Configuration and operation
6.1 Security recommendations
CP 443-1 (EX30)
Manual, 03/2019, C79000-G8976-C255-05
45
● Make sure that all passwords are protected and inaccessible to unauthorized personnel.
See also the preceding section for information on this.
● Do not use one password for different users and systems.
Protocols
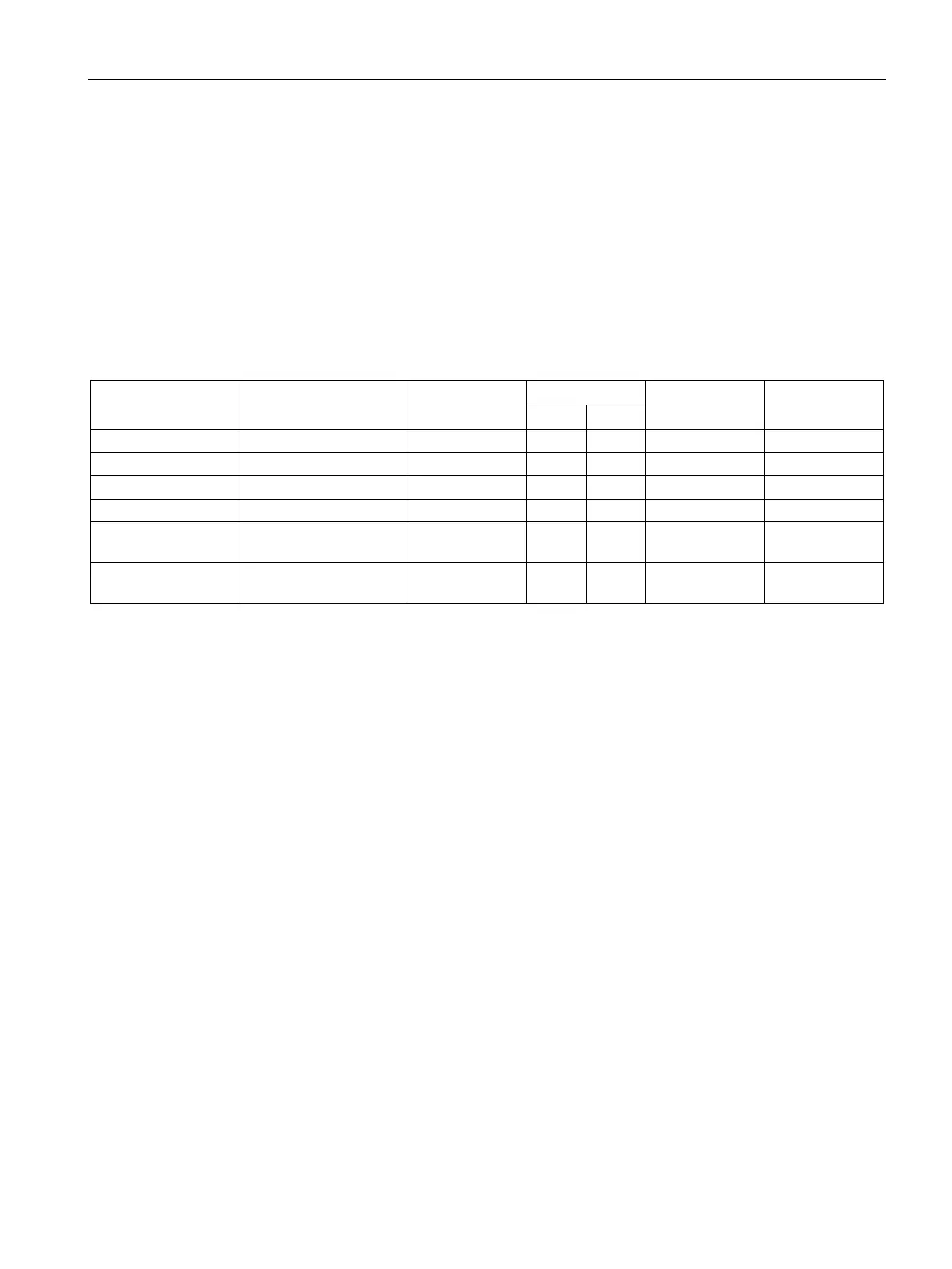
List of available protocols
The following is a list of all available protocols and their ports through which the device can
be accessed.
UDP/161 Open ✓ -- No No
UDP/34964 Open -- -- No No
UDP/49152-65535 Open -- -- No No
Explanation for table:
●
Protocols that the device supports.
●
Port number assigned to the protocol.
●
– Open
The port is open at the start of the configuration.
– Closed
The port is closed at the start of the configuration.
●
– ✓
The port can be configured.
– --
The port cannot be configured

 Loading...
Loading...











