5. Log into the IDP command-line interface and verify the SSH key fingerprint.
Comparing the SSH key fingerprint information enables you to detect
man-in-the-middle attacks:
a. Connect to the IDP command-line interface:
■ Use SSH to connect to the IP address or hostname for the management
interface. Log in as admin and enter su – to switch to root.
■ If you prefer, make a connection through the serial port and log in as
root.
b. Enter cd /etc/ssh.
c. Enter ssh-keygen -l -f ssh_host_dsa_key.
The command generates output similar to the following:
1024 f4:91:d0:04:b7:61:00:77:45:c3:cc:bd:af:b3:5b:a2 ssh_host_dsa_key.pub
After you have verified the SSH key fingerprint matches, click Next.
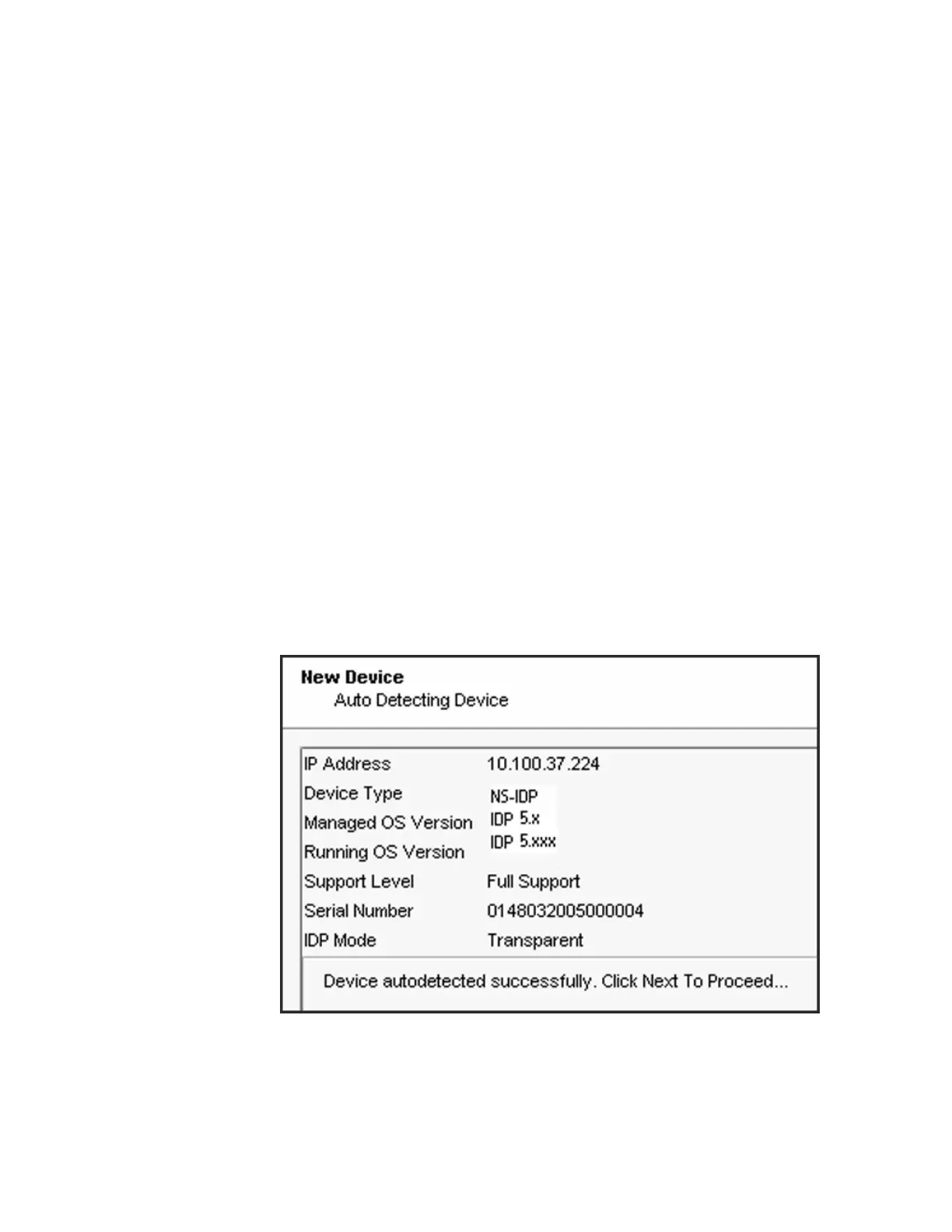
The Wizard displays a page where NSM retrieves and displays inventory
information. Please wait a moment as the NSM retrieves inventory information
from the IDP appliance.
Figure 15: NSM Add Device Wizard: Inventory Information
6. Verify that the device type, OS version, device serial number, and device mode
are correct.
7. Click Next to add the device to NSM. Upon success, NSM displays the following
message:
44 ■ Adding a Reachable IDP Device to NSM
IDP250 Installation Guide
Download from Www.Somanuals.com. All Manuals Search And Download.
 Loading...
Loading...











