MEMORY MANAGEMENT AND VIRTUAL ADDRESSING
VIRTUAL ADDRESS
I I I
TARGET
SELECTOR OFFSET
SEGMENT
TI
0-
PHYSICAL
DATUM
DESCRIPTOR
ADDRESS
I
TABLE
I
SEGMENT
SEGMENT
BASE
DESCRIPTOR
----
INDEX
G3010B
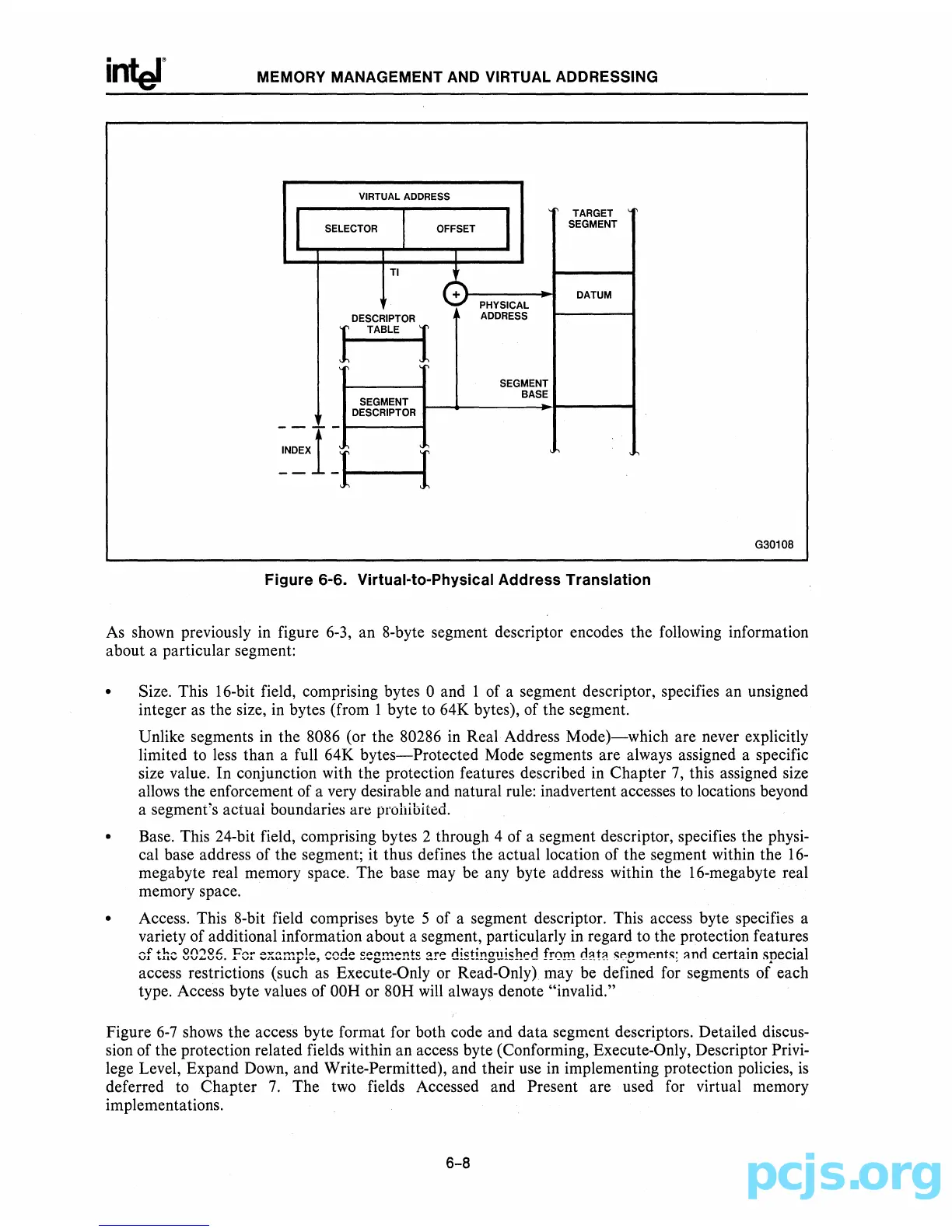
Figure
6-6.
Virtual-to-Physical Address Translation
As shown previously in figure
6-3,
an 8-byte segment descriptor encodes the following information
about a particular segment:
Size. This 16-bit field, comprising bytes
0 and 1 of a segment descriptor, specifies an unsigned
integer as the size,
in
bytes (from 1 byte
to
64K bytes), of the segment.
Unlike segments
in
the 8086 (or the 80286
in
Real Address
Mode)-which
are never explicitly
limited to
less
than a full 64K
bytes-Protected
Mode segments are always assigned a specific
size value. In conjunction with the protection features described in Chapter
7,
this assigned size
allows
the enforcement of a very desirable and natural rule: inadvertent accesses
to
locations beyond
a segment's actual boundaries are prohibited.
Base. This 24-bit field, comprising bytes 2 through 4 of a segment descriptor, specifies the physi-
cal base address of the segment; it thus defines the actual location of the segment within the
16-
megabyte real memory space. The base may be any byte address within the 16-megabyte real
memory space.
Access. This 8-bit field comprises byte 5 of a segment descriptor. This access byte specifies a
variety of additional information about a segment, particularly
in
regard to the protection features
of
the
80286.
Fer
example,
cede
seg!TI.ents
are
distinguished
from
certain
special
access restrictions (such as Execute-Only or Read-Only) may be defined for segments of each
type. Access byte values of
OOH
or 80H
will
denote "invalid."
Figure
6-7
shows the access byte format for both code and data segment descriptors. Detailed discus-
sion of the protection related fields within an access byte (Conforming, Execute-Only, Descriptor Privi-
lege Level, Expand Down, and Write-Permitted), and their use
in
implementing protection policies,
is
deferred
to
Chapter
7.
The
two
fields Accessed and Present are used
for
virtual memory
implementations.
6-8
 Loading...
Loading...











