$."R%*6,).7S%67)/
]8&;'%8&'<&$%)4&'2+'&;$A5&#.'$::&++'%9'%8&':9;%495'"$;&5'$;#':)44&;%
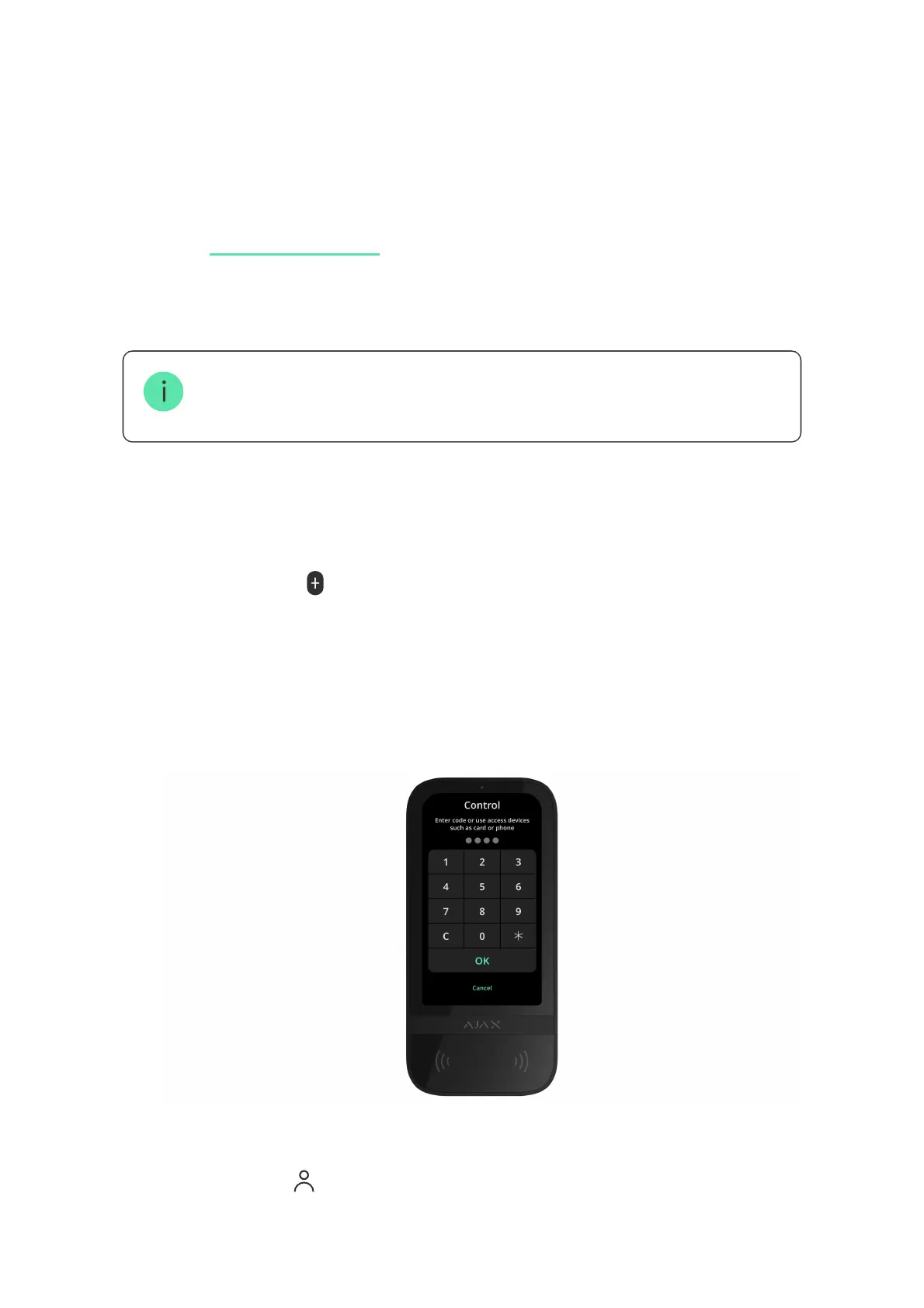
+7+%&?'+%$%&'2+'A59:6&#@'B9');A59:6'2%.'%8&')+&4'+89)5#'$)%8&;%2:$%&G
&;%&4'$;' '94'A42;*'$'"&4+9;$5'$::&++'#&C2:&'%9'%8&
6&7"$#@
I<'"4&M$)%8942T$%29;'2+'&;$A5&#.'%8&'Arming without Code'<&$%)4&'2+
);$C$25$A5&'2;'%8&'6&7"$#'+&%%2;*+@
You can authenticate in two ways:
%::.):.7%6"'+)&"
1.
I;'%8&'Control' '%$A@'(<%&4'59*2;.'%8&')+&4'3255'+&&'%8&'+8$4&#
*49)"+'9<'%8&'+7+%&?'X2<'%8&'*49)"'?9#&'2+'$:%2C$%&#Y@'B8&7'$4&
+"&:2D&#'2;'%8&'6&7"$#'+&%%2;*+G'Security Management'→
Shared Groups@'Q7'#&<$)5%.'$55'%8&'+7+%&?'*49)"+'$4&'+8$4&#@
2.
I;'%8&'Log in' '%$A@'(<%&4'59*2;.'%8&')+&4'3255'+&&'$C$25$A5&
 Loading...
Loading...