Endpoint Network Access Control Enabling Endpoint Control
FortiClient Endpoint Security Version 4.0 MR1 Administration Guide
04-40001-99556-20090626 37
http://docs.fortinet.com/ • Feedback
• Allow — The FortiGate unit takes no action against applications.
• Monitor — The FortiGate unit records the application in the logs and in the Endpoint
NAC > Monitor list but will not take any action against the user.
• Block — The FortiGate unit quarantines the host and records the violating applications
in the logs and in the Endpoint NAC > Monitor list. A “quarantined” message is shown
to the user in the web browser.
For more information about creating firewall policies, see the Firewall chapter of the
FortiGate Administration Guide.
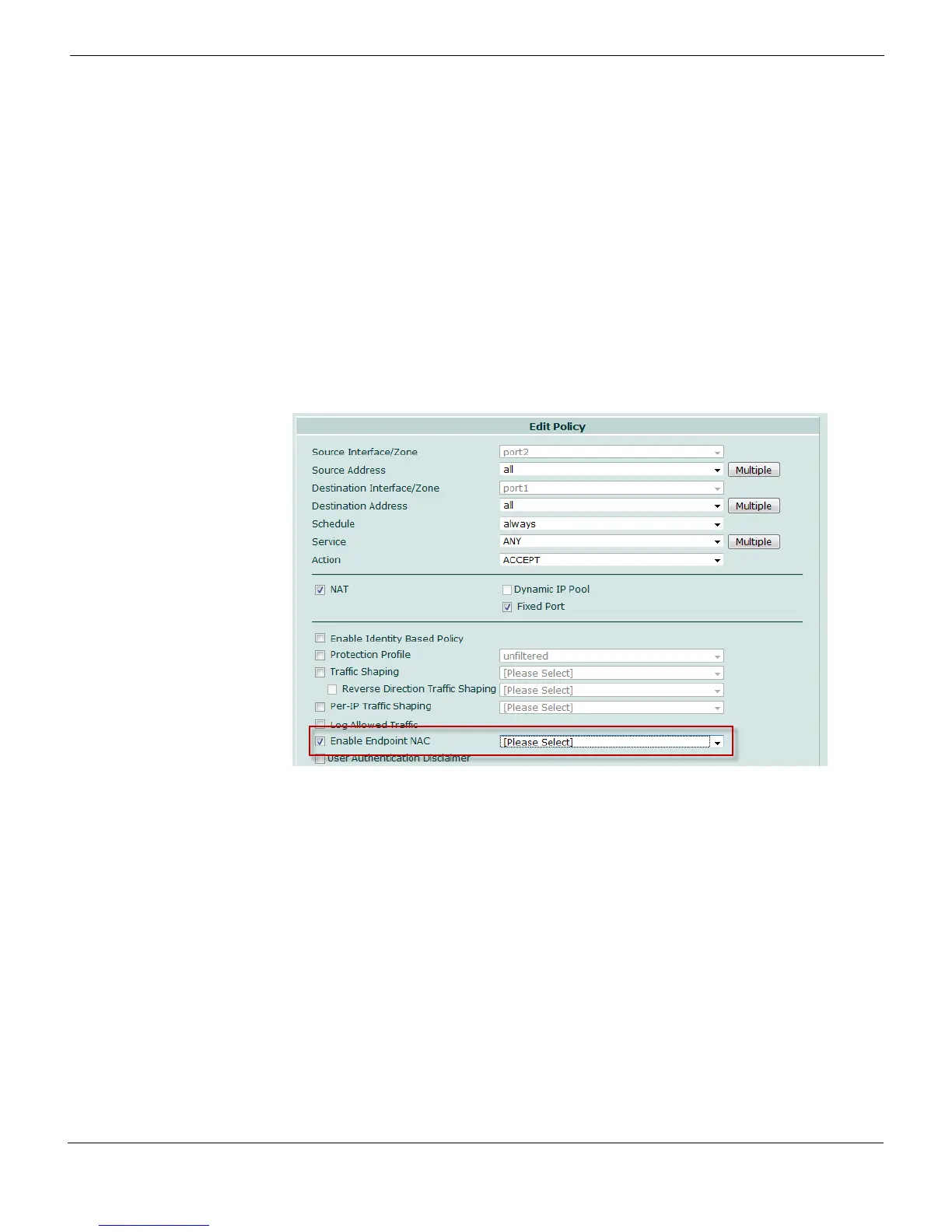
To apply an Endpoint Control Profile to a firewall policy
1 Go to Firewall > Policy and select the Policy tab.
2 Select a firewall policy and click Edit.
Figure 8: Enabling Endpoint NAC in a firewall policy
3 Select Enable Endpoint NAC and do one of the following:
• Select the endpoint profile from the list.
•Select Create New and create an endpoint profile. See “To create an Endpoint
Control profile” on page 33.
4 Click OK.
Monitoring Endpoints
If you have the Application Detection List set to Monitor or Block and have applied it to an
Endpoint Control Profile and a firewall policy, you can view which applications have
attempted to pass through the Fortigate unit.
To monitor endpoints
1 Go to Endpoint NAC > Monitor.
 Loading...
Loading...