The candidate image is not installed in the non
‑
secure image primary slot in the case of the following errors:
• Version dependency failure: The version of the non‑secure image is non‑consistent with the version of the
secure image.
The candidate image is not installed in the non
‑
secure image primary slot and is erased from the non
‑
secure
image secondary slot in the case of the following errors:
• Image size not consistent
• Flash reading errors (double ECC errors)
• Version check failure: The image version is lower than the previous valid image installed.
• Image signature failure: The image is not authentic.
The candidate image is not installed in the non
‑
secure image primary slot and TOE is resetting:
• A Flash writing or erasing error may be reported by the Flash driver used by the application to write data in
the non
‑
secure image primary slot area.
PSA API interface
The PSA API interfaces the secure services hosted in the secure application ROT. These API are used (or
called) by the Non‑secure world, but can also be called by the secure application ROT(secure services running
in secure domain with unprivileged rights), it provides a programmatic interface to trigger secure functionalities
running in secure domain with privileged rights. The integrator calls these C APIs and builds a completely
secure application by compiling the TOE source code with application RoT code. The detailed parameters,
actions, and error messages are described in the PSA developer APIs [PSA_ST_API], [PSA_CRYPTO_API], and
[PSA_ATTESTATION_API].
The non‑secure application interacts with the secure application via the standard PSA APIs as described in the
Open Source documents [PSA_ST_API], [PSA_CRYPTO_API], and [PSA_ATTESTATION_API] which describe
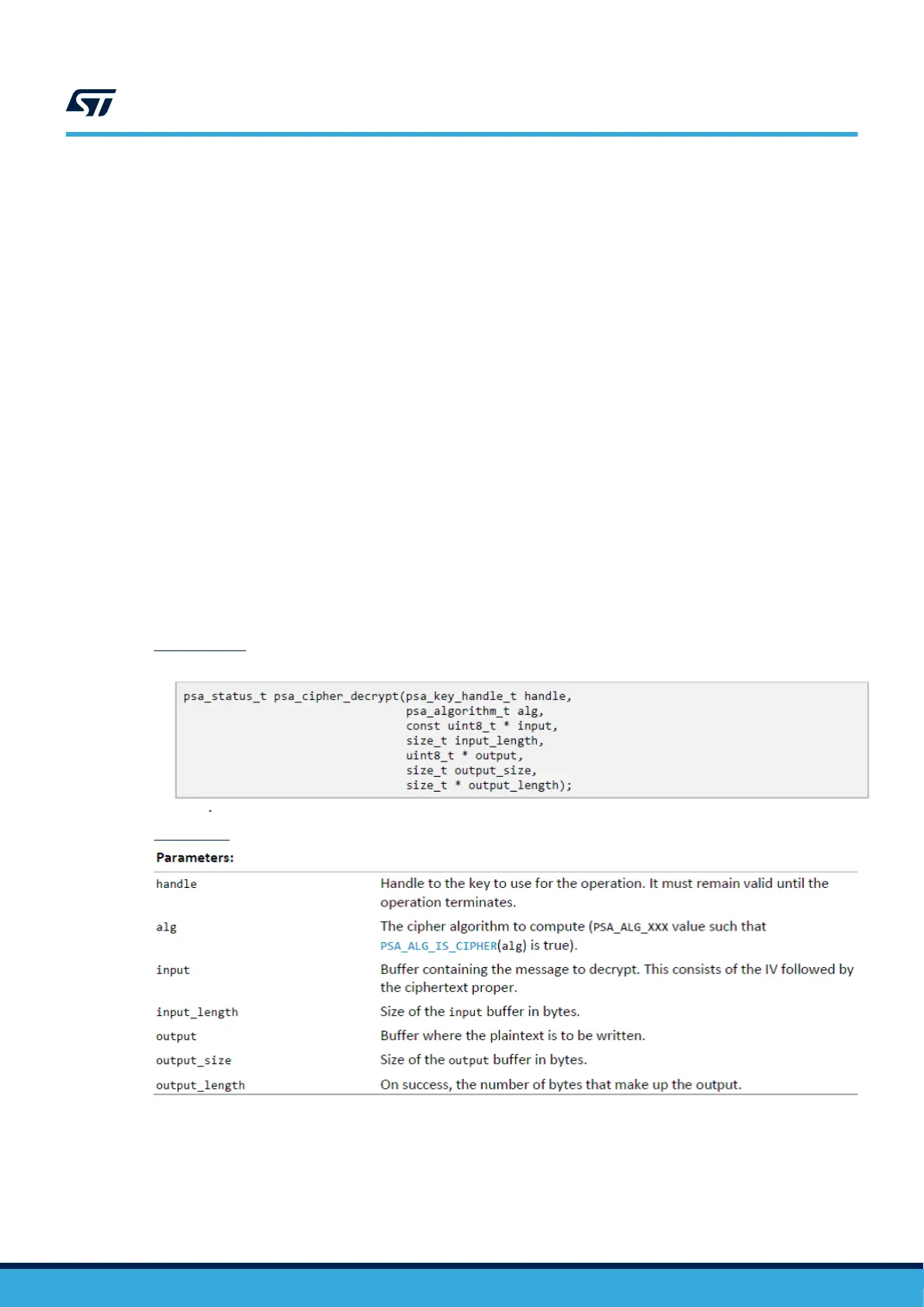
each PSA API. As an example, psa_cipher_decrypt API is illustrated hereafter:
Method of use:
• Call the following function.
Parameters:
UM2852
Operational guidance for the integrator role
UM2852 - Rev 1
page 18/27

 Loading...
Loading...