Configure Anti-Virus Settings
When anti-virus software runs an automated scan on a heavily utilized Avigilon NVR or workstation, it may
prevent video data from being written. Some anti-virus software packages are equipped with live process
scanning and incorporated firewalls. These features may cause communication failures between cameras
and NVRs or between NVRs and clients.
You may need to set up exceptions in the anti-virus software running on NVRs, workstations or clients within
the ACC system. For more information on how to exclude locations and applications from being scanned,
see your anti-virus software manual.
Preventing Data Write Issues
To ensure the anti-virus software does not interfere with the ACC software's ability to write video data and
other important files, exclude the following locations from being scanned:
AvigilonData
Located on each of the Primary and Secondary Data Volumes.*
AvigilonConfig
Located on each of the Config Volumes.*
Avigilon Program Files
Located at C:\Program Files\Avigilon.
*Do not use the C drive or an OSdrive for these volumes. To see which drives are configured as the Primary
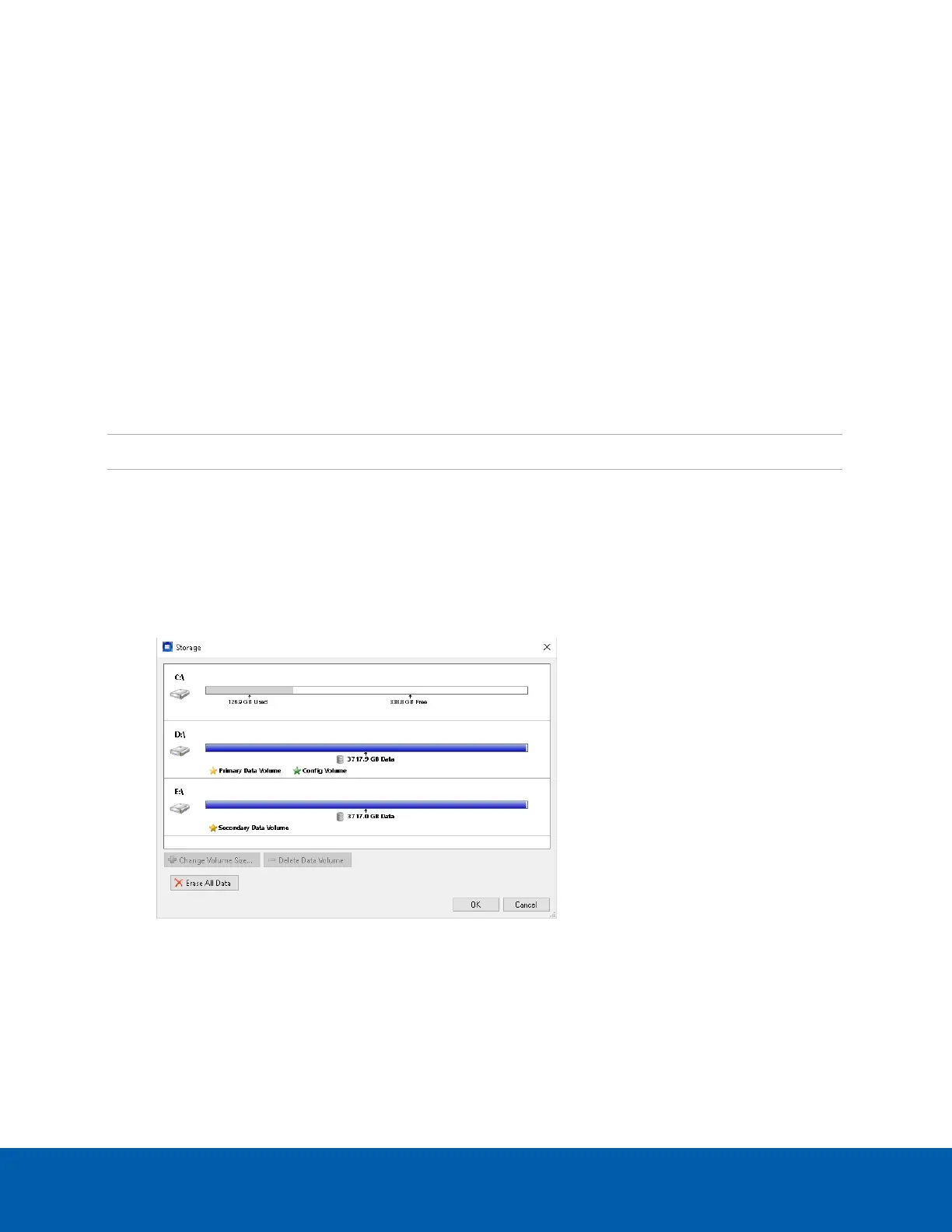
and Secondary Data Volumes and Config Volumes, use the ACC Admin Tool.
l In the Admin Tool, click Settings >Storage.
The Primary and Secondary Data Volumes and Config Volumes are displayed.
Preventing Network Communication Failure
To prevent communication failure, exclude the following from having their network traffic scanned or
analyzed:
Configure Anti-Virus Settings 7
 Loading...
Loading...