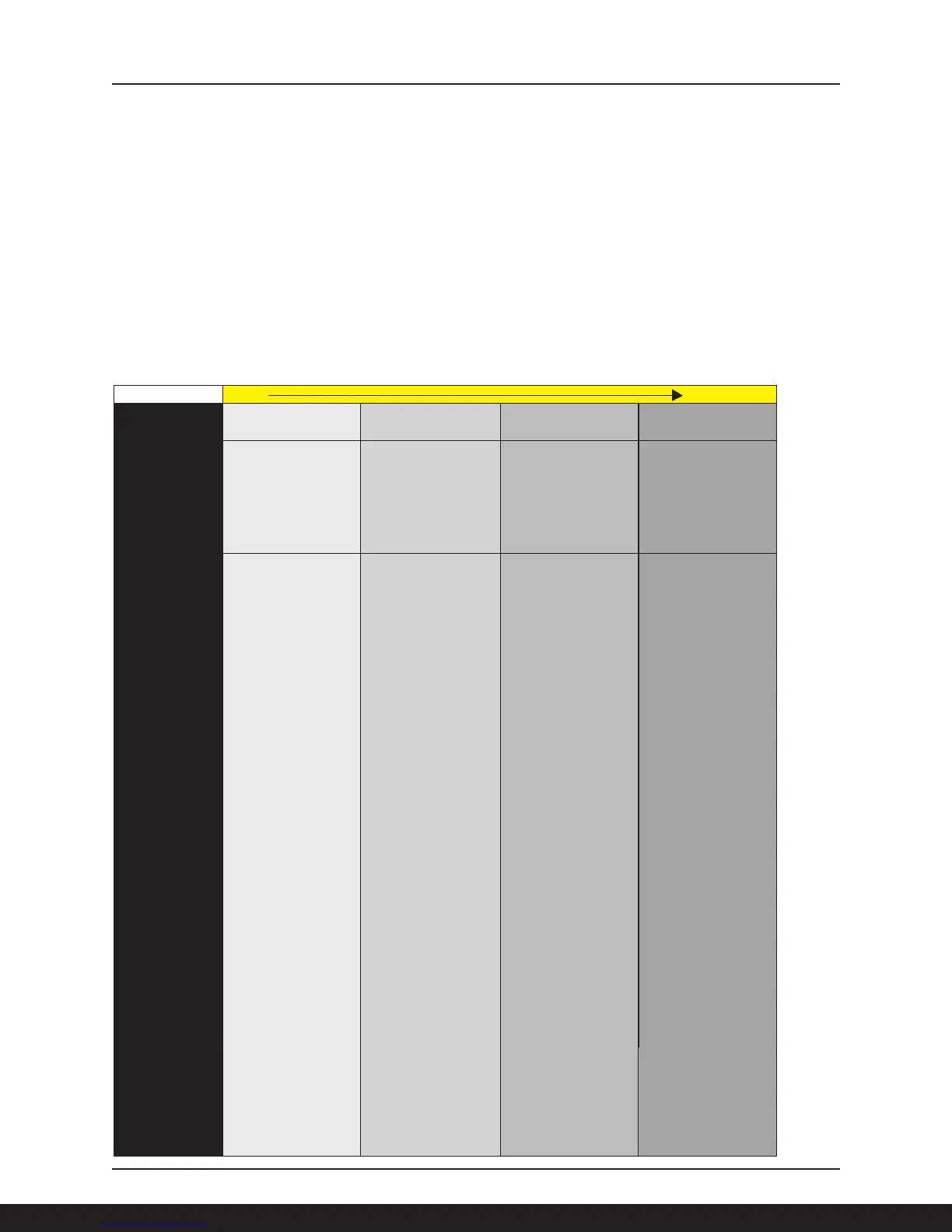4
Risk Levels
Every company is different and their exposure to all types of security threats will vary based on the
nature of their business and the sensitivity of the information that is processed. Further, the location
and configuration of a specific device will also impact the appropriate level of security. Non-networked
devices, for example, may only require local (internal) user authentication whereas networked peripherals
will demand more robust login (external) controls. Those devices with hard disk drives used for long-term
document storage require different security solutions than a desktop printer that uses only RAM to
temporarily store print jobs. This table identifies the measures a customer can implement based on their
objectives.
