24
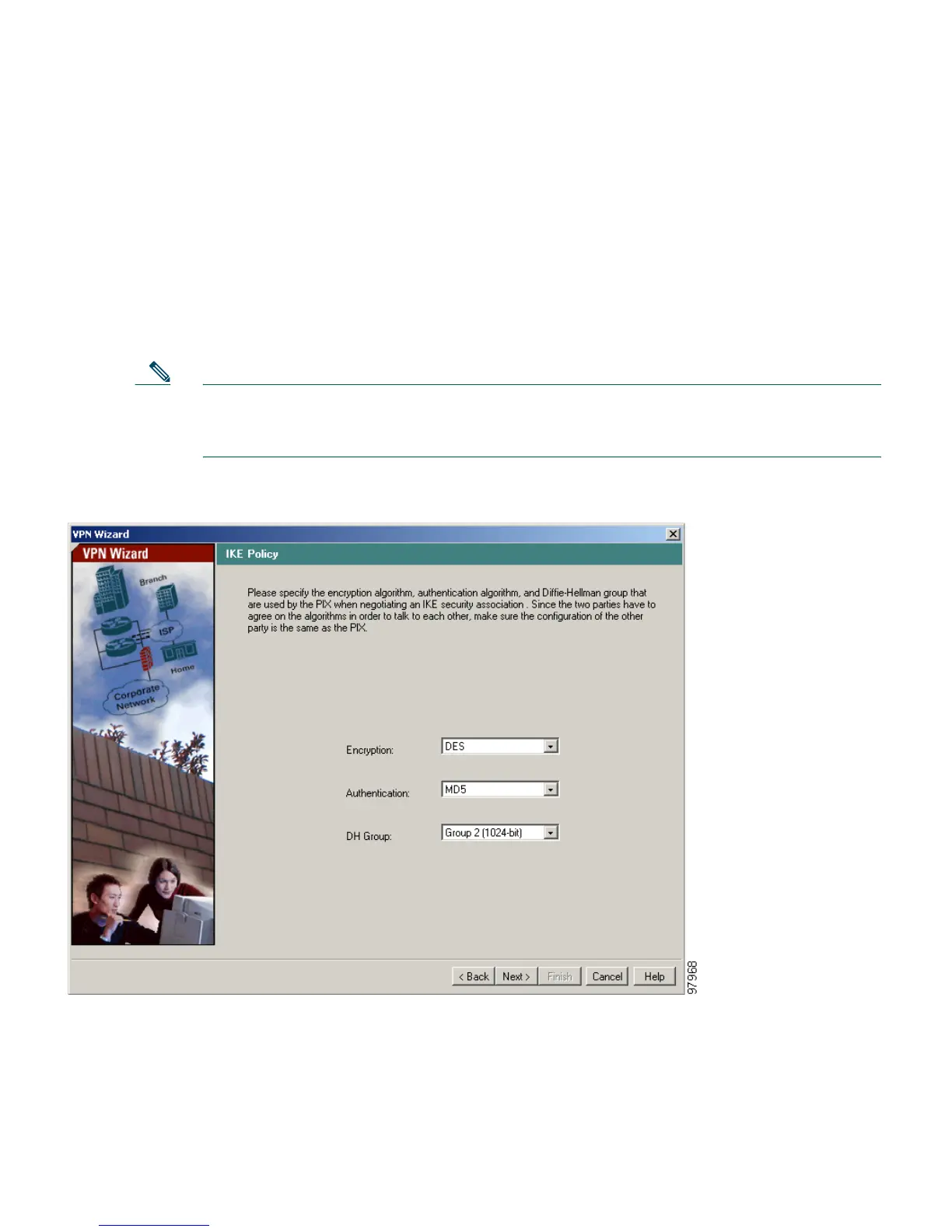
Step 3 Configure the IKE Policy
This step is comprised of two windows:
1. Configure the IKE negotiation parameters.
In most cases, the default values are sufficient to establish secure VPN tunnels between two peers.
a. Select the Encryption (DES/3DES/AES), Authentication algorithms (MD5/SHA), and the
Diffie-Hellman group (1/2/5) used by the PIX 515E during an IKE security association.
Confirm all values before moving to the next window.
Note When configuring PIX 2, enter the exact values for each of the options that you
selected for PIX 1. Encryption mismatches are a common cause of VPN tunnel
failures and can slow down the process.
b. Click the Next button to continue.
 Loading...
Loading...











