ESR series service routers.ESR-Series. User manual
Command Description
ip firewall screen suspicious-packets
udp-fragment
The given command enables the blocking of fragmented UDP packets.
ip firewall screen suspicious-packets
unknown-protocols
The given command enables the blocking of packets, with the protocol ID
contained in IP header equal to 137 and more.
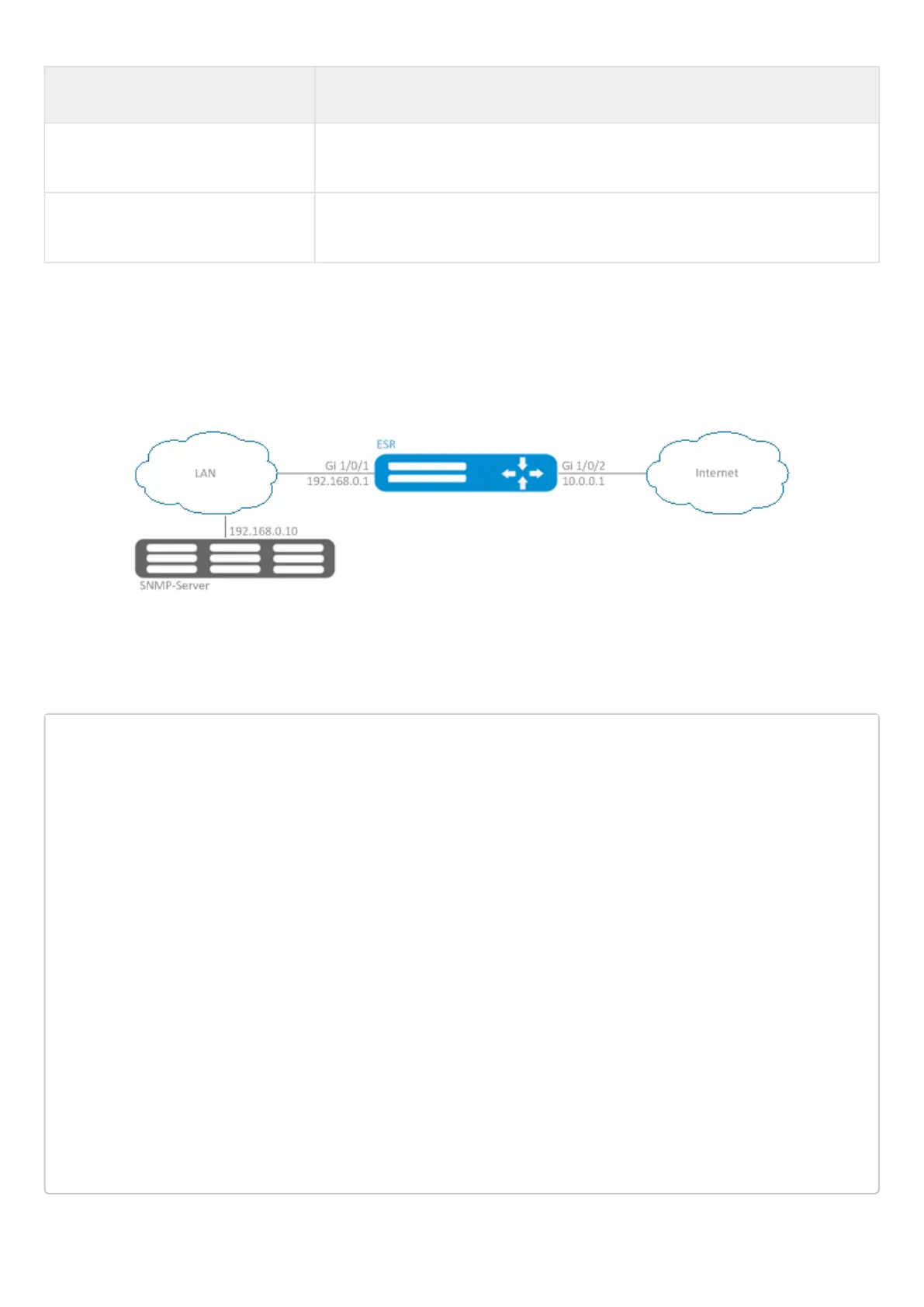
13.3.3 Configuration example of logging and protection against network attacks
Objective:
Protect LAN and ESR router from land, syn-flood, ICMP flood network attacks and configure the notification of
attacks by SNMP to SNMP server 192.168.0.10.
Solution:
First, configure interfaces and firewall (firewall configuration or its absence will not affect the operation of
network attacks protection):
esr(config)# security zone LAN
esr(config-zone)# exit
esr(config)# security zone WAN
esr(config-zone)# exit
esr(config)# security zone-pair LAN WAN
esr(config-zone-pair)# rule 100
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# ex
esr(config-zone-pair)# exit
esr(config)# security zone-pair WAN LAN
esr(config-zone-pair)# rule 100
esr(config-zone-pair-rule)# action permit
esr(config-zone-pair-rule)# enable
esr(config-zone-pair-rule)# exit
esr(config-zone-pair)# exit
esr(config)# interface gigabitethernet 1/0/1
esr(config-if-gi)# security-zone LAN
esr(config-if-gi)# ip address 192.168.0.1/24
esr(config-if-gi)# exit
esr(config)# interface gigabitethernet 1/0/2
esr(config-if-gi)# security-zone WAN
esr(config-if-gi)# ip address 10.0.0.1/24
esr(config-if-gi)# exit

 Loading...
Loading...