inter
PROTECTION
,---,
I I
MODULEA B
S
MODULEB
TASK
STACK
TASK
DATA
BLOCK
1
TASK
DATA
BLOCK
2
CODE
DATA
'I
I
I
I
I I
o
I I
1-
__
....1
MEMORY
I
L_
I
-
-
CPU
CODE
DATA
STACK
EXTRA
SEGMENT
REGISTERS
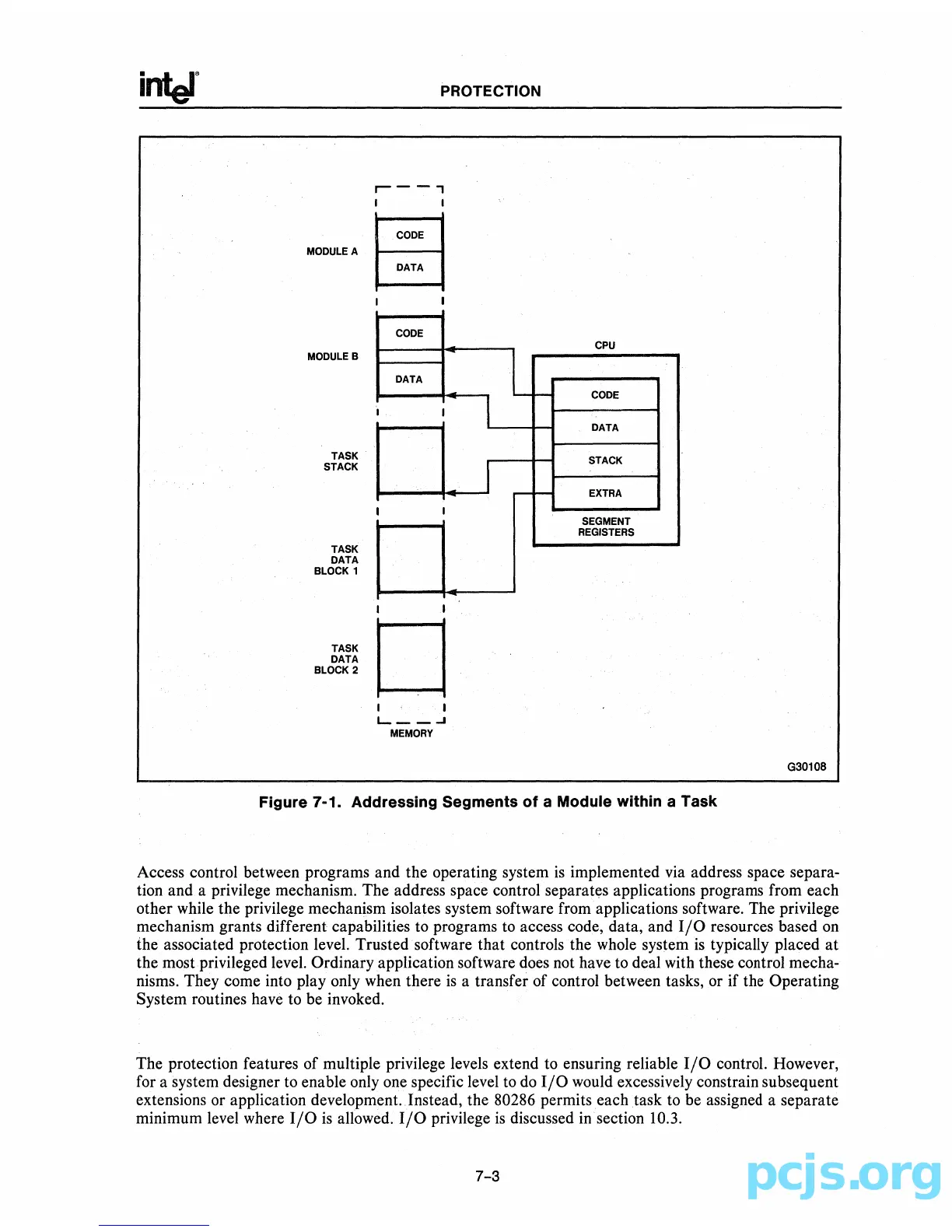
Figure 7-1. Addressing Segments of a Module within a Task
G3010B
Access control between programs and the operating system
is
implemented via address space separa-
tion and a privilege mechanism. The address space control separates applications programs from each
other while the privilege mechanism isolates system software from applications software. The privilege
mechanism grants different capabilities to programs to access code, data, and
I/O
resources based on
the associated protection level. Trusted software that controls the whole system
is
typically placed
at
the most privileged level. Ordinary application software does not have to deal with these control mecha-
nisms. They come into play only when there
is
a transfer of control between tasks, or if the Operating
System routines have to be invoked.
The protection features of multiple privilege levels extend to ensuring reliable
I/O
control. However,
for a system designer to enable only one specific level to do
I/O
would excessively constrain subsequent
extensions or application development. Instead, the 80286 permits each task to be assigned a separate
minimum level where
I/O
is
allowed.
I/O
privilege
is
discussed in section 10.3.
7-3
 Loading...
Loading...











