6-23
Configuring Secure Shell (SSH)
Further Information on SSH Client Public-Key Authentication
a. Combines the decrypted byte sequence with specific session data.
b. Uses a secure hash algorithm to create a hash version of this informa-
tion.
c. Returns the hash version to the switch.
7. The switch computes its own hash version of the data in step 6 and
compares it to the client’s hash version. If they match, then the client is
authenticated. Otherwise, the client is denied access.
Using client public-key authentication requires these steps:
1. Generate a public/private key pair for each client you want to have SSH
access to the switch. This can be a separate key for each client or the same
key copied to several clients.
2. Copy the public key for each client into a client-public-key text file.
3. Use copy tftp to copy the client-public-key file into the switch. Note that
the switch can hold 10 keys. The new key is appended to the client public-
key file
4. Use the aaa authentication ssh command to enable client public-key
authentication.
To Create a Client-Public-Key Text File. These steps describe how to
copy client-public-keys into the switch for RSA challenge-response authenti-
cation, and require an understanding of how to use your SSH client applica-
tion.
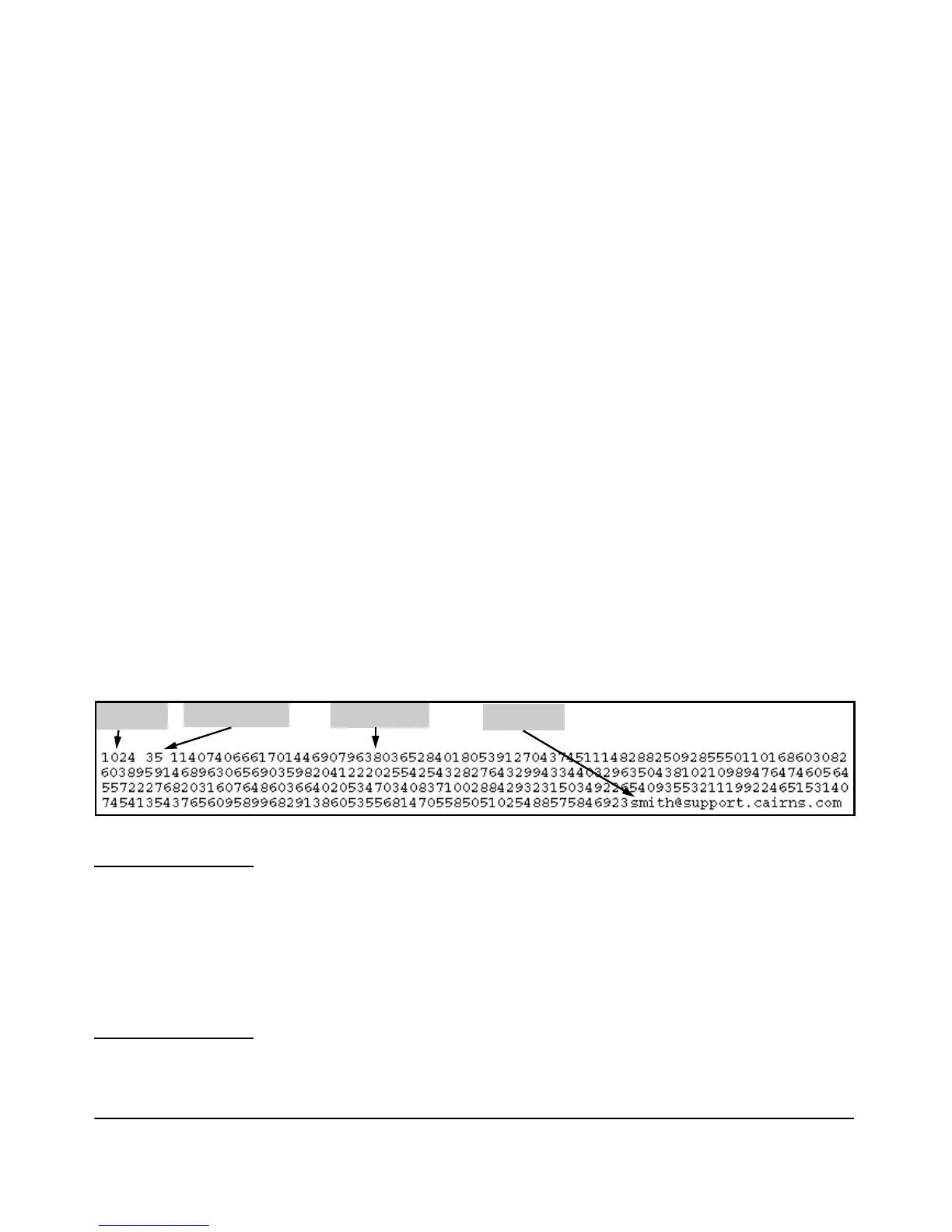
Figure 6-14. Example of a Client Public Key
Notes Comments in public key files, such as smith@support.cairns.com in figure 6-14,
may appear in a SSH client application’s generated public key. While such
comments may help to distinguish one key from another, they do not pose any
restriction on the use of a key by multiple clients and/or users.
Public key illustrations such as the key shown in figure 6-14 usually include
line breaks as a method for showing the whole key. However, in practice, line
breaks in a public key will cause errors resulting in authentication failure.
Bit Size Exponent <e>
Modulus <n>
Comment

 Loading...
Loading...











