Xerox Multi-Function Device Security Target
28
Copyright
2013 Xerox Corporation. All rights reserved.
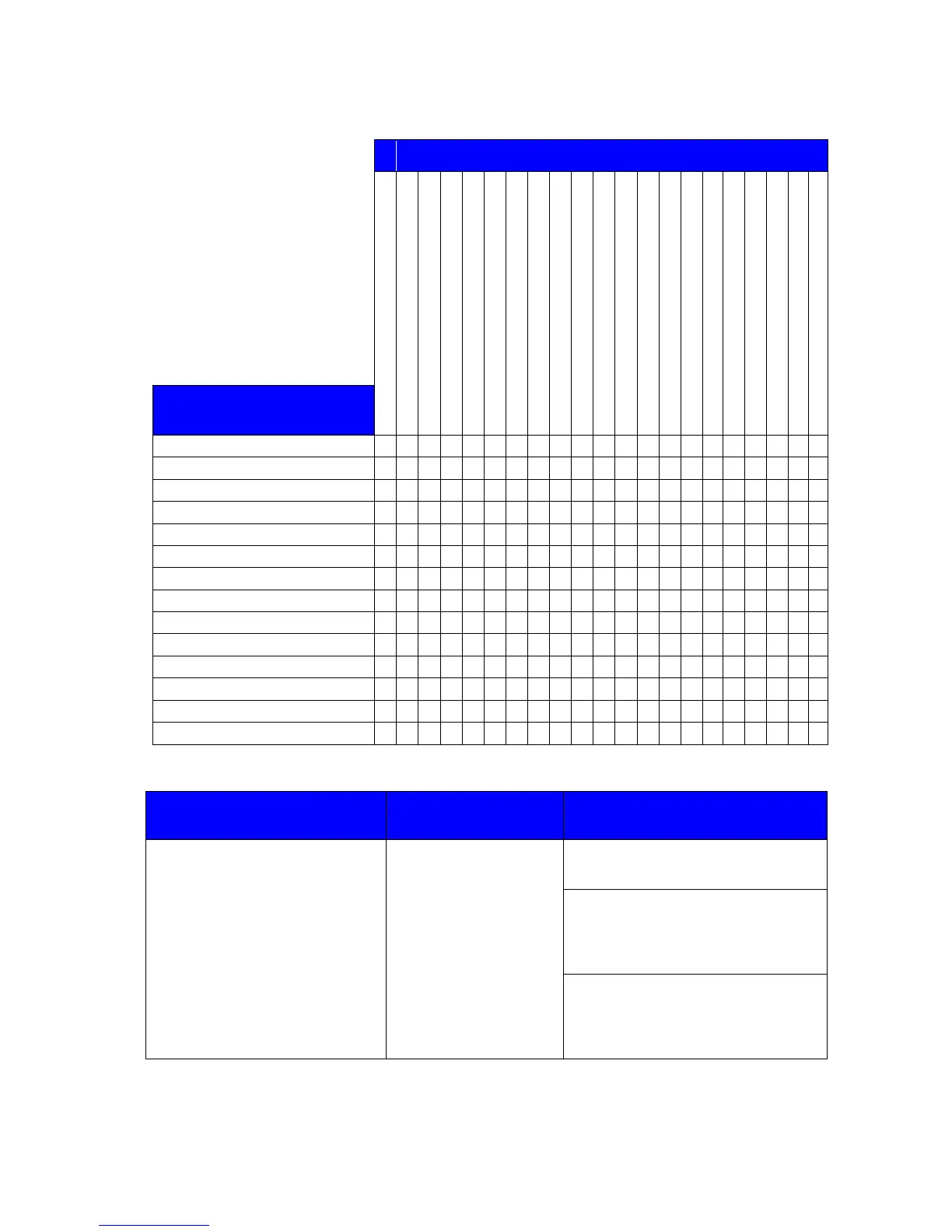
Table 19: Completeness of security objectives
O.AUDIT_STORAGE.PROTECTED
OE.AUDIT_STORAGE.PROTECTED
OE.AUDIT_ACCESS.AUTHORIZED
Threats, policies and
assumptions
Table 20: Sufficiency of security objectives
Threats. Policies, and
Assumptions
User Document Data
may be disclosed to
unauthorized persons
O.DOC.NO_DIS protects D.DOC
from unauthorized disclosure
O.USER.AUTHORIZED
establishes user identification and
authentication as the basis for
authorization
OE.USER.AUTHORIZED
establishes responsibility of the
TOE Owner to appropriately grant
authorization

 Loading...
Loading...