45-2
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 45 Configuring Cisco Mobility Advantage
Information about the Cisco Mobility Advantage Proxy Feature
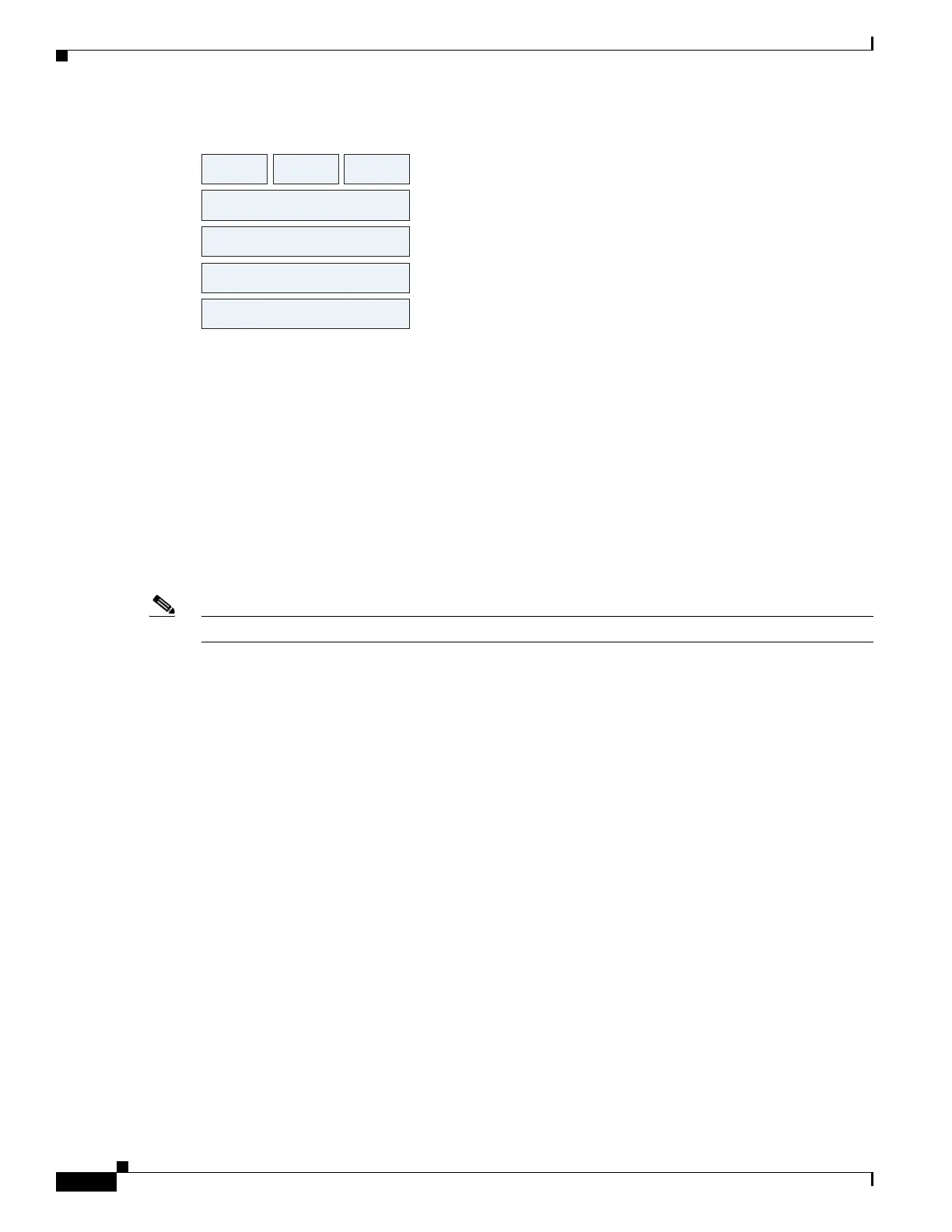
Figure 45-1 MMP Stack
The TCP/TLS default port is 5443. There are no embedded NAT or secondary connections.
Cisco UMA client and server communications can be proxied via TLS, which decrypts the data, passes
it to the inspect MMP module, and re-encrypt the data before forwarding it to the endpoint. The inspect
MMP module verifies the integrity of the MMP headers and passes the OML/HTTP to an appropriate
handler. The adaptive security appliance takes the following actions on the MMP headers and data:
• Verifies that client MMP headers are well-formed. Upon detection of a malformed header, the TCP
session is terminated.
• Verifies that client to server MMP header lengths are not exceeded. If an MMP header length is
exceeded (4096), then the TCP session is terminated.
• Verifies that client to server MMP content lengths are not exceeded. If an entity content length is
exceeded (4096), the TCP session is terminated.
Note 4096 is the value currently used in MMP implementations.
Because MMP headers and entities can be split across packets, the adaptive security appliance buffers
data to ensure consistent inspection. The SAPI (stream API) handles data buffering for pending
inspection opportunities. MMP header text is treated as case insensitive and a space is present between
header text and values. Reclaiming of MMP state is performed by monitoring the state of the TCP
connection.
Mobility Advantage Proxy Deployment Scenarios
Figure 45-2 and Figure 45-3 show the two deployment scenarios for the TLS proxy used by the Cisco
Mobility Advantage solution. In scenario 1 (the recommended deployment architecture), the adaptive
security appliance functions as both the firewall and TLS proxy. In scenario 2, the adaptive security
appliance functions as the TLS proxy only and works with an existing firewall. In both scenarios, the
clients connect from the Internet.
In the scenario 1 deployment, the adaptive security appliance is between a Cisco UMA client and a Cisco
UMA server. The Cisco UMA client is an executable that is downloaded to each smartphone. The Cisco
UMA client applications establishes a data connection, which is a TLS connection, to the corporate
Cisco UMA server. The adaptive security appliance intercepts the connections and inspects the data that
the client sends to the Cisco UMA server.
271645
MMP
TLS/SSL
TCP
OML HTTP etc.
IP

 Loading...
Loading...