Cookbook Configuration
103
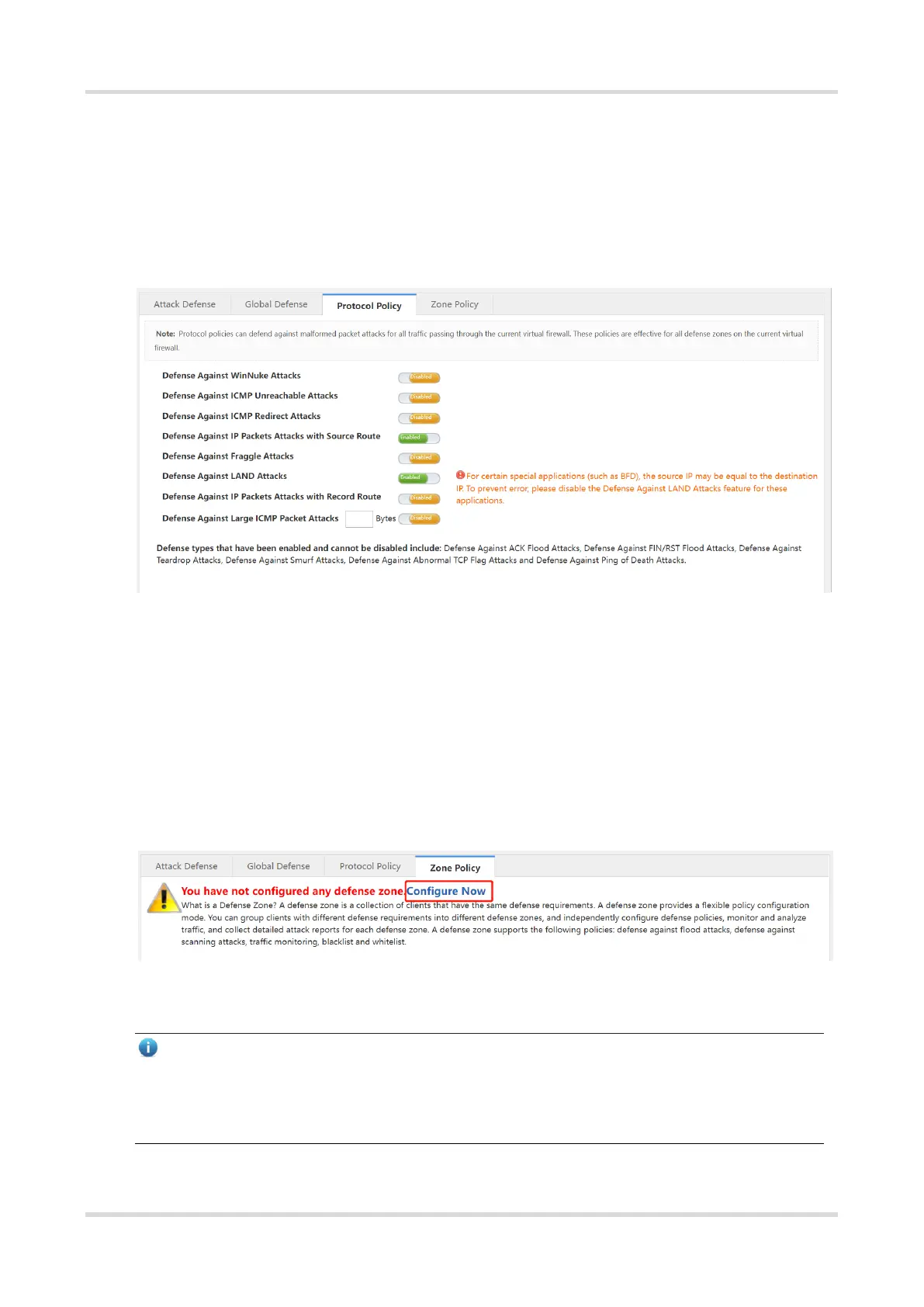
3. Protocol Policy
Protocol policies can defend against attacks for vulnerabilities of the protocol operating mechanism. The device
will filter protocol packets with attack characteristics if the corresponding protocol is enabled.
Procedure
(1) Choose Firewall > Attack Defense Config > Protocol Policy.
(2) Click to enable the defense policy as required to make the specified policy take effect.
4. Zone Policy
A defense zone is a collection of clients that have the same defense requirements. You can group clients with
different defense requirements into corresponding defense zones to defend the clients based on groups and
manage them separately. You can configure defense policies for specified zones respectively to defend the client
precisely.
Procedure
(1) Choose Firewall > Attack Defense Config > Zone Policy.
(2) Click Configure Now to enter the Config Wizard for Creating a New Defense Zone page.
(3) Enter the security zone name, description and the protected client range, and click Next.
Note
The protected client range supports a single IP address (example: 1.1.1.1), subnet bit length (example:
1.1.1.0/24), or subnet mask (example: 1.1.1.0/255.255.255.0). Enter the protected client range and click Add
to enter another range.

 Loading...
Loading...








