8-7
Cisco ASA 5500 Series Getting Started Guide
78-19186-01
Chapter 8 Scenario: DMZ Configuration
Example DMZ Network Topology
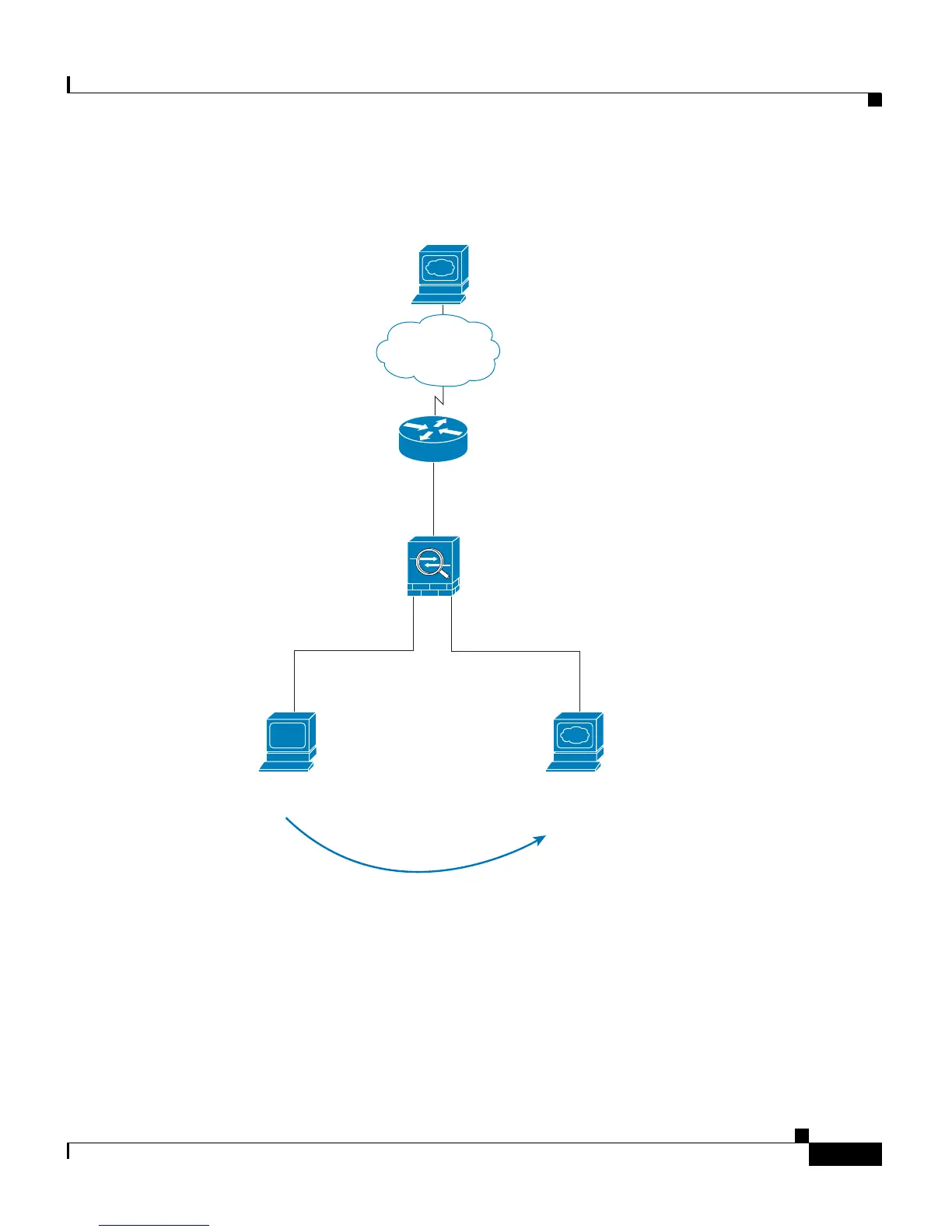
Figure 8-4 An Inside User Visits a Web Server on the DMZ
In Figure 8-4, the adaptive security appliance permits HTTP traffic originating
from inside clients and destined for the DMZ web server. Because the internal
network does not include a DNS server, internal client requests for the DMZ web
server are handled as follows:
1. A lookup request is sent to the DNS server of the ISP. The public IP address
of the DMZ web server is returned to the client.
User
192.168.1.2
Inside
DMZ
191801
www.example.com
Internet
Public IP Address
209.165.200.225
(outside interface)
Inside interface
192.168.1.1
DMZ interface
10.30.30.1
Web Server
Private IP Address: 10.30.30.30
Public IP Address: 209.165.200.225

 Loading...
Loading...