Cookbook Configuration
106
Note
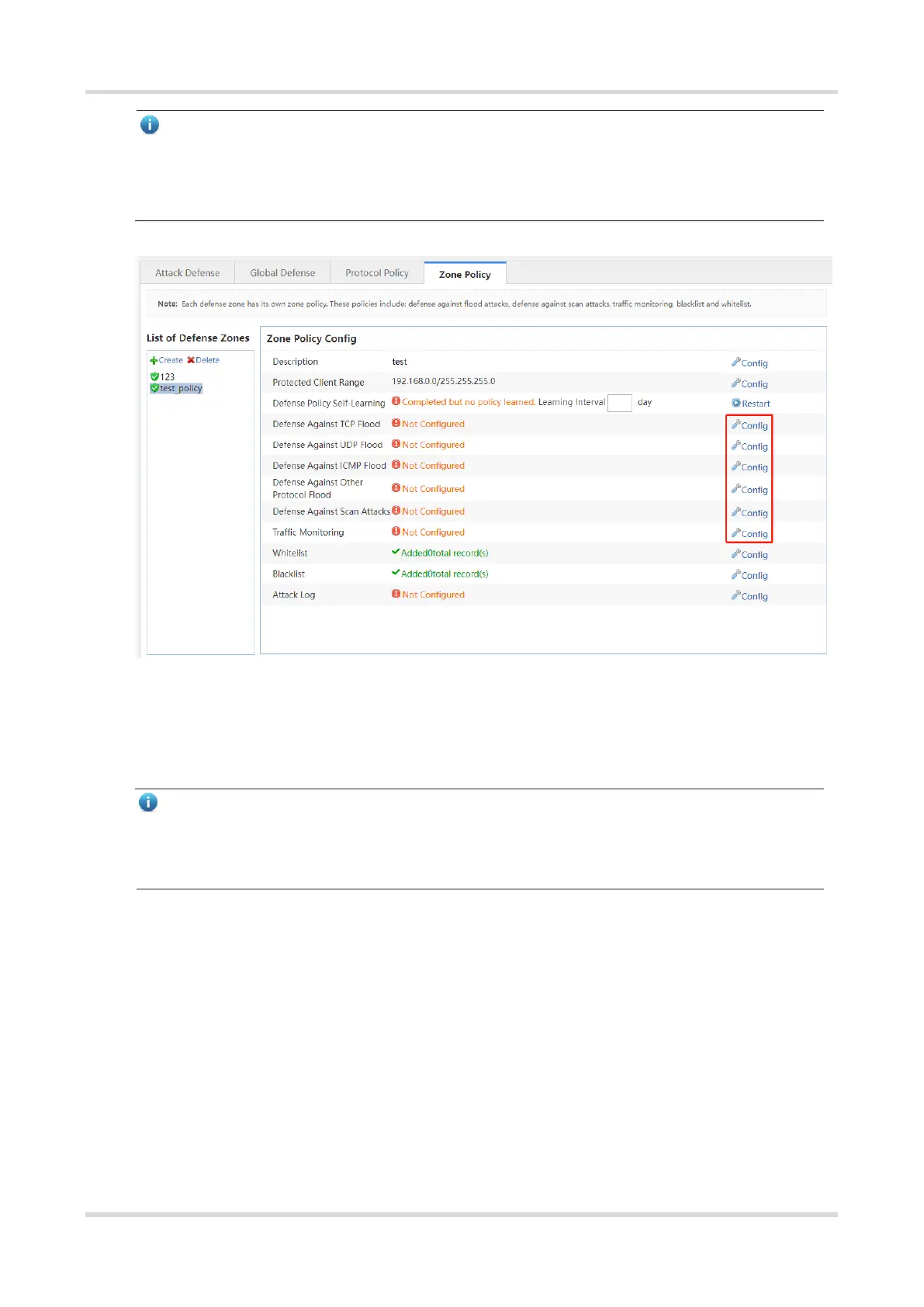
As the traffic monitoring function consumes some of device performance. You are advised to disable the traffic
monitoring function after the defense zone policy works smoothly to ensure that the device can achieve the
maximum service processing capacity.
(7) (Optional) For a trusted source IP address, you can add it to the whitelist to bypass the detection of the device
and the traffic of this source IP will not be affected. Click Config of the whitelist to access the Configure
Whitelist page, enter the source IP address, the subnet mask, select the protocol type and the designation
port range, and click Add.
Note
The whitelist is valid only for this defense zone.
The whitelist overrides the blacklist. If an IP address is added to a whitelist and a blacklist simultaneously,
the whitelist is valid.

 Loading...
Loading...








