67-2
Cisco ASA 5500 Series Configuration Guide using ASDM
OL-20339-01
Chapter 67 Clientless SSL VPN
Security Precautions
By default, the adaptive security appliance permits all portal traffic to all web resources (e.g., HTTPS,
CIFS, RDP, and plug-ins). The adaptive security appliance clientless service rewrites each URL to one
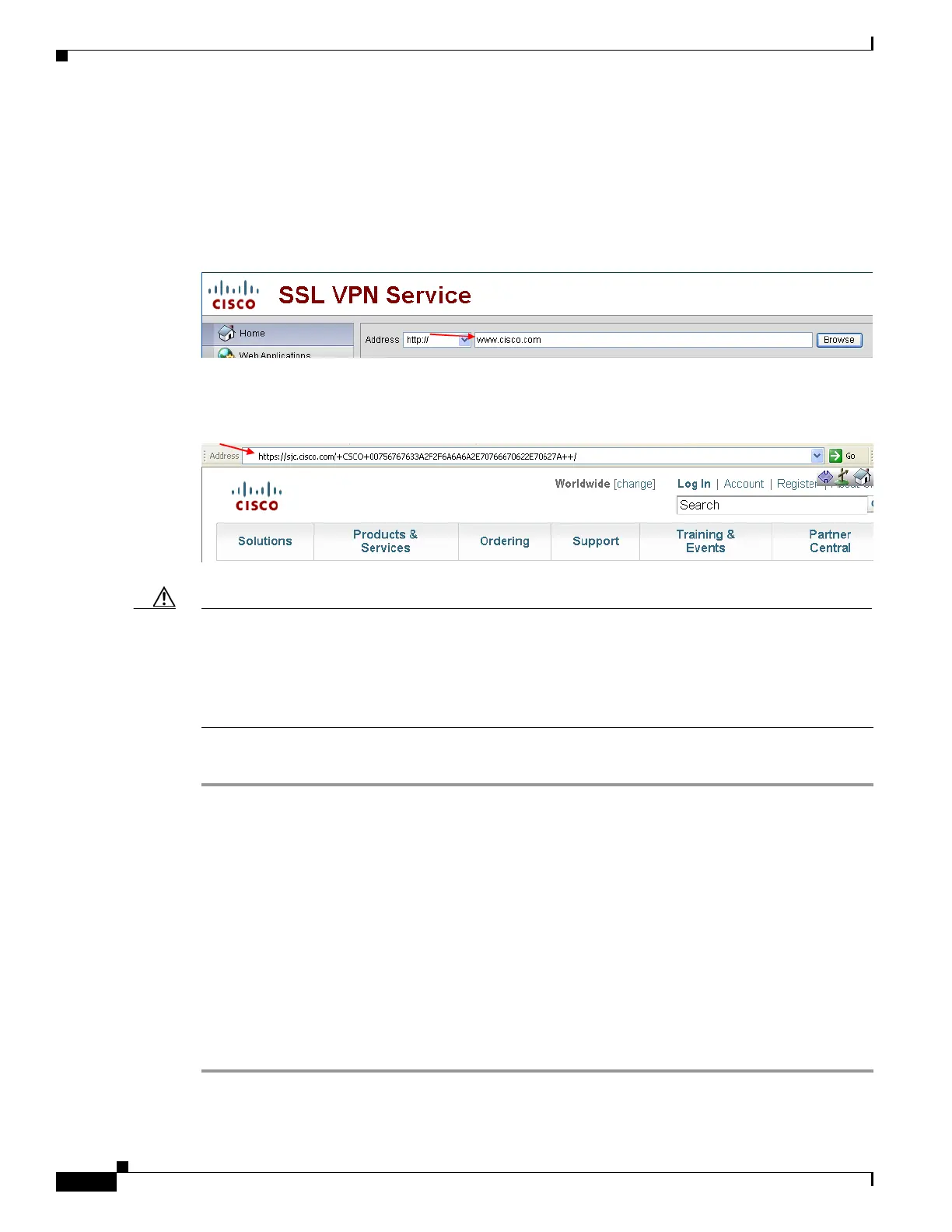
that is meaningful only to the adaptive security appliance; the user cannot use the rewritten URL
displayed on the page accessed to confirm that they are on the site they requested (see example Figures
67-1 and 67-2).
Figure 67-1 Example URL Typed by User
Figure 67-2 Same URL Rewritten by Security Appliance and displayed on the Browser Window
Caution To avoid placing users at risk, please assign a web ACL to the policies configured for clientless access
– group-policies, dynamic access policies, or both – to control traffic flows from the portal. For example,
without such an ACL, users could receive an authentication request from an outside fraudulent banking
or commerce site. Also, we recommend disabling URL Entry on these policies to prevent user confusion
over what is accessible. The procedure that follows steps you through the recommendations in this
statement.
We recommend that you do the following to minimize risks posed by clientless SSL VPN access:
Step 1 Configure a group policy for all users who need clientless SSL VPN access, and enable clientless SSL
VPN only for that group policy.
Step 2 With the group policy open, choose General > More Options > Web ACL and click Manage. Create a
web ACL to do one of the following: permit access only to specific targets within the private network,
permit access only to the private network, deny Internet access, or permit access only to reputable sites.
Assign the web ACL to any policies (group policies, dynamic access policies, or both) that you have
configured for clientless access. To assign a web ACL to a DAP, edit the DAP record, and select the web
ACL on the Network ACL Filters tab.
Step 3 Disable URL entry on the portal page, the page that opens upon the establishment of a browser-based
connection. To do so, click Disable next to URL Entry on both the group policy Portal frame and the
DAP Functions tab.
Step 4 Instruct users to enter external URLs in the native browser address field above the portal page or open a
separate browser window to visit external sites.

 Loading...
Loading...