WLAN VDSL Gateway User Manual
34
wireless network.
There are several security methods to choose from, depending on user’s needs and
the capabilities of user’s wireless machines.
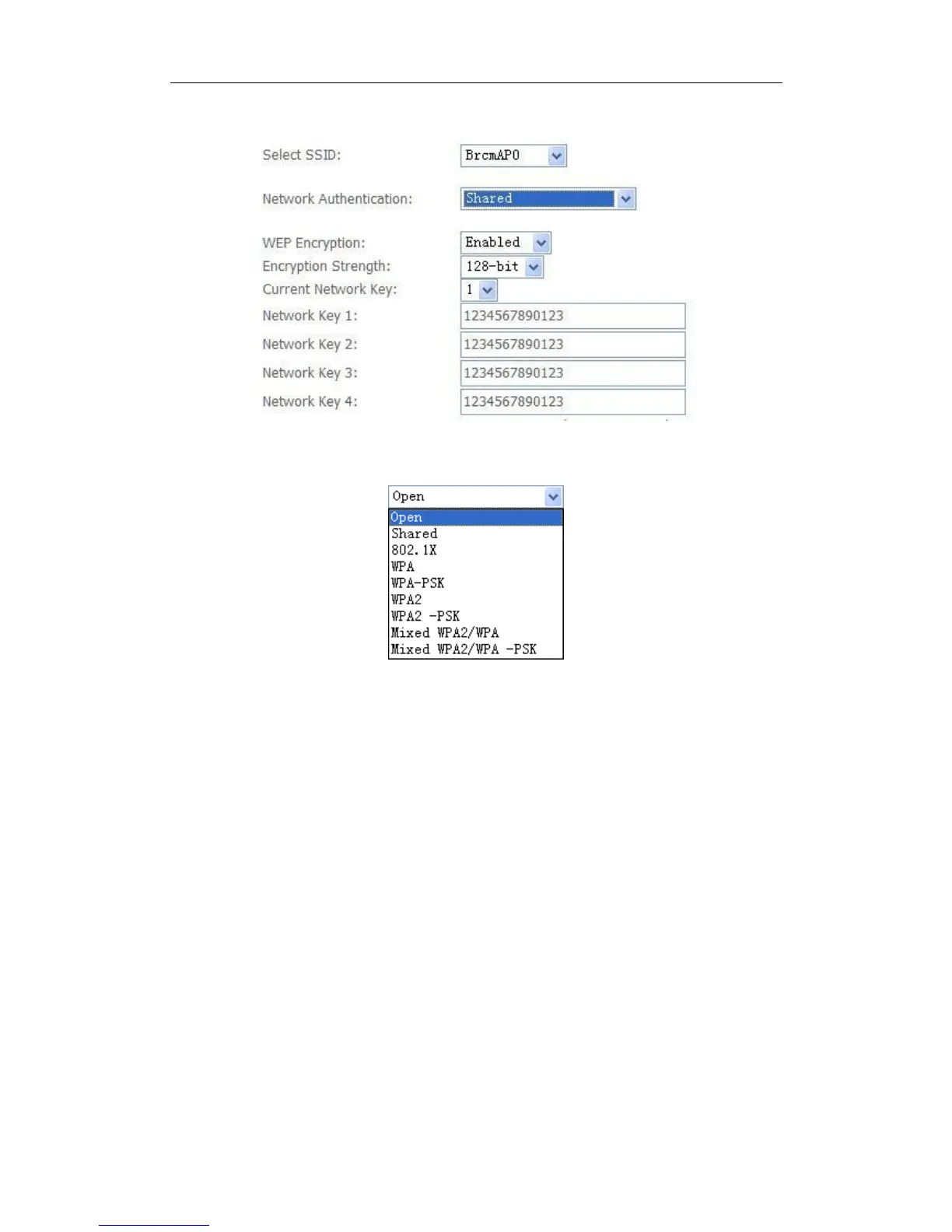
WEP open and WEP shared —WEP is an encryption scheme that is used
to protect user’s wireless data communications. WEP uses a combination
of 64-bit keys or 128-bit keys to provide access control to user’s network
and encryption security for every data transmission. To decode a data
transmission, each wireless client on the network must use an identical
64-bit or 128-bit key. WEP is an older wireless encryption method that is
not as hard to break as the more-recent WPA.
802.1x — In 802.1x (also known as RADIUS), a separate machine called an
authentication server receives a user ID and password. It grants or denies
access based on whether the ID and password match any entries in its
account list. User can optionally enable WEP encryption with this option.
Because it requires a separate machine acting as the authentication server,
802.1x is most often used in business environments.
WPA — WPA is a more recent encryption method that addresses many of
 Loading...
Loading...