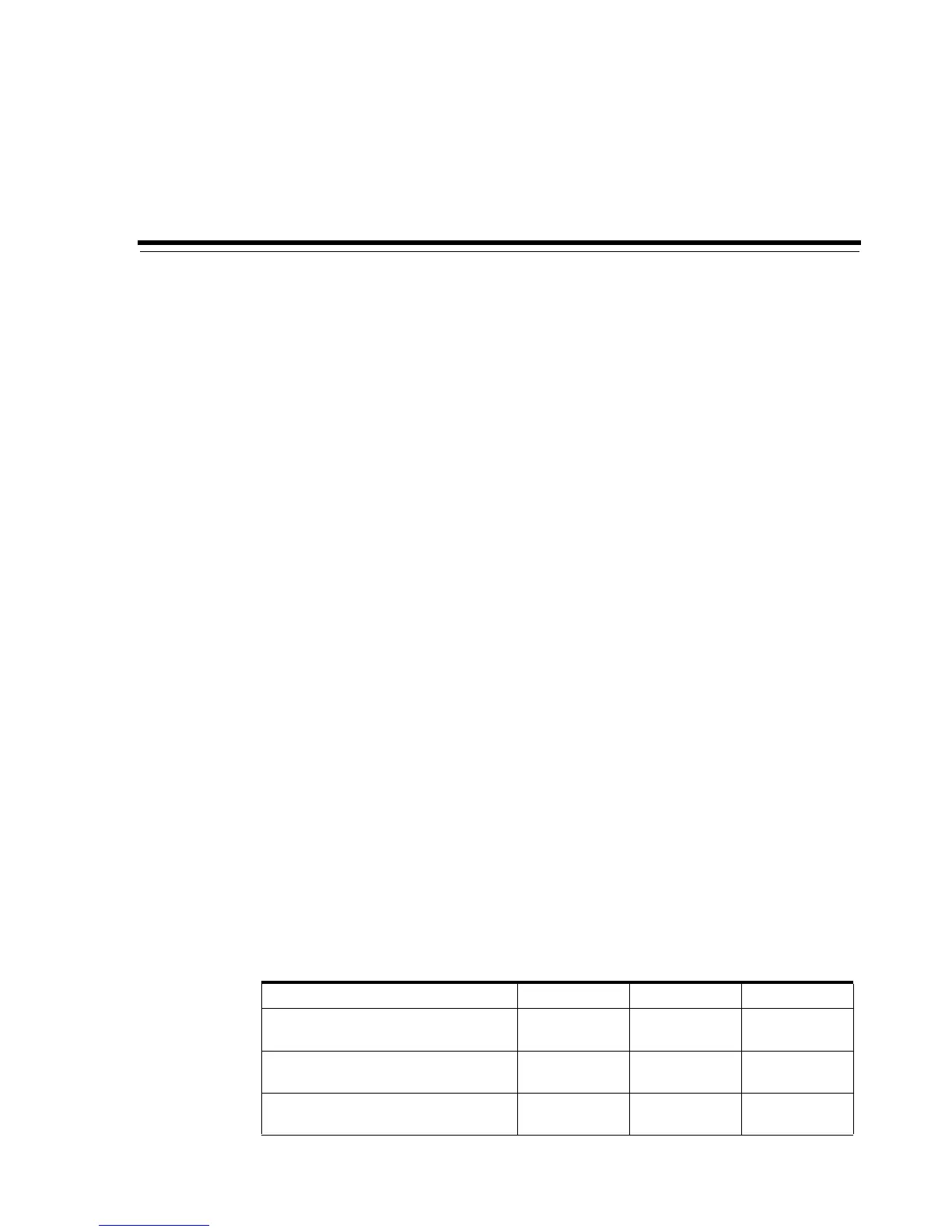
By default, the library uses ports listed in the following table. The firewall should be
configured to allow traffic to use these ports and that any unused ports are blocked.
The SL8500 and SL3000 libraries support IPv4.
Table 2–1 Network ports used
Port SL500 SL3000 SL8500
22 tcp - SSH CLI and SLC access -
inbound stateful
XXX
115 tcp - SFTP code download from
SLC inbound stateful
XXX
161 udp - SNMP library agent requests
- inbound stateful
XXX

 Loading...
Loading...









