Security: 802.1X Authentication
Overview
Cisco 350, 350X and 550X Series Managed Switches, Firmware Release 2.4, ver 0.4 361
18
Switch as 802.1x Supplicant
In addition to its capacity as an 802.1x authenticator, the switch itself can be configured as an
802.1x supplicant seeking port access permission from a neighbor. The supplicant supports the
EAP MD5-Challenge method specified by RFC3748. The method authenticates a client by its
name and password.
When the supplicant is enabled on an interface, the interface becomes unauthorized. When the
802.1X authentication process succeeds, the interface state is changed to authorized.
The following events start the 802.1X supplicant authentication on a port:
• Supplicant is enabled on a port in the Up status.
• The status of the port is changed to Up and supplicant is enabled on the port.
• An EAP Identifier Request message is received on the port and the supplicant is
enabled on the port.
802.1x authenticator and supplicant cannot be configured at the same time on a single
interface.
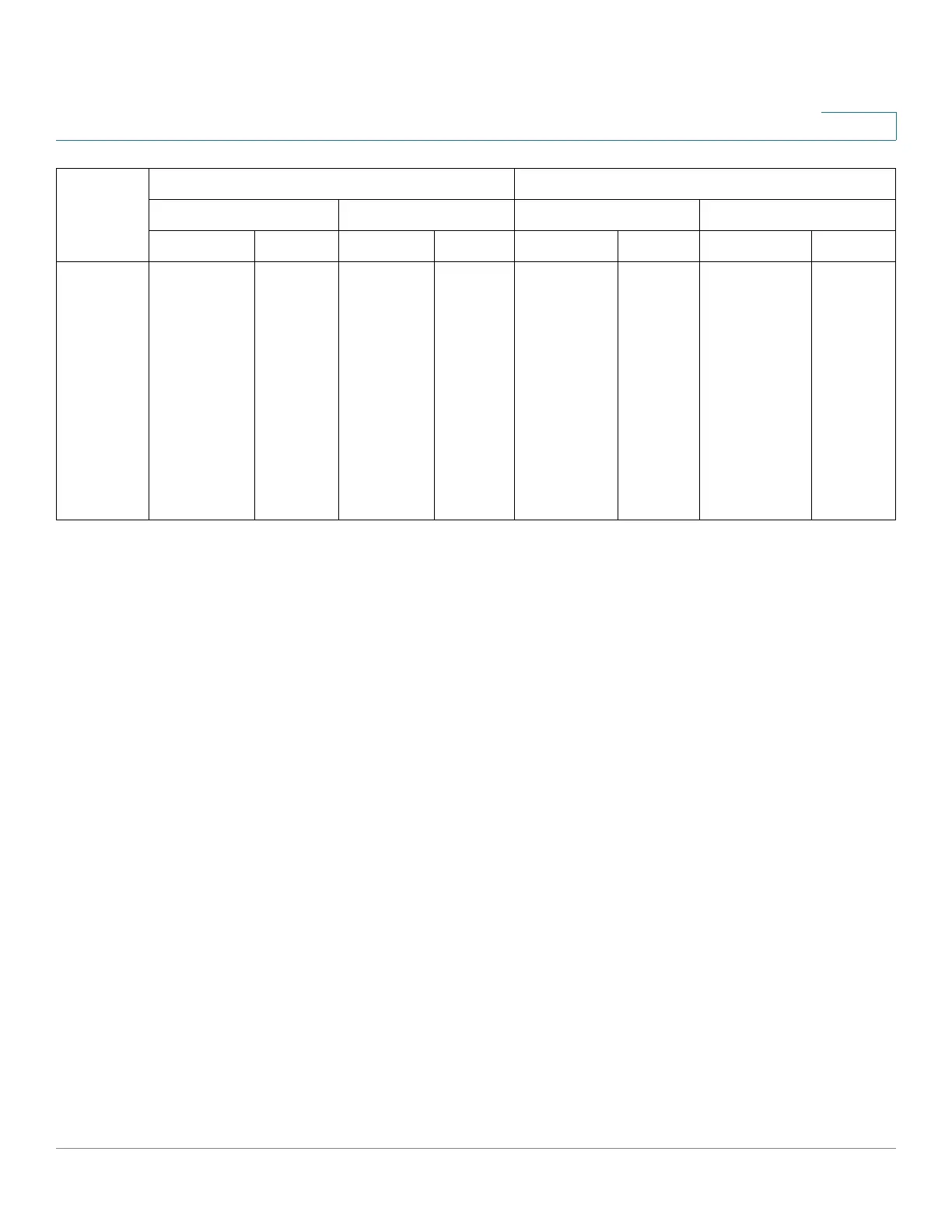
Full multi-
sessions
Frames are
re-mapped to
the guest
VLAN
Frames
are re-
mapped to
the guest
VLAN
unless
they
belongs to
the
unauthent
icated
VLANs
Frames are
dropped
Frames
are
dropped
unless
they
belongs
to the
unauthent
icated
VLANs
Frames are
re-mapped to
the RADIUS
assigned
VLAN
Frames
are re-
mapped
to the
Radius
VLAN
unless
they
belongs
to the
unauthent
icated
VLANs
Frames are
bridged based
on the static
VLAN
configuration
Frames
are
bridged
based on
the static
VLAN
configurat
ion
Unauthenticated Traffic Authenticated Traffic
With Guest VLAN Without Guest VLAN With Radius VLAN Without Radius VLAN
Untagged Tagged Untagged Tagged Untagged Tagged Untagged Tagged
 Loading...
Loading...