-----------
Traffic/Security Filters
Filter Types and Operation
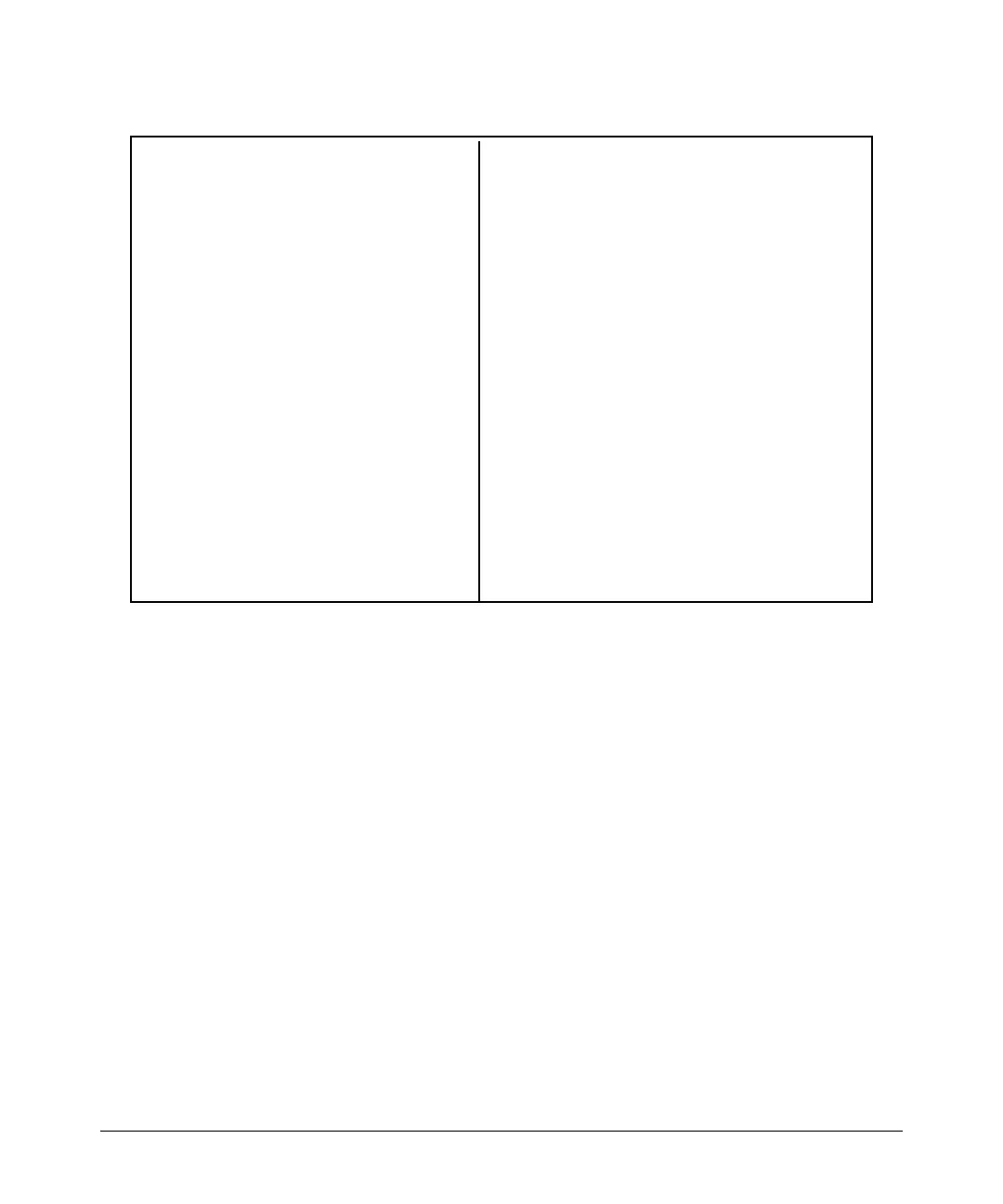
ProCurve(config)# show filter 4
Tr affic/Security Filters
F ilter Type : Source Port
S ource Port : 5
D est Port Type | Action
- -------- -------- - + -------
1 10/100 TX | Forward
2 1 0/100TX | Dro p
3 1 0/100TX | Dro p
4 1 0/100TX | Dro p
5 1 0/100TX | Dro p
6 1 0/100TX | Dro p
7 1 0/100TX | Dro p
8 1 0/100TX | Dro p
9 1 0/100TX | Dro p
1 0 1 0/100TX | Dro p
1 1 1 0/100TX | Dro p
1 2 1 0/100TX | Dro p
. . .
ProCurve(config)# show filter 24
Traffic /Security Filters
Filter Type : Source Port
Source Port : 10
Dest Port Ty pe | Action
------ --- --------- +
1 10/1 00TX | Drop
2 10/1 00TX | Drop
3 10/1 00TX | Drop
4 10/1 00TX | Drop
5 10/1 00TX | Drop
6 10/1 00TX | Drop
7 10/1 00TX | Forwa rd
8 10/1 00TX | Drop
9 10/1 00TX | Drop
10 10/1 00TX | Drop
11 10/1 00TX | Drop
12 10/1 00TX | Drop
. . .
The same command, using IDX 26, shows how traffic from the Internet is
handled.
9-12

 Loading...
Loading...











