7-3
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 7 ASA FirePOWER Module
About the ASA FirePOWER Module
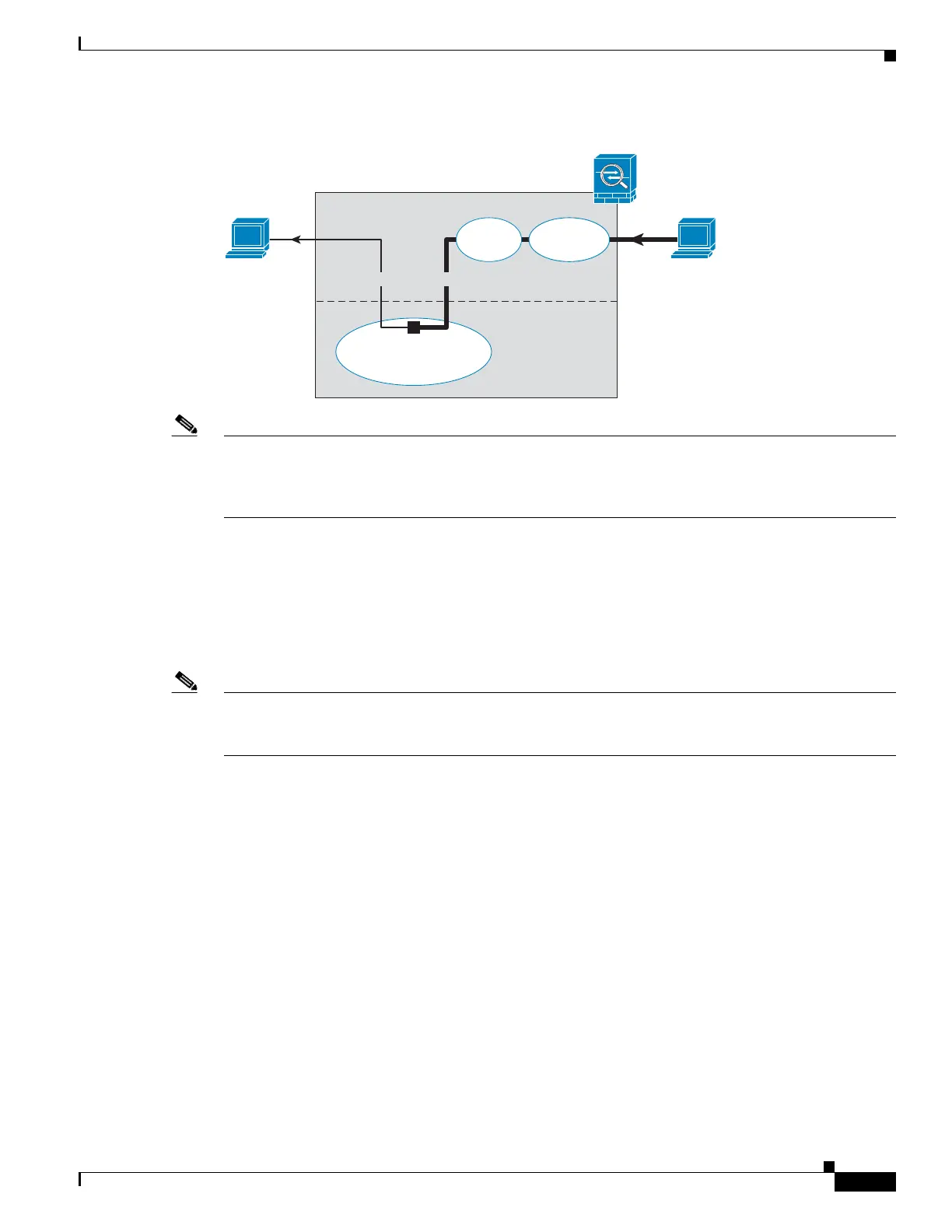
Figure 7-1 ASA FirePOWER Module Traffic Flow in the ASA
Note If you have a connection between hosts on two ASA interfaces, and the ASA FirePOWER service policy
is only configured for one of the interfaces, then all traffic between these hosts is sent to the ASA
FirePOWER module, including traffic originating on the non-ASA FirePOWER interface (because the
feature is bidirectional).
ASA FirePOWER Inline Tap Monitor-Only Mode
This mode sends a duplicate stream of traffic to the ASA FirePOWER module for monitoring purposes
only. The module applies the security policy to the traffic and lets you know what it would have done if
it were operating in inline mode; for example, traffic might be marked “would have dropped” in events.
You can use this information for traffic analysis and to help you decide if inline mode is desirable.
Note You cannot configure both inline tap monitor-only mode and normal inline mode at the same time on the
ASA. Only one type of security policy is allowed. In multiple context mode, you cannot configure inline
tap monitor-only mode for some contexts, and regular inline mode for others.
The following figure shows the traffic flow when operating in inline tap mode.
ASA
Main System
ASA FirePOWER
Diverted Traffic
ASA FirePOWER
inspection
VPN
Decryption
Firewall
Policy
Block
inside
outside
371444

 Loading...
Loading...



