3
In many cases, the connection type determines what attempts are made to authenticate and authorize
users. For example, a wireless connection or dial-in connection may require more stringent
credentials than a wired connection. For wired networks, unfortunately, Authorized Users,
Unauthorized Users, and Guests may have network access to the same equipment because no
authentication and authorization is being done. Uncontrolled access can cause problems – for
example, an Authorized Server with a security vulnerability can be exploited by an Unauthorized
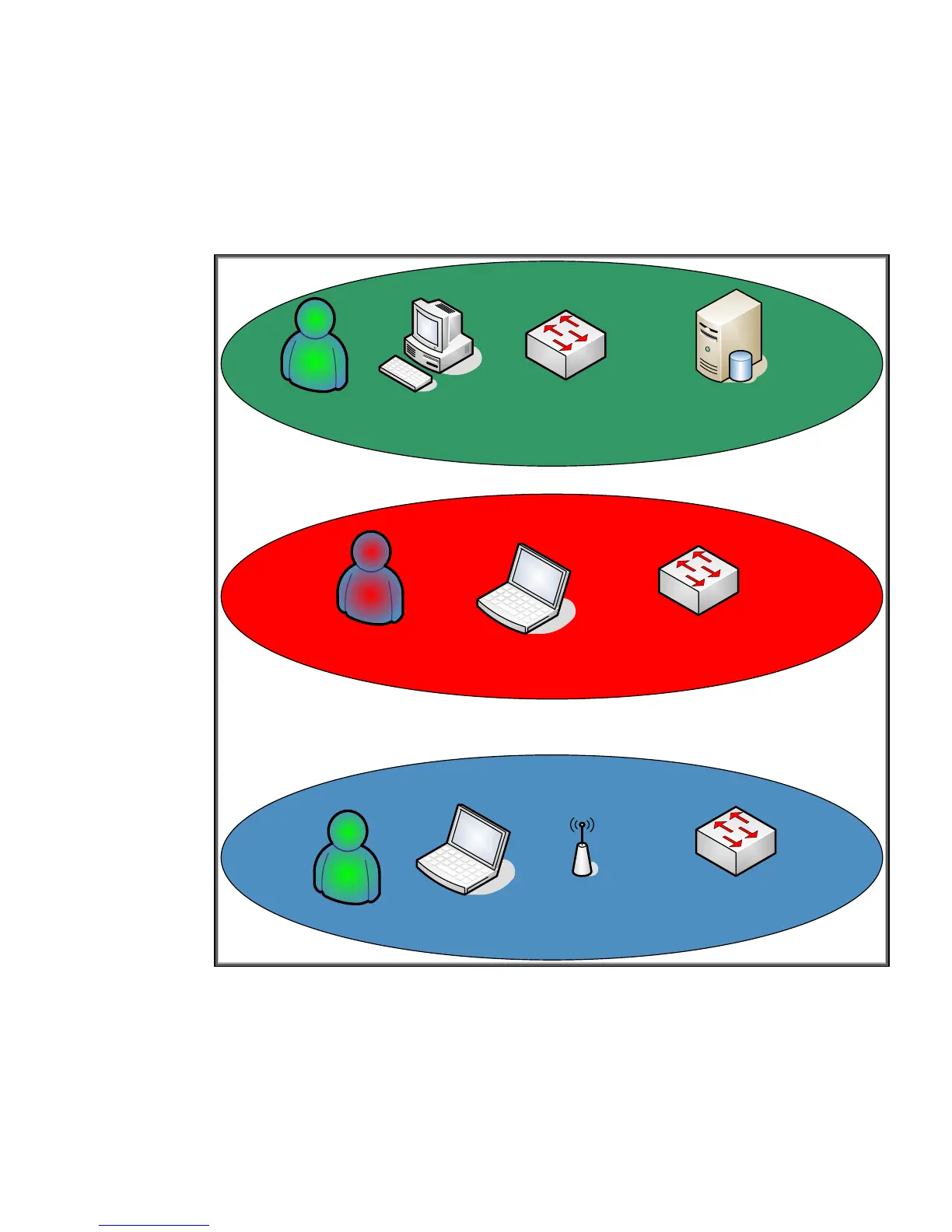
User. Instead, we would like the wired network architecture to help us isolate equipment to those
users that require access to it. Virtual LANs are a common way to accomplish this isolation. See
Figure 3 – Virtual LANs.
Unauthorized
Guest
Authorized
`
Ethernet Edge Switch
Ethernet Edge Switch
Access Point Ethernet Edge Switch
Authorized User’s Server
Figure 3 - Virtual LANs
In Figure 3, independent switches that are each responsible for a single VLAN are used. Each VLAN
is for a particular type of user. There is typically a one-to-one correspondence between a VLAN and
an IP Subnet. Inter-VLAN communication is routed.
There are a couple of problems with this approach: (1) it doesn’t really make sense to have an
Unauthorized User VLAN for wired connection and (2) an Unauthorized User can simply plug their
computer into the Authorized VLAN switch to circumvent security. It is also very inefficient to dedicate
one switch to one VLAN. We could use a single switch and create Port-Based VLANs – for example,

 Loading...
Loading...











