Juniper Networks SSG 320M and 350M Security Policy
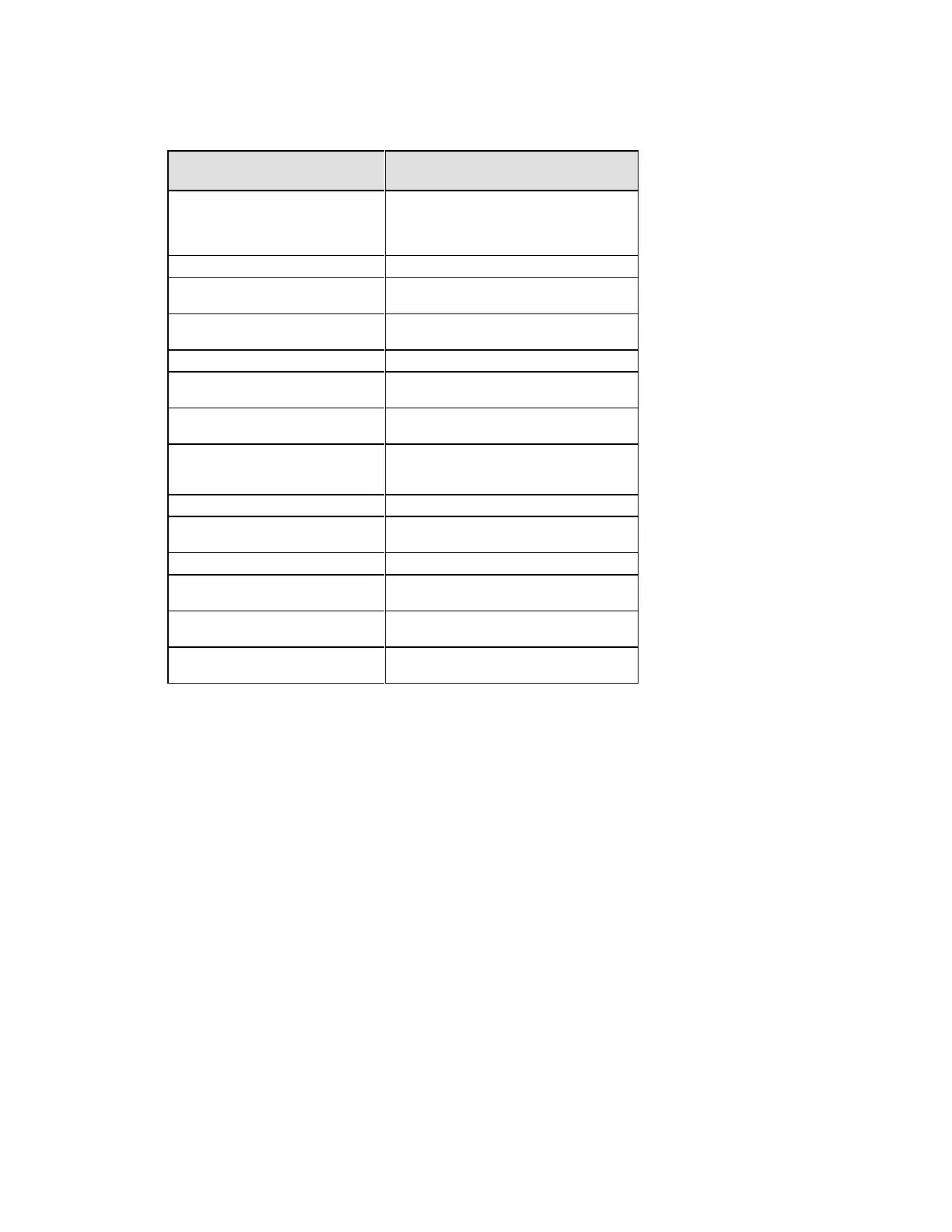
Table D: How Keys Are Generated
May be either entered directly at the CLI
by the administrator, or generated
internally via ANSI X9.31 RNG as a result
of IKE protocol exchanges.
Entered directly at the CLI by
administrator
Internally via ANSI X9.31 RNG, as a result
of IKE protocol exchanges
Entered directly at the CLI by
administrator
SSH Server/Host DSA Private Key
Internally via ANSI X9.31 RNG when DSA
key-pair is generated.
Internally via ANSI X9.31 RNG, as a result
of Diffie-Hellman key exchange during
SSH session establishment.
Entered directly at the CLI by
administrator
IKE RSA/DSA/ECDSA Private Key
Internally via ANSI X9.31 RNG
Diffie Hellman Private Key
Components
Initial generation via entropy gathered
from a variety of internal sources.
Entered directly at the CLI by
administrator
Mitigation of Other Attacks Policy
The module is not designed to mitigate against attacks which are outside of the scope of FIPS 140-2.
 Loading...
Loading...