Plus...
Plus...
Plus...

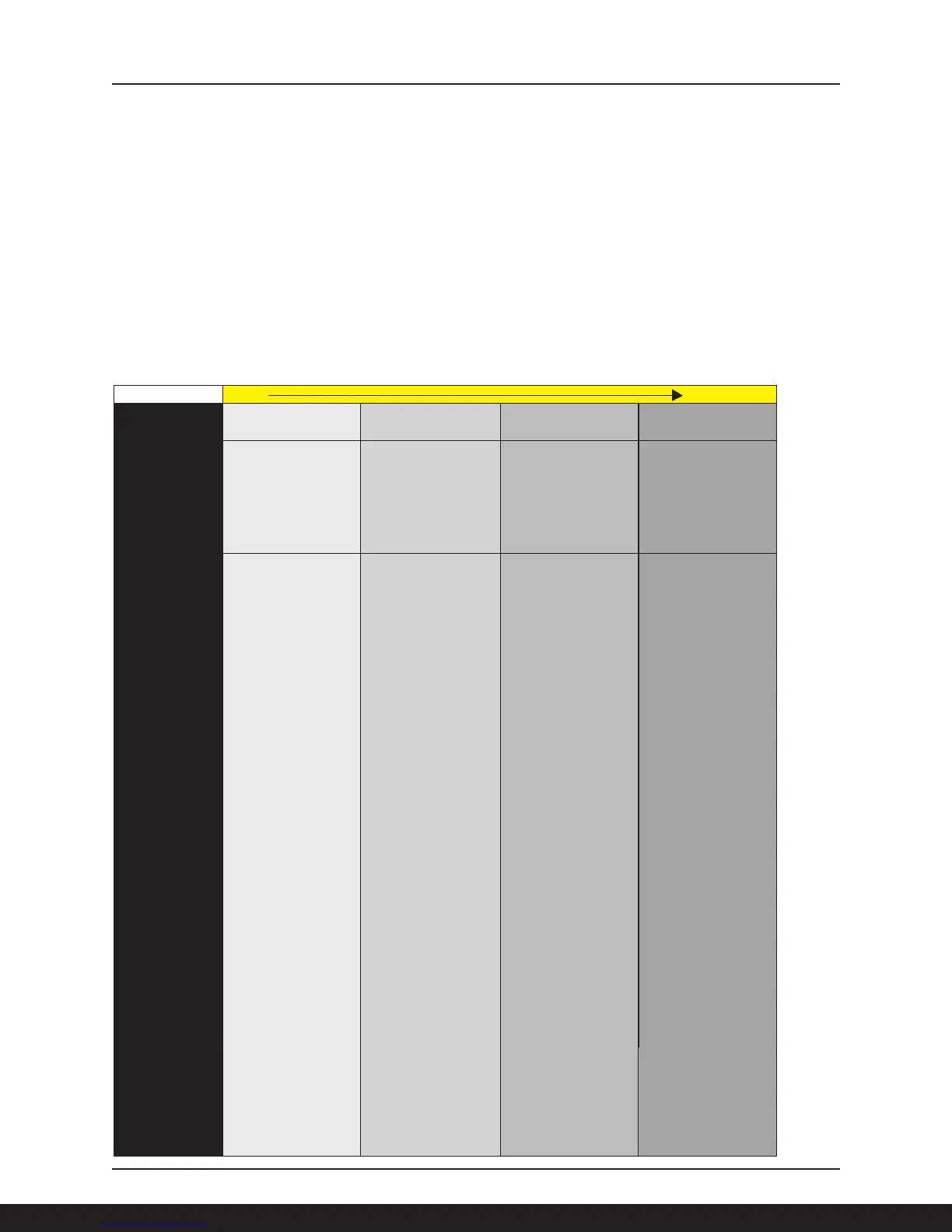 Loading...
Loading...