WorkCentre 7220-7225 Information Assurance Disclosure Paper
Ver. 1.0, January 2013 Page 37 of 61
4.2. Audit Log
The device maintains a security audit log. Recording of security audit log data can be enabled or disabled by the SA.
The audit log is implemented as a circular log containing a maximum of 15000 event entries, meaning that once the
maximum number of entries is reached, the log will begin overwriting the earliest entry. Only an SA will be
authorized to download the log from the device. The log may only be exported over an https: connection, so SSL
must be set up before retrieving the log. The log is exported in Comma-Separated Value (CSV) file format. The log
does not clear when it is disabled, and will persist through power cycles.
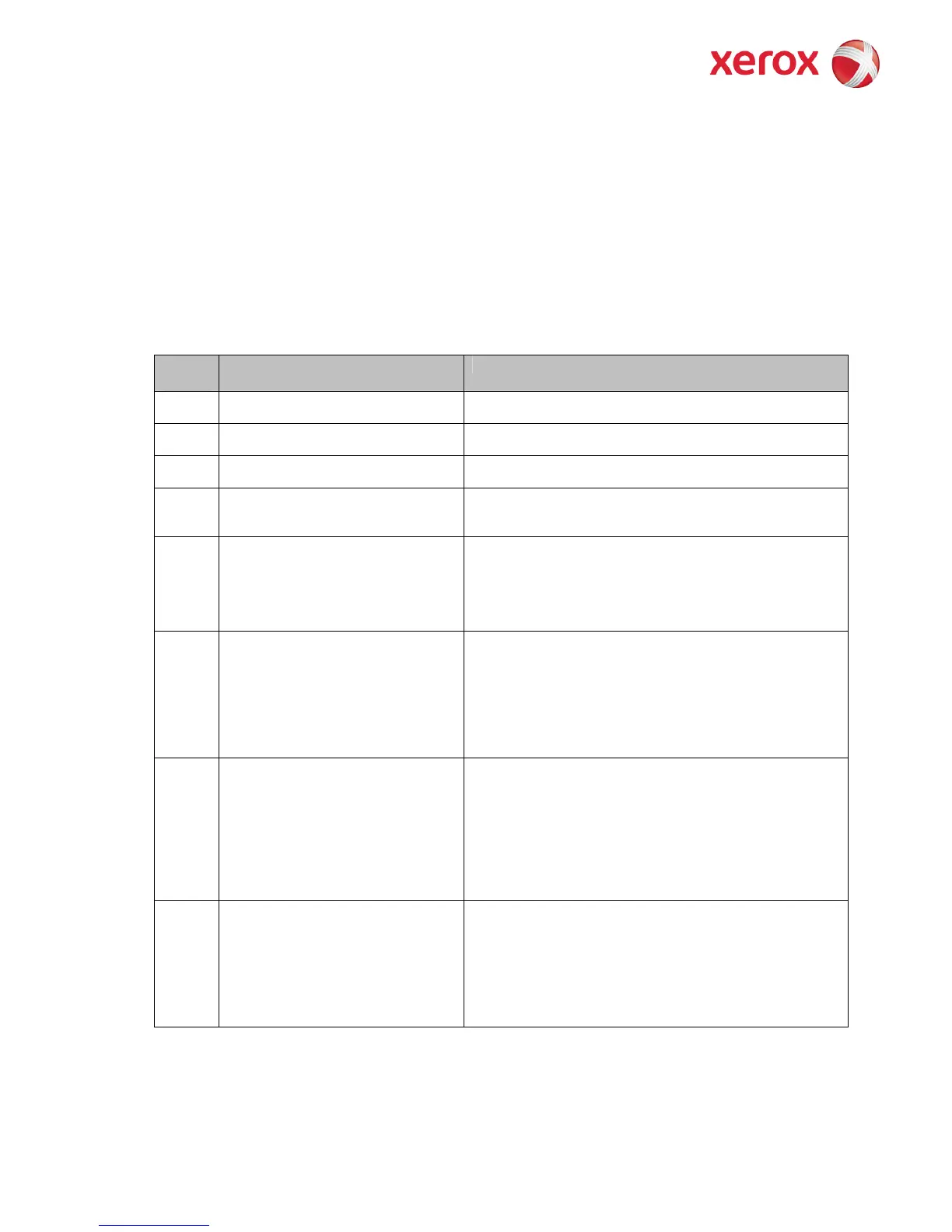
The following table lists the events that are recorded in the log:
ID
1 System startup Device name
Device serial number
2 System shutdown Device name
Device serial number
3 Manual ODIO Standard started Device name
Device serial number
4 Manual ODIO Standard complete Device name
Device serial number
Overwrite Status
5 Print job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
6 Network scan job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-net-destination
net-destination.
7 Server fax job Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
Total-fax-recipient-phone-numbers
fax-recipient-phone-numbers
net-destination.
8 IFAX
Job name
User Name
Completion Status
IIO status
Accounting User ID
Accounting Account ID
total-number-of-smtp-recipients
smtp-recipients

 Loading...
Loading...