SSL Combined with Other Authentication Methods
Configuring Secure Sockets Layer Authentication 7-11
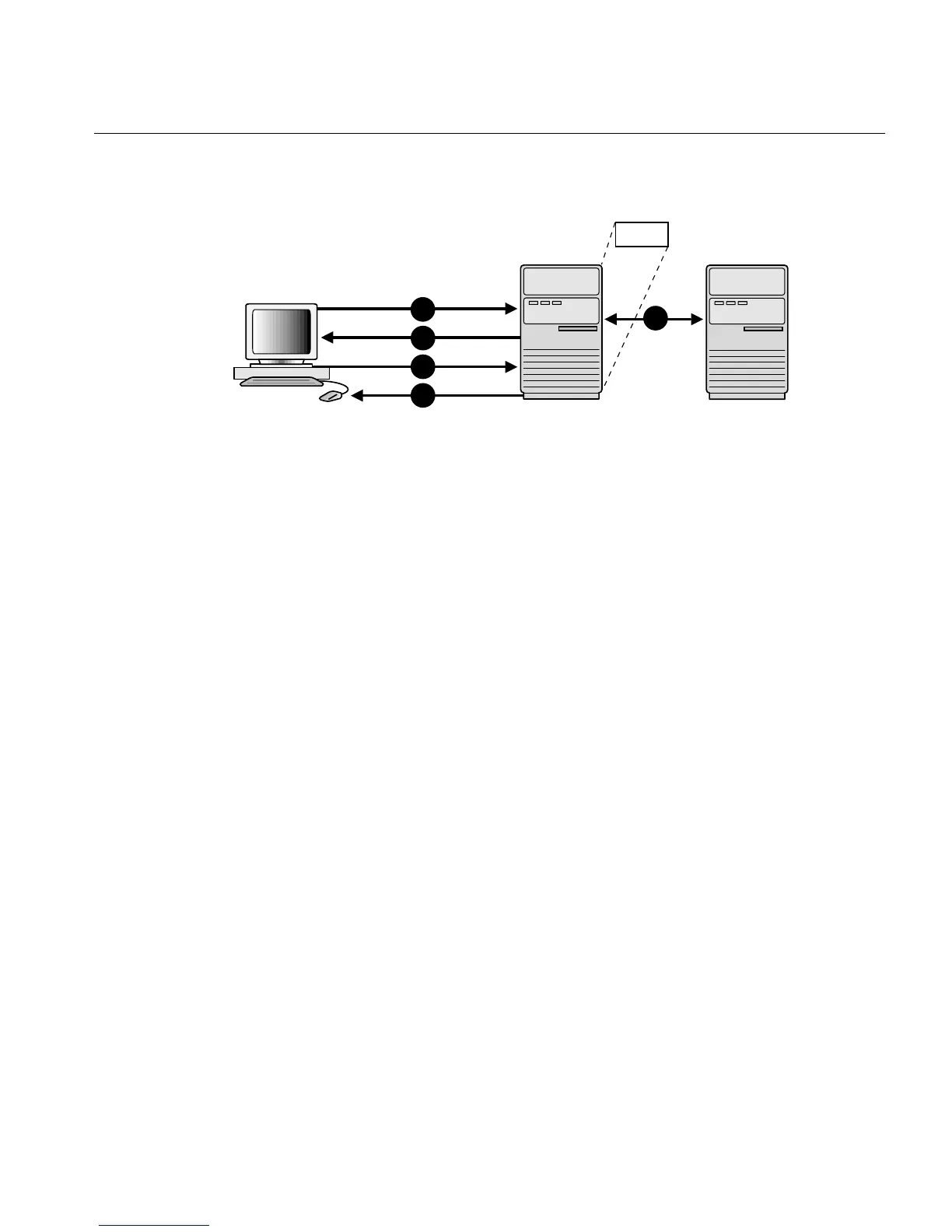
Figure 7–1 SSL in Relation to Other Authentication Methods
1.
The client seeks to connect to the Oracle database server.
2. SSL performs a handshake during which the server authenticates itself to the
client and both the client and server establish which cipher suite to use.
3. Once the SSL handshake is successfully completed, the user seeks access to the
database.
4. The Oracle database server authenticates the user with the authentication server
using a non-SSL authentication method such as Kerberos or RADIUS.
5. Upon validation by the authentication server, the Oracle database server grants
access and authorization to the user, and then the user can access the database
securely by using SSL.
See Also: "How SSL Works in an Oracle Environment: The SSL
Handshake" on page 7-4
2
3
5
1
Oracle
Client Oracle Server
Wallet
Authentication Server
4
 Loading...
Loading...