9
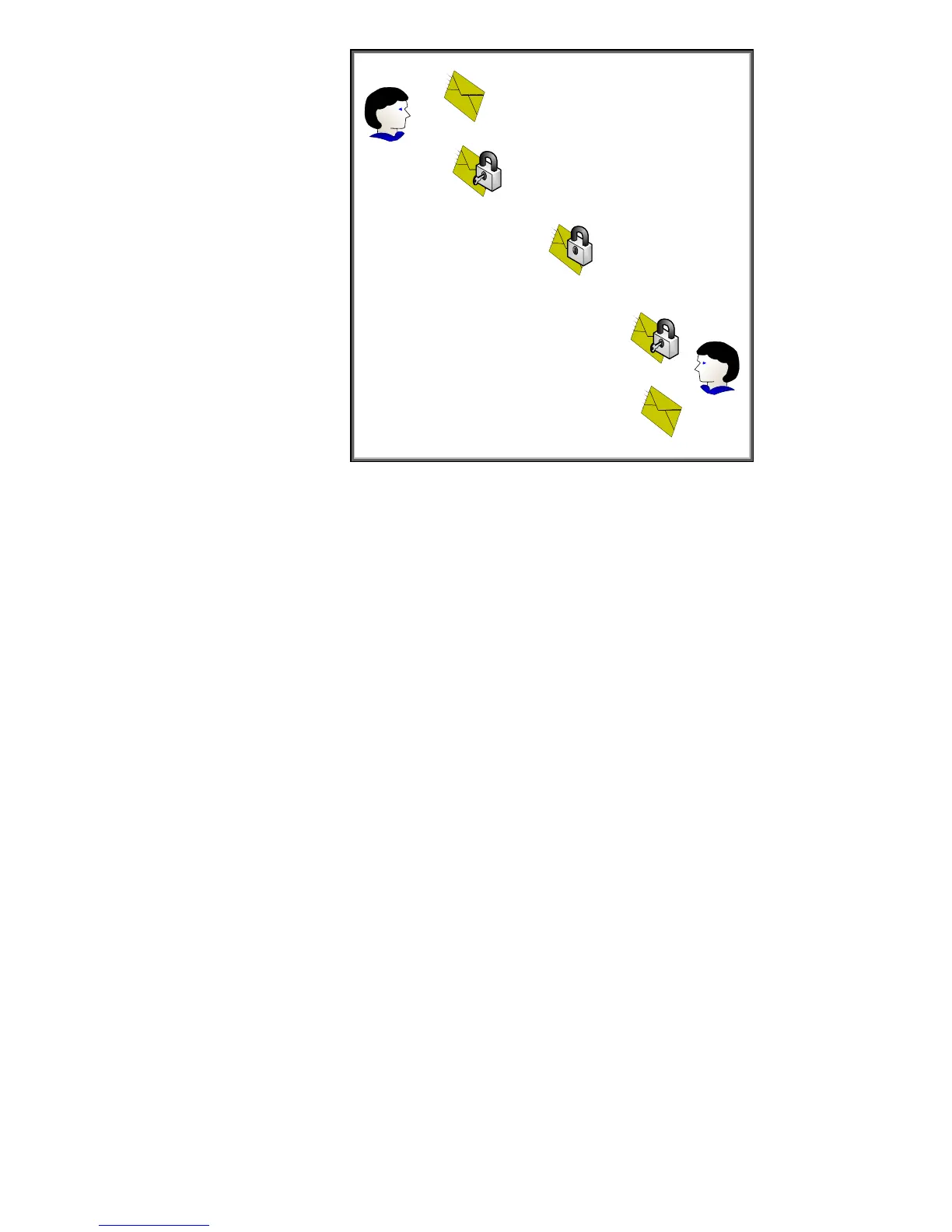
Message Delivery
User
Encryption Performed
User
Decryption Performed
Unencrypted Message
Unencrypted Message
Figure 10 – Symmetric Cryptography
In Figure 10, the confidentiality provided to the message is done via a single key. Because the same
key is used for encryption and decryption, this process is known as symmetric cryptography.
Symmetric cryptography commonly has two attributes associated with it:
• It performs well – it is fast and easy to implement
• It has a key distribution problem – how do you get the symmetric key to everyone that needs
it in a secure way?
Asymmetric cryptography is also available and functions very different than symmetric cryptography.
It has two keys – one Public and one Private. The private key is not shared with anyone. The Public
key is like a public telephone number. You can share it with everyone. Let’s look at Figure 11 –
Asymmetric Cryptography.

 Loading...
Loading...











