19
11. Viewing logs and statistics
The Scan log section (Menu > Logs > Scan) contains logs
providing comprehensive data about completed scan
tasks. Logs are created after each successful On-demand
scan or when an infiltration is detected by the On-access
scan. All infected files are highlighted in red. At the end of
each log entry is an explanation of why the file was
included in the log.
Scan logs contain:
log file name (usually in the form Scan.Number.log)
date and time of the event
list of scanned files
actions performed or errors encountered during the
scan
Scan log
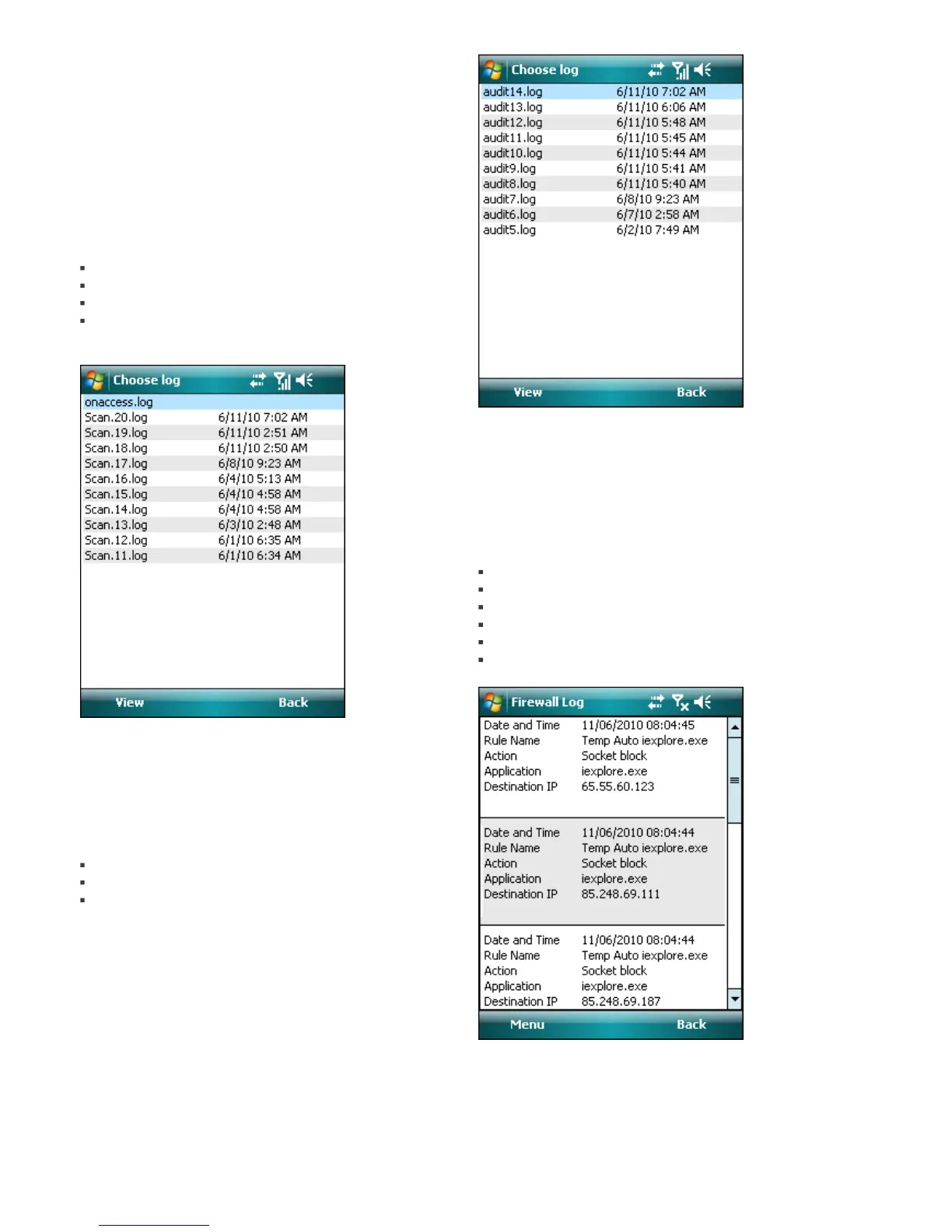
The Security audit log section (Menu > Logs > Security
audit) stores all security audit results from both
automatic (scheduled) audit and manually triggered
audit.
Security audit logs contain:
log file name (in the form auditNumber.log)
date and time of audit
detailed results
Security audit log
The Firewall Log (Menu > Logs > Firewall) contains the
information about the firewall events blocked by ESET
Mobile Security. The log is updated after every
communication performed through the firewall. New
events appear on the top of the log.
Firewall Log contains:
date and time of the event
name of the rule used
action performed (based on the rule settings)
source IP address
destination IP address
protocol used
Firewall log
 Loading...
Loading...











