10
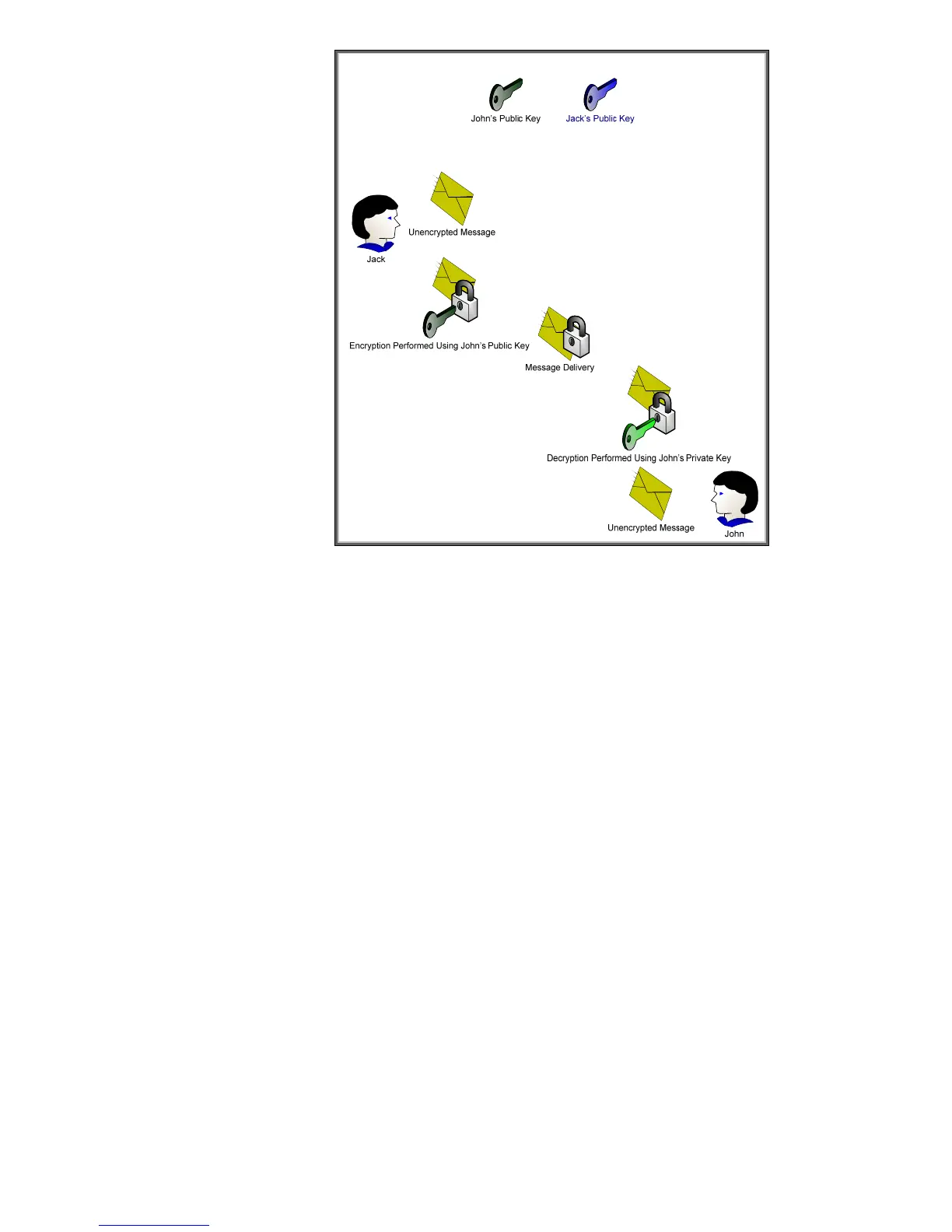
Figure 11 – Asymmetric Cryptography
Here we can see the difference between asymmetric and symmetric cryptography. One key can be
used for encryption and then the corresponding key can be used for decryption. It appears that
asymmetric cryptography has solved the key distribution issue; however there are two new attributes
usually associated with asymmetric cryptography
• It is slow
• It has a trust problem. How do I know that this is John’s public key and not someone
pretending to be John?
To solve the first problem, asymmetric cryptography is usually used to securely distribute symmetric
keys and sign hash codes. In short, what is actually being encrypted and decrypted is usually much
smaller than actual messages. This has the nice benefit of solving the key distribution issue with
symmetrical cryptography. So, in essence, symmetric keys are sent securely using asymmetric
cryptography and the actual messages themselves are protected using symmetric cryptography.
Cool! We get the flexibility of asymmetric cryptography and the speed of symmetric cryptography.
Now we only have to solve the trust problem.
In order to solve the trust problem, five things will need to be discussed:
• A certificate authority – a trusted third party that creates digital certificates from certificate
requests
• A certificate request – a public key associated with identity information that will serve as the
basic building block for a digital certificate that the certificate authority will create and sign.
• A digital certificate – a public key associated with identity information that is digitally signed
by the certificate authority.
• A digital signature – the hash of the digital certificate encrypted by the private key of the
certificate authority.
 Loading...
Loading...











