Xerox Multi-Function Device Security Target
25
Copyright
2013 Xerox Corporation. All rights reserved.
4. Security Objectives
The purpose of the security objectives is to detail the planned response to a
security problem or threat. Threats can be directed against the TOE or the
security environment or both, therefore, the CC identifies two categories of
security objectives:
1. Security objectives for the TOE, and
2. Security objectives for the environment.
4.1. Security Objectives for the TOE
This section describes the security objectives that the TOE shall fulfill.
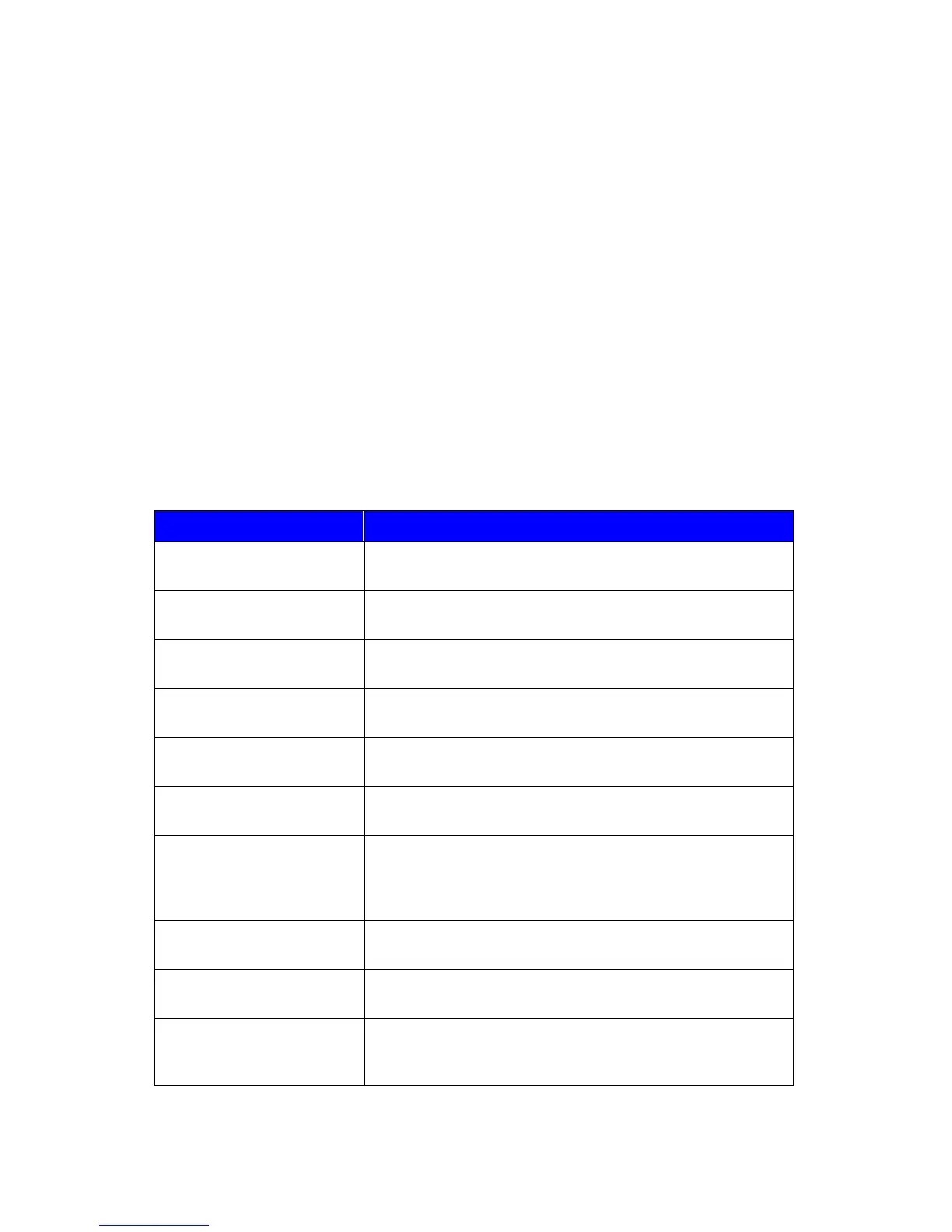
Table 16: Security objectives for the TOE
The TOE shall protect User Document Data from
unauthorized disclosure.
The TOE shall protect User Document Data from
unauthorized alteration.
The TOE shall protect User Function Data from
unauthorized alteration.
The TOE shall protect TSF Protected Data from
unauthorized alteration.
The TOE shall protect TSF Confidential Data from
unauthorized disclosure.
The TOE shall protect TSF Confidential Data from
unauthorized alteration.
The TOE shall require identification and authentication of
Users, and shall ensure that Users are authorized in
accordance with security policies before allowing them to
use the TOE.
The TOE shall manage the operation of external interfaces
in accordance with security policies.
The TOE shall provide procedures to self-verify executable
code in the TSF.
The TOE shall create and maintain a log of TOE use and
security-relevant events, and prevent its unauthorized
disclosure or alteration.

 Loading...
Loading...

















