HP Inc.
HP LaserJet Enterprise MFP M527 Series,
Color LaserJet Enterprise MFP M577 Series, and
PageWide Enterprise Color MFP 586 Series
Firmware with Jetdirect Inside Security Target
Version: 2.0 Copyright © 2008-2016 by atsec information security corporation and HP Inc. Page 18 of 98
Last update: 2016-06-07 or its wholly owned subsidiaries
Windows Sign In (via Kerberos)
For successful remote authentication, Control Panel users must enter their username and password as
defined by the remote sign-in method.
All users must sign in before being presented with the home screen allowing access to Control Panel
applications. Prior to signing in, the TOE can be configured to display a Welcome message on which the
user must press “OK” before the user can access the sign-in screen. At the sign-in screen, the user may
get help on various MFP functions or select a sign-in method prior to signing in. The sign-in method
selections are:
Local Device Sign In:
o Administrator Access Code
o User Access Code
LDAP Sign In (if configured and enabled)
Windows Sign In (if configured and enabled)
When users sign in through the Control Panel, the TOE displays asterisks for each character of a PIN,
Access Code, or password typed to prevent onlookers from viewing another user's authentication data.
The TOE also contains a mechanism called Simplified Account Lockout that slows Control Panel
authentication attempts when multiple unsuccessful authentication attempts occur.
1.5.2.3.2 IPsec I&A
Client computers can connect to the TOE to submit print jobs and to manage the TOE. The TOE uses
IPsec to identify and mutually authenticate client computers that attempt to connect to the TOE.
The client computers that connect to the TOE are considered IPsec users and are classified as either
Network Client Computers or the Administrative Computer. The TOE uses IP addresses to identify these
users and X.509v3 certificates to authenticate the users. The IP address of a connecting client computer
must be defined in the TOE's IPsec/Firewall in order for the computer to be considered authorized to
access the TOE. Any client computer not defined in the TOE's IPsec/Firewall is considered unauthorized
and is blocked by the firewall from accessing the TOE.
The TOE uses IPsec/Firewall address templates, service templates, and rules to map IP addresses to
network service protocols. An address template contains one or more IP addresses. A service template
contains one or more allowed network service protocols. A rule contains a mapping of an address
template to a service template. Through the rules, an administrator determines the User Role of the client
computers (i.e., the administrator determines which client computer is the Administrative Computer and
which client computers are the Network Client Computers). In the evaluated configuration, the
IPsec/firewall only allows the Administrative Computer to connect to all interfaces supported by the TOE.
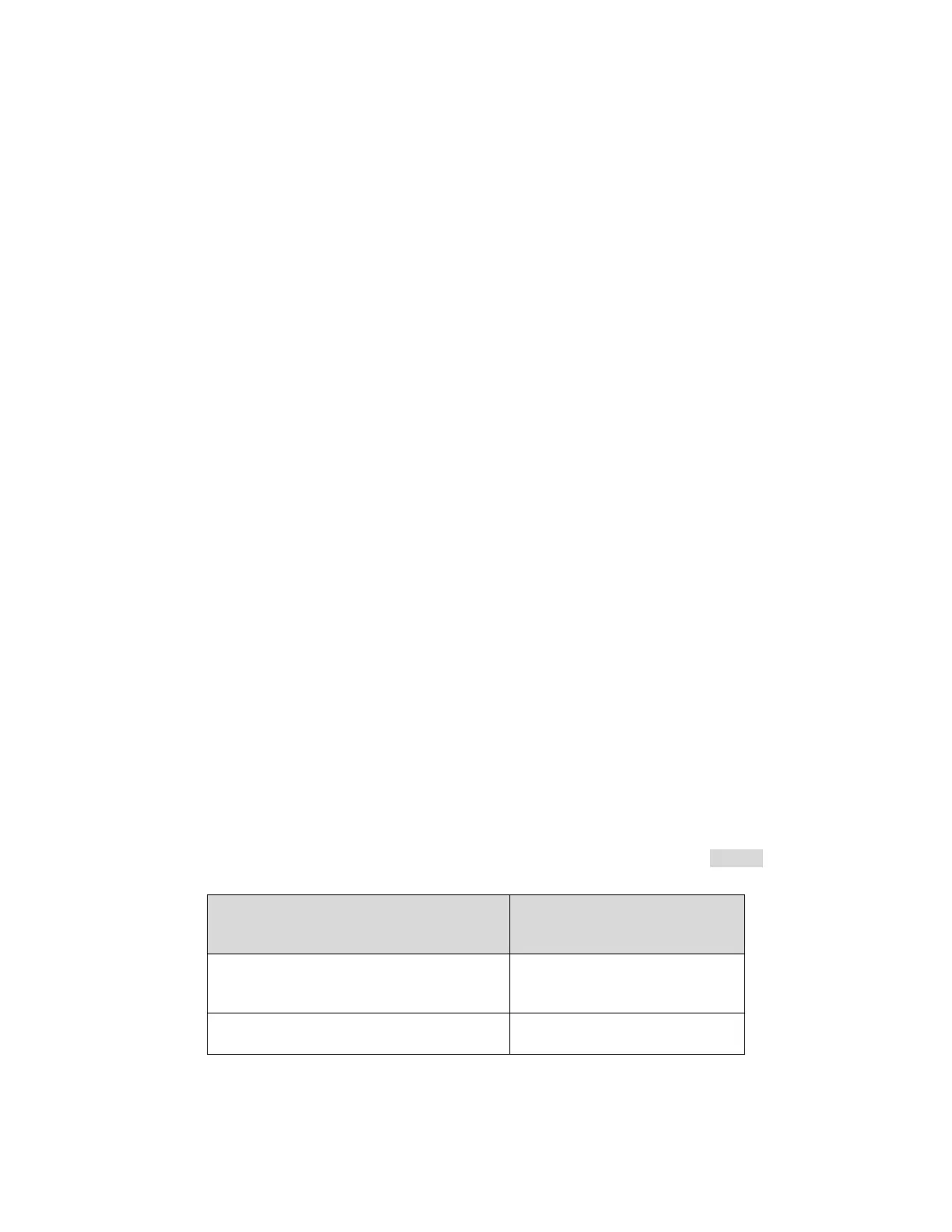
The Network Client Computers are limited to just the PJL Interface (TCP port 9100). Table 2 shows the
mapping of IPsec users to their allowed network protocols.
Allowed network protocol
access
Administrative Computer
(U.ADMINISTRATOR)
EWS (HTTP), OXPd, WS*,
SNMP, PJL
Network Client Computer (U.NORMAL)
 Loading...
Loading...











