11-21
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 11 Service Policy Using the Modular Policy Framework
History for Service Policies
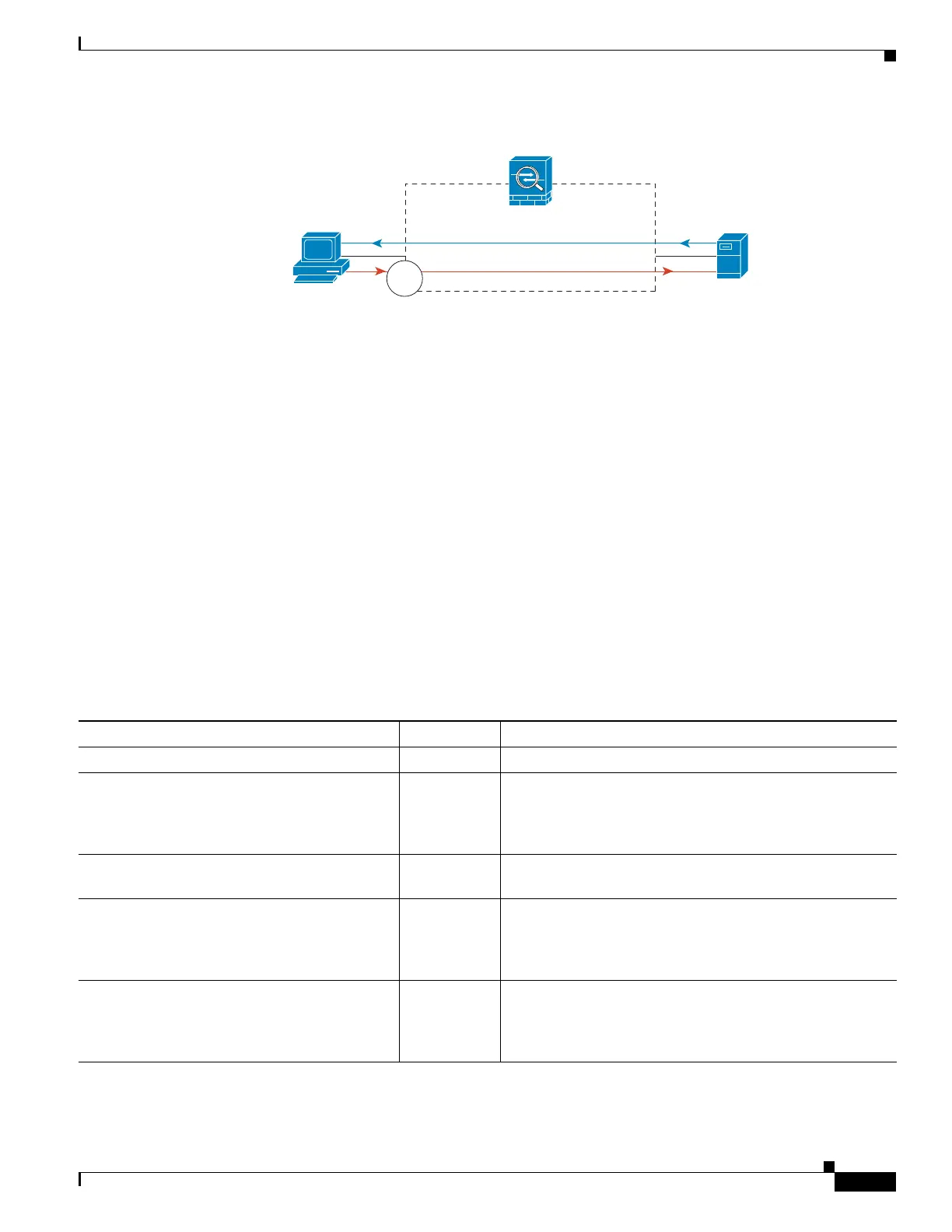
Figure 11-4 HTTP Inspection with NAT
See the following commands for this example:
hostname(config)# object network obj-192.168.1.1
hostname(config-network-object)# host 192.168.1.1
hostname(config-network-object)# nat (VM1,outside) static 209.165.200.225
hostname(config)# access-list http_client extended permit tcp host 192.168.1.1 any eq 80
hostname(config)# class-map http_client
hostname(config-cmap)# match access-list http_client
hostname(config)# policy-map http_client
hostname(config-pmap)# class http_client
hostname(config-pmap-c)# inspect http
hostname(config)# service-policy http_client interface inside
History for Service Policies
inside outside
Host
Real IP: 192.168.1.1
Mapped IP: 209.165.200.225
Server
209.165.201.1
port 80
insp.
Security
appliance
143416
Feature Name Releases Description
Modular Policy Framework 7.0(1) Modular Policy Framework was introduced.
Management class map for use with RADIUS
accounting traffic
7.2(1) The management class map was introduced for use with
RADIUS accounting traffic. The following commands were
introduced: class-map type management, and inspect
radius-accounting.
Inspection policy maps 7.2(1) The inspection policy map was introduced. The following
command was introduced: class-map type inspect.
Regular expressions and policy maps 7.2(1) Regular expressions and policy maps were introduced to be
used under inspection policy maps. The following
commands were introduced: class-map type regex, regex,
match regex.
Match any for inspection policy maps 8.0(2) The match any keyword was introduced for use with
inspection policy maps: traffic can match one or more
criteria to match the class map. Formerly, only match all
was available.

 Loading...
Loading...


















