7. Key Management
Key management is a critical component of a security product. A risk analysis will
determine the strength of cryptographic algorithm and associated key sizes and lifetimes
required to protect customer data.
7.1. Key management schema
Refer to the Security Worlds chapter in the User Guide for a description of the Security
World infrastructure available for managing the secure life-cycle of cryptographic keys.
See Security World Access Control Architecture for a description of the different keys
available to protect application keys.
7.2. Security World security strengths
Security strength is represented by a number associated with the amount of work (that
is, the number of guesses/operations) that is required to break a cryptographic algorithm
or system. The security strength is specified in bits and is a specific value from the set
{80, 96, 112, 128, 192, 256} e.g. a security strength of 112 bits would require on average
2
(112-1)
operations to brute force the algorithm or system.
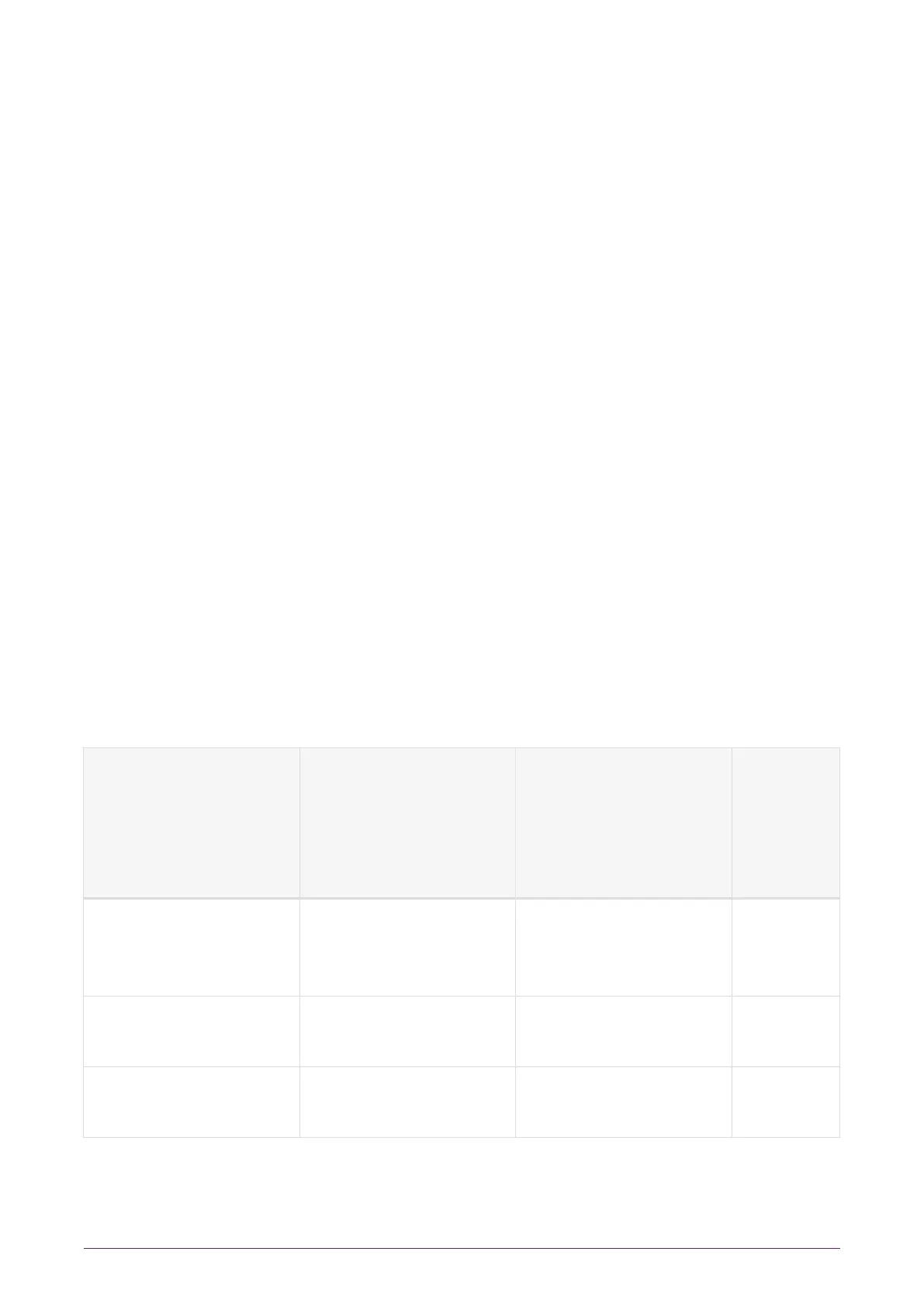
Security World modes are selected when creating a Security World. The available modes,
associated cipher suites, automatic FIPS mechanism compliance and security strengths
are:
Modes Ciphersuite Automatic compliance
of FIPS mechanisms
with NIST SP800-131A
Revision 1
algorithm/key sizes
Security
Strength
FIPS 140-2 Level 3 (FIPS
approved mode
enforced)
DLf3072s256mAEScSP8
00131Ar1
Yes 128 bits
Unrestricted (default) DLf3072s256mAEScSP8
00131Ar1
No (see note 1) 128 bits
Common Criteria CMTS
(see note 2)
DLf3072s256mAEScSP8
00131Ar1
No 128 bits
nShield® Security Manual 49 of 90

 Loading...
Loading...