Juniper Networks SSG 520M and SSG 550M Security Policy
Validation Level
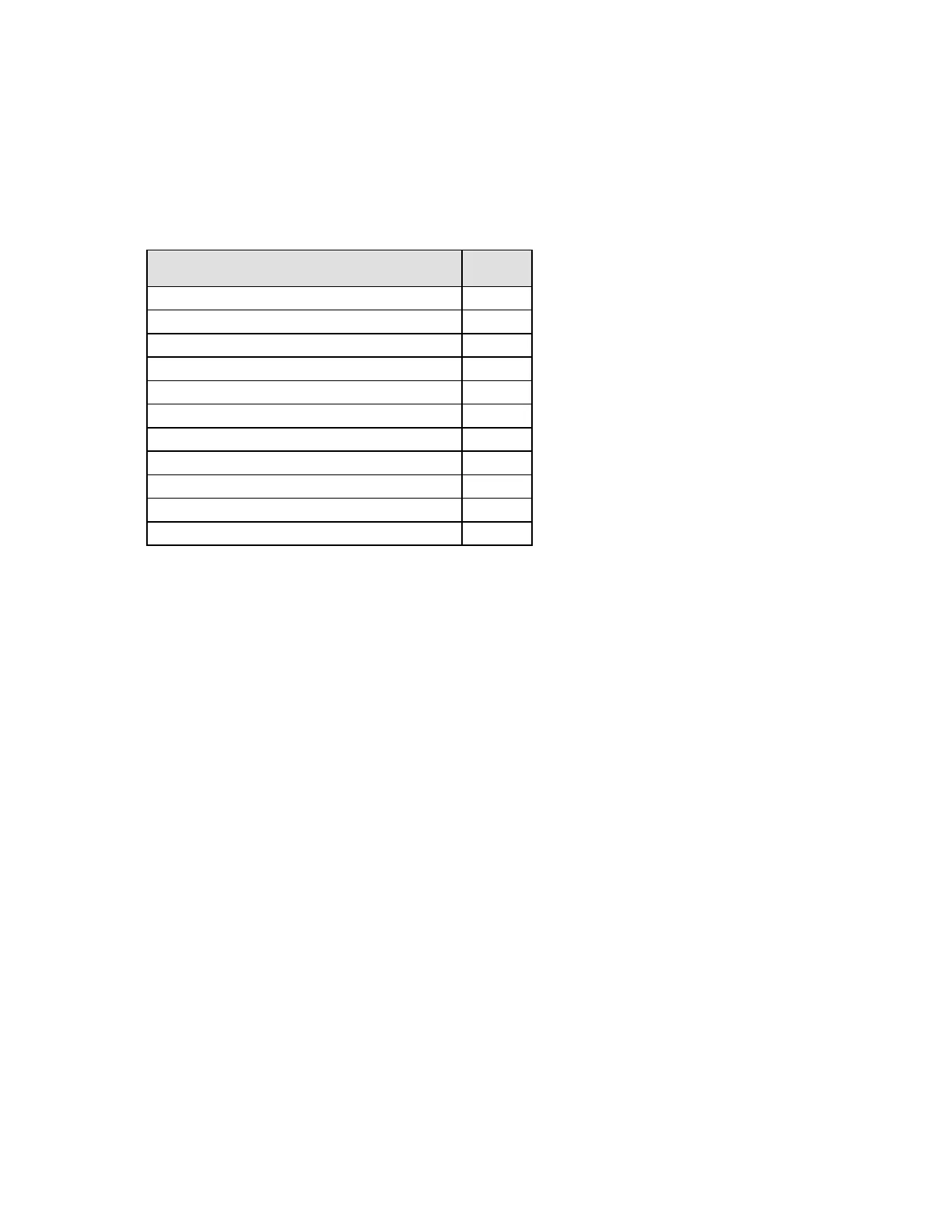
The following table lists the validation level for each FIPS 140-2 area.
Table 1: Module Validation Level
Security Requirements Section
Cryptographic Module Specification
Cryptographic Module Ports and Interfaces
Roles, Services, and Authentication
Cryptographic Key Management
Mitigation of Other Attacks
Roles and Services
The security appliance supports three distinct roles:
Cryptographic Officer (Root): The device allows one Crypto-Officer. This role is assigned to
the first operator who logs on to the device using the default admin name and password
(netscreen, netscreen). Only the Crypto-Officer can create other administrators, change the
device to operate in FIPS mode and apply the tamper-evident seals.
User (Admin): This role can configure specific security policies. These policies provide the
device with information on how to operate. For example, configuring access policies and VPN
encryption with Triple-DES). This role does not have the ability to create other administrators.
Read-Only User (Admin): This role can only perform a limited set of services to retrieve
information or status. This role cannot perform services to configure the device.
The security appliance offers the following services:
Configuration: Configure firewall policies (including the bypass service), VPN encryption and
digital signature options, network interface options, routing tables, protocol support,
authentication servers, logging options and system time. Clear dynamic system information
such as statistics or VPN security associations.
Status: View firewall policies, VPN configuration, traffic and performance statistics, firmware
version, network interface status and system logs. Perform ping and trace-route.
Zeroize: Overwrite all CSP values with three alternating bit patterns, then reset the
configuration to the factory default values. Also occurs when placing the device into or
removing it from FIPS mode.
Manage: Create new users.
Self-tests: Invoke cryptographic algorithm and system integrity self-tests.

 Loading...
Loading...