Xerox® Security Guide for Office Class Products: AltaLink® VersaLink®
November 2018 Page 18
Network Access Control
802.1x
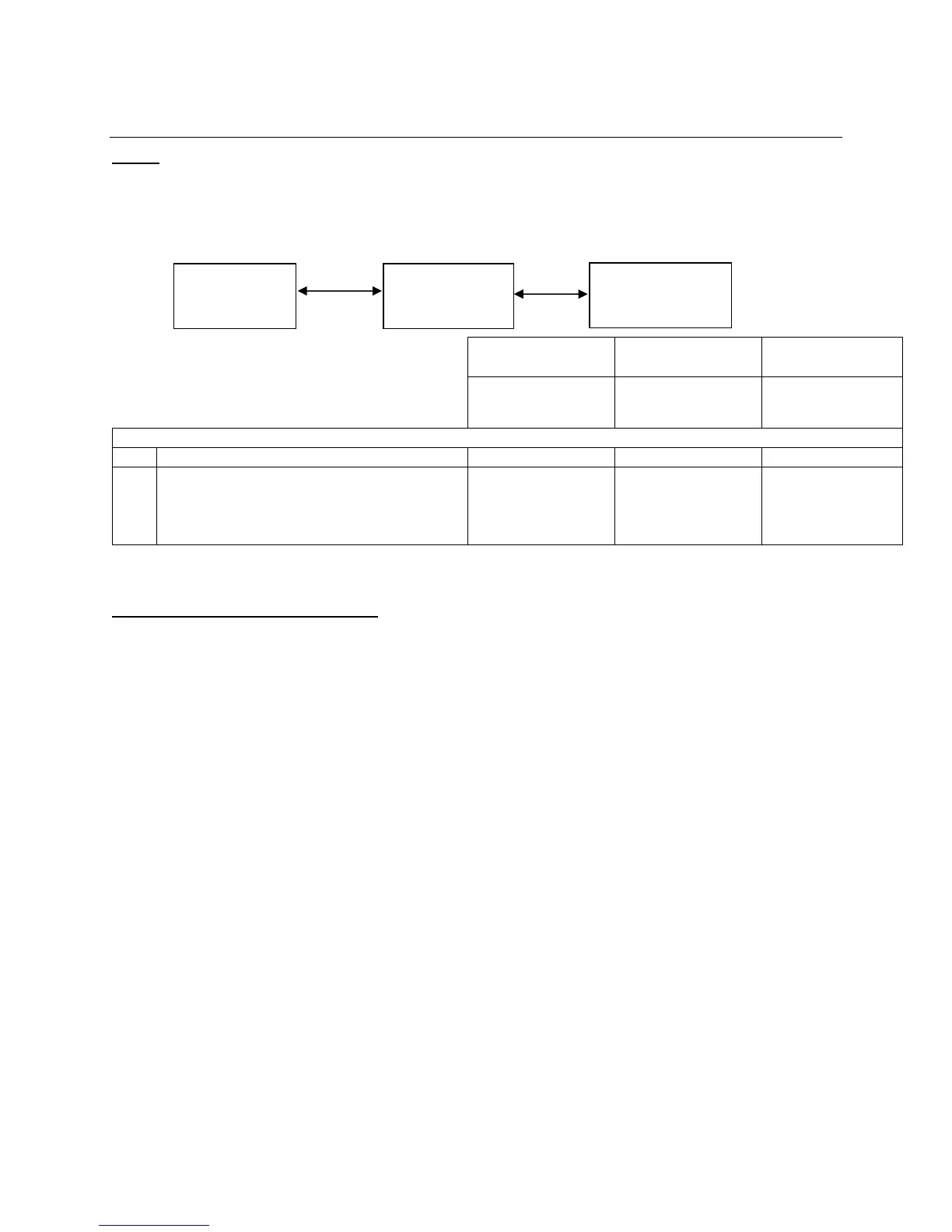
In 802.1X authentication, when the product is connected to the LAN port of Authenticator such as the
switch as shown below, the Authentication Server authenticates the product, and the Authenticator
controls access of the LAN port according to the authentication result. The product starts authentication
processing at startup when the startup settings for 802.1X authentication are enabled.
B8045, B8055, B8065, B8075,
B8090, C8030, C8035, C8045,
C8055, C8070
B405, B605, B615, B7025,
B7030, B7035, C405, C505,
C605, C7020, C7025, C7030
B400, B600, B610, C400, C500,
C600, C7000, C8000, C9000
PSK, AES (CCMP)/TKIP,
PEAPv0/MS-CHAPv2, EAP-
TLS, EAP-TTLS/PAP, EAP-
TTLS/MS-CHAPv2, EAP-
TTLS/EAP-TLS
MD5, MS-CHAPv2,
PEAP/MS-CHAPv2, EAP-TLS
MD5, MS-CHAPv2,
PEAP/MS-CHAPv2, EAP-TLS
Cisco Identity Services Engine (ISE)
Cisco ISE is an intelligent security policy enforcement platform that mitigates security risks by providing a
complete view of which users and what products are being connected across the entire network
infrastructure. It also provides control over what users can access your network and where they can go.
Cisco's ISE includes over 200 Xerox product profiles that are ready for security policy enablement. This
allows ISE to automatically detect Xerox products in your network. Xerox products are organized in Cisco
ISE under product families, such as AltaLink® and VersaLink®, enabling Cisco ISE to automatically
detect and profile new Xerox products from the day they are released. Customers who use Cisco ISE
find that including Xerox products in their security policies is simpler and requires minimal effort.
Cisco ISE Profiling Services provides dynamic detection and classification of endpoints connected to the
network. ISE collects various attributes for each network endpoint to build an endpoint database. The
classification process matches the collected attributes to prebuilt or user-defined conditions, which are
then correlated to an extensive library of product profiles. These profiles include a wide range of product
types, including tablets, smartphones, cameras, desktop operating systems (for example, Windows®,
Mac OS® X, Linux® and others), and workgroup systems such as Xerox printers and MFPs.
Once classified, endpoints can be authorized to the network and granted access based on their profile
signature. For example, guests to your network will have different level of access to printers and other
end points in your network. As an example, you and your employees can get full printer access when
accessing the network from a corporate workstation but be granted limited printer access when accessing
the network from your personal Apple® iPhone®.
Cisco ISE allows you to deploy the following controls and monitoring of Xerox products:
Automatically provision and grant network access rights to printers and MFPs to prevent
inappropriate access (including automatically tracking new printing products connecting to the
network):
o Block non-printers from connecting on ports assigned to printers
Server
(e.g. Switch)
(Supplicant)

 Loading...
Loading...











