NAT_S615
Entry ID: 109744660, V1.1, 08/2017
Siemens AG All rights reserved
2.8 Source NAT from VPN tunnel
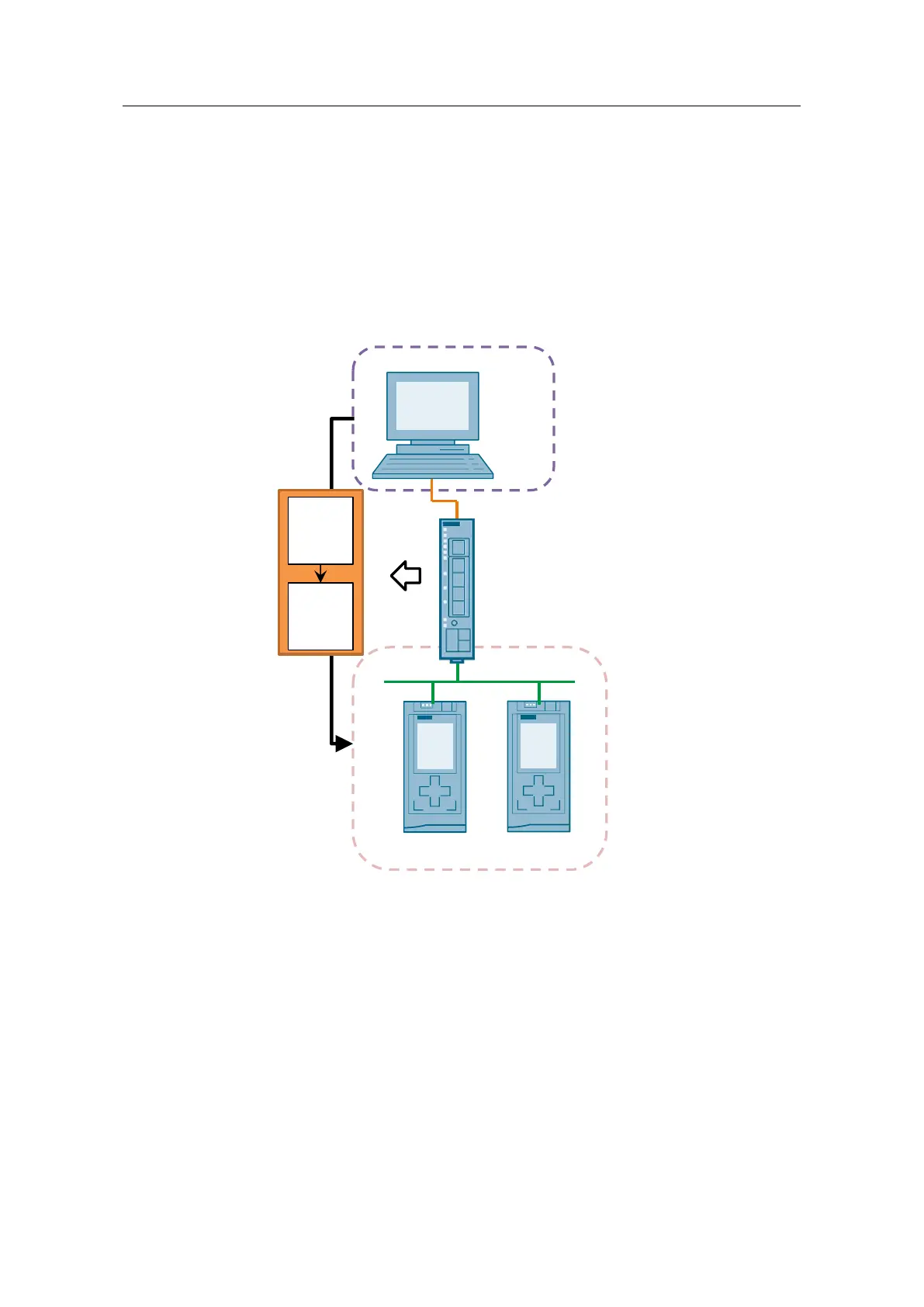
Starting situation
Protected by a VPN tunnel, the PC is to be able to use any functions on the S7
CPUs of an existing plant. No gateway is entered in the CPU and no change is to
be made to the hardware setting.
The destination port is not defined and can be changed when establishing the
connection.
Figure 2-15
Tunnel endpoint: 192.168.1.0/24
PC:
192.168.1.10
Gateway:
VPN Config
192.168.2.1
NAT Table
CPU: 192.168.2.20
Gateway: None
CPU: 192.168.2.30
Gateway: None
SRC IP:
Each
DST IP:
192.168.2.x
SRC IP:
192.168.2.1
DST IP:
192.168.2.x
VPN
VLAN1: 192.168.2.0/24
Requirements
An existing IPSec tunnel with the SCALANCE S615 as the tunnel endpoint is the
basis of this configuration. For example, the SOFTNET Security Client or another
SCALANCE S connected upstream to the PC can be the VPN partner.
For network separation, the SCALANCE S615 has VLANs with different network
IDs. As a result, the device has a separate IP address for each VLAN
(in this document: VLAN1: 192.168.2.1). Only VLAN1 is of interest to this
configuration, as this is where the VPN tunnel terminates.
To translate the message frames from the VPN tunnel to a different IP address, a
NAT table is additionally defined in the SCALANCE S615.

 Loading...
Loading...











