Security
Operating Manual PSEN sc M 3.0/5.5 08-17
1005387-EN-05
| 16
4 Security
To secure plants, systems, machines and networks against cyberthreats it is necessary to
implement (and continuously maintain) an overall industrial security concept that is state of
the art.
Perform a risk assessment in accordance with VDI/VDE 2182 or IEC 62443-3-2 and plan
the security measures with care. If necessary, seek advice from Pilz Customer Support.
4.1 Required security measures
} The product is not protected from physical manipulation or from reading of memory con-
tents during physical access. Use appropriate measures to ensure that there is no phys-
ical access by unauthorised persons. You should also use security seals so that you can
detect any manipulation of the product or interfaces. Installation inside a lockable control
cabinet is recommended as a minimum measure.
} The configuration computer that accesses the product has to be protected from attacks
by a firewall or other suitable measures. We recommend that a virus scanner is used on
this configuration computer and updated regularly.
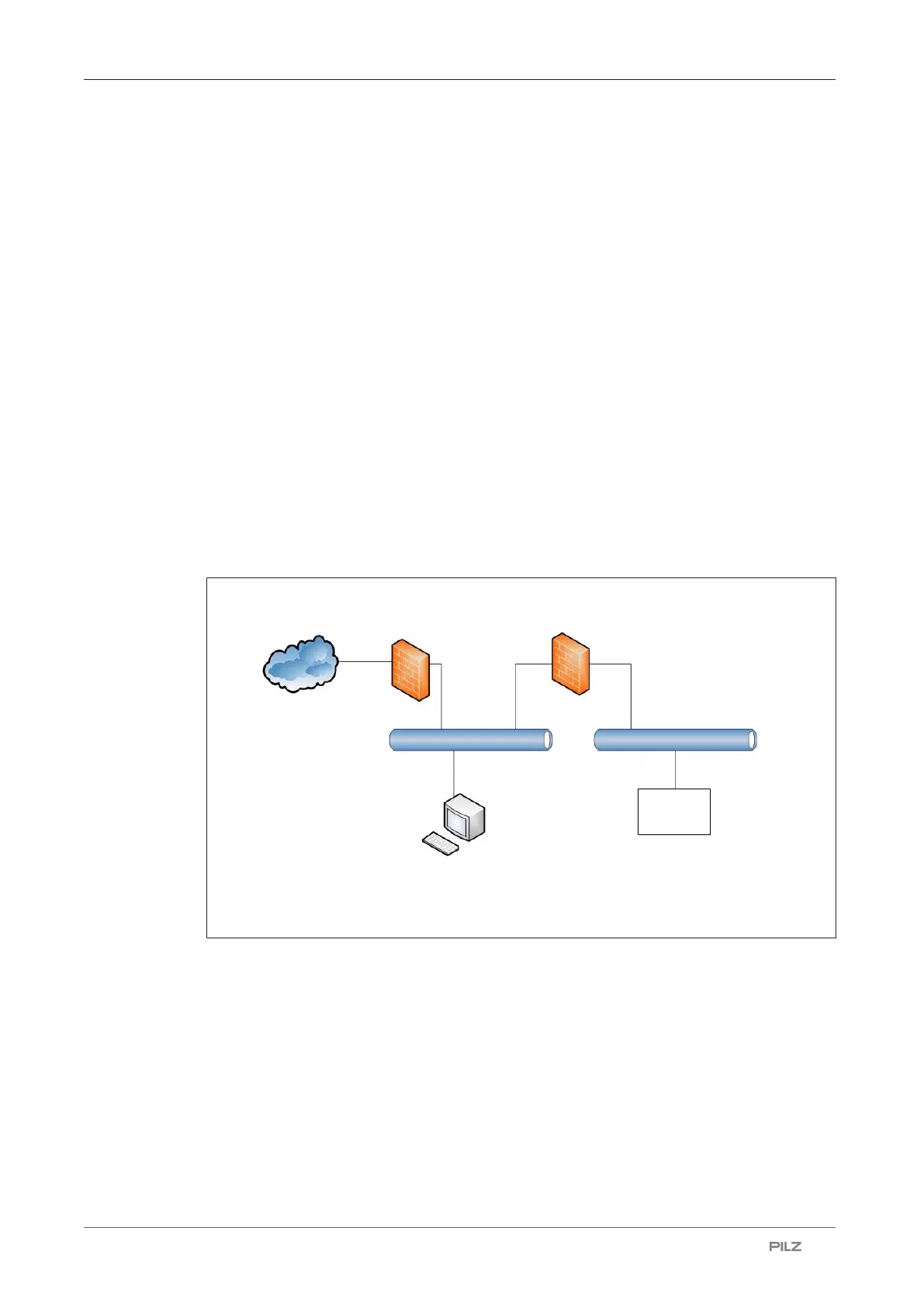
} Ensure that the product is separated by a router (layer 3 switch or firewall) from the com-
pany network.
Company firewall Machine firewall
Company network Machine network
Internet
Configuration computer
Product
Fig.: Example network topology
} If necessary, protect the configuration computer and the product from unauthorised use
by assigning passwords and taking further measures if required. We also recommend
that the user logged on to this configuration computer does not have administrator rights.

 Loading...
Loading...