Network Security in Measured Boot
XAPP1309 (v1.0) March 7, 2017 12
www.xilinx.com
Network Security in Measured Boot
Software updates and remote attestation require a secure connection between a server and the
embedded system clients. The network has a large attack surface because it can be attacked by
any adversary with access to the Internet. For firmware updates, a server to client(s) connection
is used. In some factory automation environments, client-to-client communication is also
needed to coordinate operational procedures.
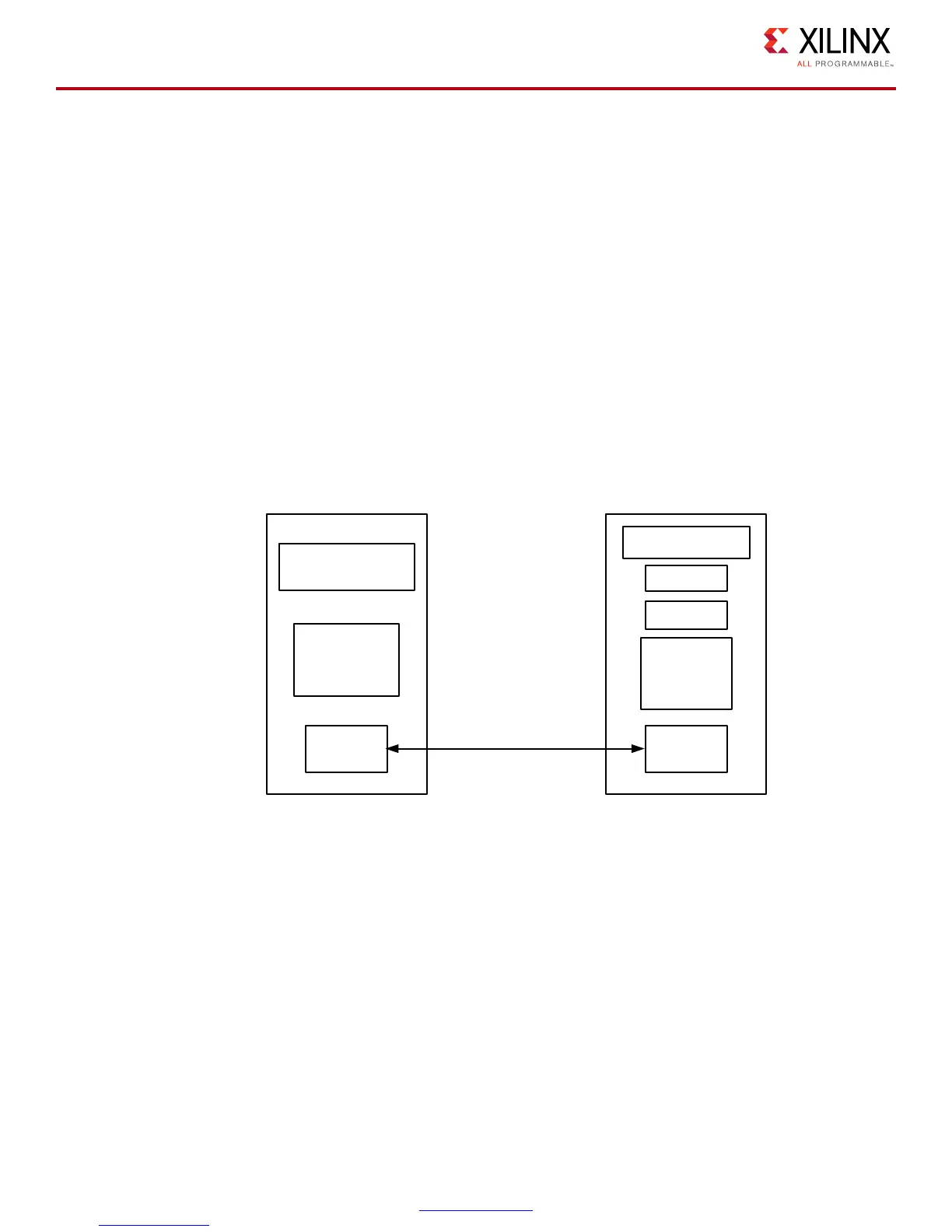
Figure 10 shows a high-level view of strongSwan’s implementation of TCG’s trusted network
connect (TNC). In the TNC architecture, the server connects to clients in the integrity evaluation
layer. The client does integrity measurement collection (IMC), and the server does integrity
measurement verification (IMV). The software on the client is the platform trusted service (PTS),
trust software stack (Trousers), and the TPM tools.
PTS uses the Trousers library to access the TPM and IMA measurements. The reports use
standard PTS formats for interoperability between applications and vendors.
The policy decision point (PDP) defines the action taken by the server after measurement
verification. A typical policy/action is to limit network access until remediation is done. A
different policy is used when availability is a critical driver, and some out-of-range measurement
verifications are not treated as critical. The TPM Main Specification [Ref 4] provides an overview
of the TNC architecture.
The underlying security for TNC in the reference design uses IPsec. This includes conventional
technology such as Internet key exchange (IKEv2), public key infrastructure (PKI), and the
transport layer security (TLS) handshake in which the encryption and authentication algorithms
are negotiated and pre-shared keys are exchanged. A virtual private network is set up in the
strongSwan architecture. A privacy CA generates the x509 certificates. The strongSwan
Readme.txt provides information on the IPsec flow.
X-Ref Target - Figure 10
Figure 10: Trusted Network Connect for Remote Attestation
Policy Decision/
Enforcer
Integrity
Measurement
Verifier
TNC Server TNC Client
Integrity
Measurement
Collector
Server Client
Trousers
TPM Tools
Platform Trust
Service
IPsec
X18728-020317

 Loading...
Loading...











