Enabling Secure Networks
An integral part of the Secure Networks architecture from Enterasys,
the Matrix N-Series provides advanced security, priority and bandwidth
control mechanisms without compromising network performance. Secure
Networks leverages the distributed, flow-based visibility and advanced
policy-based control of the Matrix N-Series.
NetFlow Without Compromise
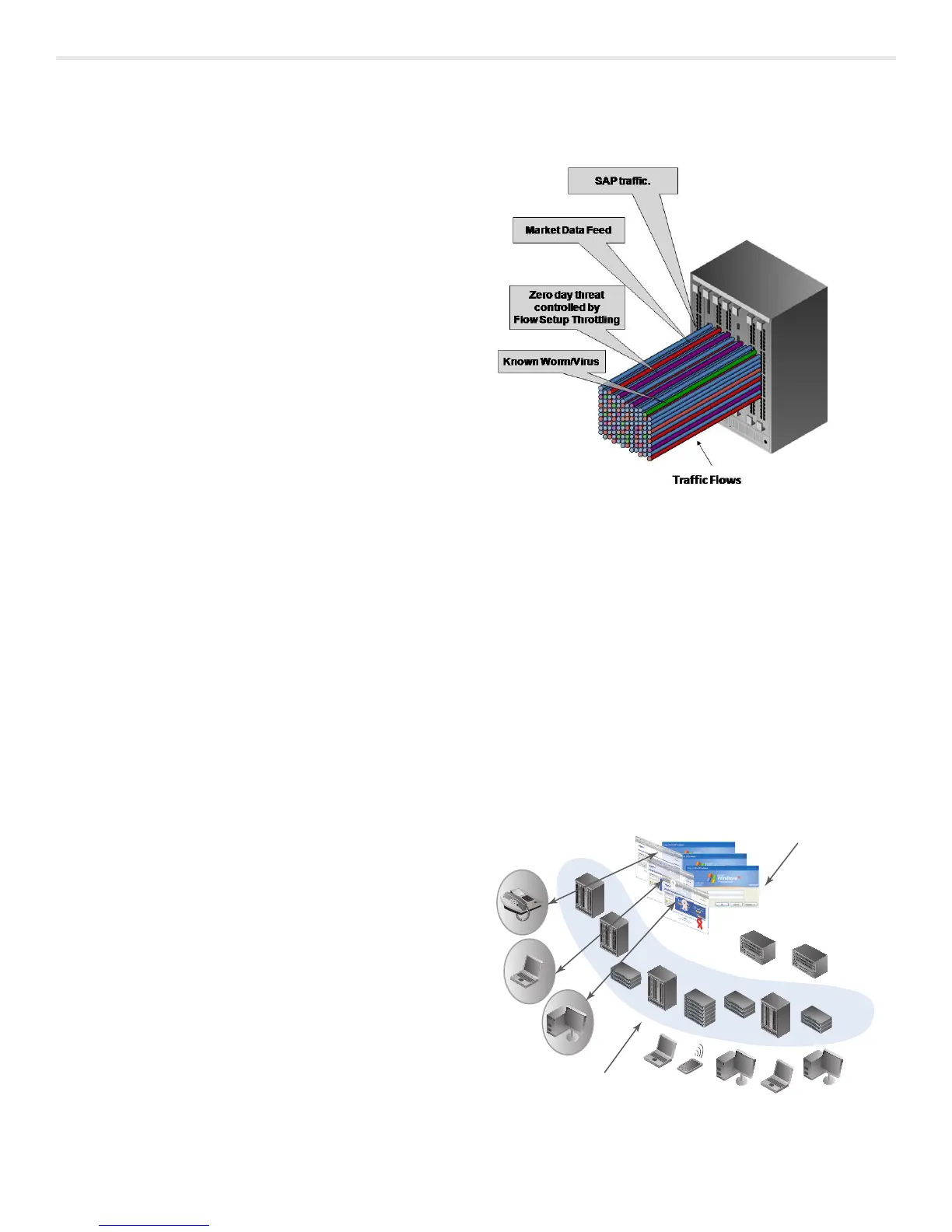
NetworkperformancemanagementandsecuritycapabilitiesviaNetFlow
areavailableoneveryMatrixN-SeriesDFEwithoutslowingdown
switching/routing performance or requiring the purchase of expensive
daughter cards for every blade. Enterasys tracks every packet in every
flow as opposed to competitor’s statistical sampling techniques.
The Matrix N-Series’ distributed, flow-based architecture allows for a
very granular level of visibility and control for each user and application
conversation, or flow, while simultaneously handling a large volume of
traffic. The distributed architecture enables each switch module in a
Matrix N-Series chassis to function independently of other modules and
eliminates single points of failure. Each chassis is managed as a single
systemusingasingleIPaddress.Thiscapabilityisuniqueintheindustry
and provides security and management automation.
Distributed Flow-Based Architecture
Inordertoensuregranularvisibilityandcontroloftrafcismaintained,
without sacrificing performance, the Matrix N-Series deploys a
distributed, flow-based architecture. This architecture ensures that when
a specific communications flow is being established between two end
points, the first packets in that communication are processed through
themultilayerclassicationengineintheswitch.Inthisprocess,the
role is identified, the applicable policies are determined, the frames are
inspected, and the action is determined. After the flow is identified, all
subsequent frames associated with that flow are automatically handled in
ASICswithoutanyfurtherprocessing.Ifthatowweretochangeinany
way, a new flow would be identified and new policies would be applied.
InthiswaytheMatrixN-Seriesisabletoapplyaverygranularlevelof
control to each flow without sacrificing performance.
Multi-User Authentication and Policy
Authenticationallowsenterpriseorganizationstocontrolnetworkaccess
andprovidesmobilitytousersanddevices.Itprovidesawaytoknowwho
or what is connected to the network and where this connection is at any
time. Matrix N-Series has unique, market leading capabilities regarding
thetypesofsimultaneousauthenticationmethods.DFEscansupport
multipleconcurrentauthenticationtechniques,including802.1X
authentication; MAC authentication, which is a way to authenticate
devicesonthenetworkusingtheMACaddress;andWeb-Based
authentication,alsoknownasPortWebAuthentication(PWA),wherea
user name and password are supplied through a browser. This capability
provides great flexibility to enterprises looking to implement access
control mechanisms across their infrastructure.
Distribution
Enables simplified user/device
identification within a
Secure Network™
User authenticated/access and
application control enforced here –
up to 1024 users per port
Edge
User physically
connected here
Features
Page 4

 Loading...
Loading...











