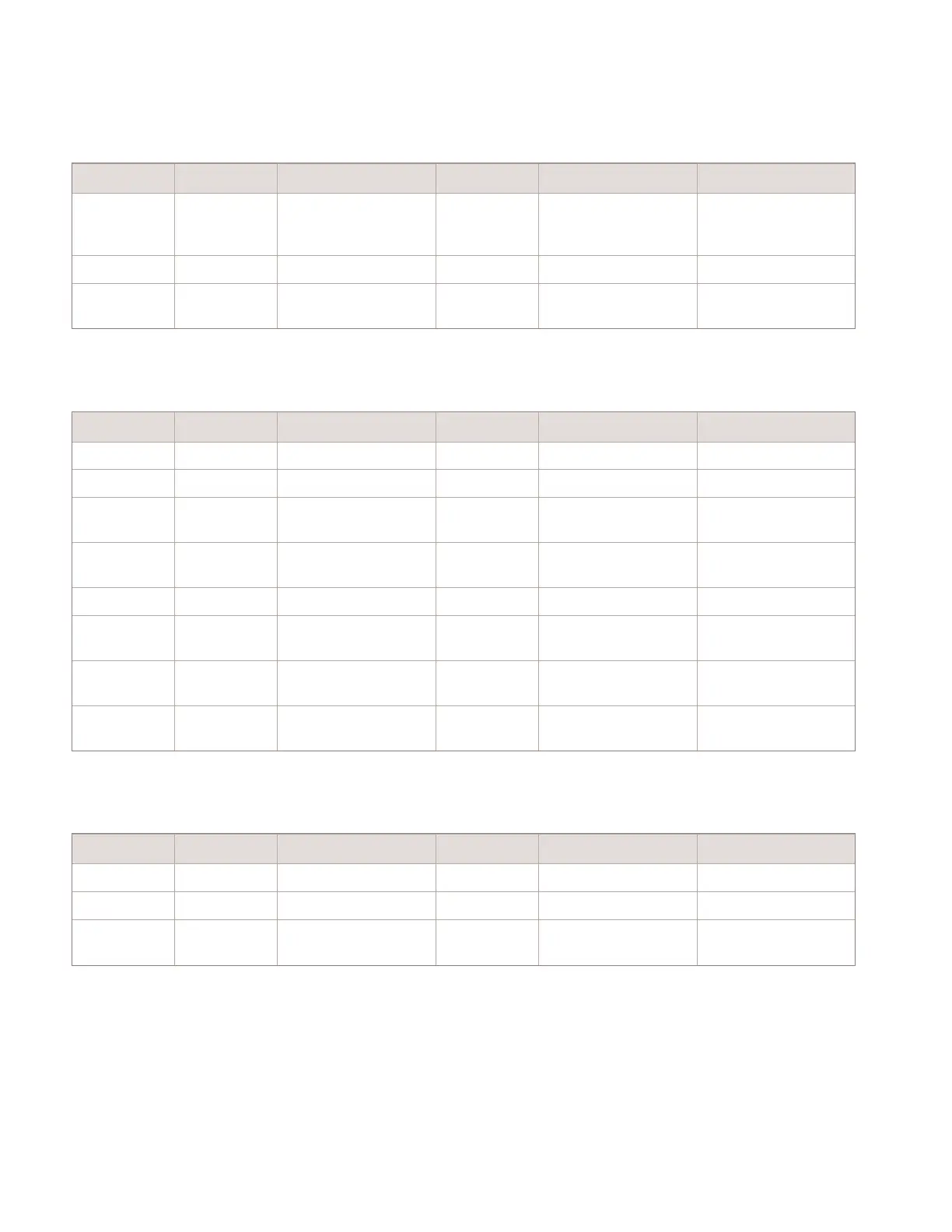
Table 7-4 Telnet / FTP Firewall rules for traffic between the 5620 SAM Server(s)
and the managed network (continued)
Protocol From port On To port On Notes
TCP Any Server(s) 21 Managed Network FTP requests (example:
STM, Accounting
Statistics, NE backups)
TCP 21 Managed Network Any Server(s) FTP responses
TCP > 1023 Managed Network > 1023 Server(s) Passive FTP ports for
data transfer
Table 7-5 SSH / SFTP / SCP Firewall rules for traffic between the 5620 SAM
Server(s) and the managed network
Protocol From port On To port On Notes
TCP Any Server(s) 22 Managed Network SAM SSH request
TCP 22 Managed Network Any Server(s) SAM SSH response
TCP Any Managed Network 22 Server(s) eNodeB and 1830 PSS
SFTP request
TCP 22 Server(s) Any Managed Network eNodeB and 1830 PSS
SFTP response
TCP > 32768 Server(s) 830 Managed Network SSH request for eNodeB
TCP 830 Managed Network > 32768 Server(s) SSH response for
eNodeB
TCP > 32768 Server(s) 830 Managed Network SSHv2 request for
MME
TCP 830 Managed Network > 32768 Server(s) SSHv2 response for
MME
Table 7-6 1830 Firewall rules for traffic between the 5620 SAM Server(s) and
the managed network
Protocol From port On To port On Notes
UDP Any 1830 69 Server(s) TFTP initiated by NE
UDP Any 1830 Any Server(s) TFTP transfer
UDP Any 1830 13528 Server(s) CORBA Notification
1830 OCS only
Security Firewall and NAT rules
....................................................................................................................................................................................................................................
....................................................................................................................................................................................................................................
7-18
5620 SAM
3HE-09809-AAAG-TQZZA 13.0 R7
Issue 1 December 2015

 Loading...
Loading...