Xerox Multi-Function Device Security Target
19
Copyright
2013 Xerox Corporation. All rights reserved.
3. Security Problem
Definition
3.1. Definitions
3.1.1. Users
Users are entities that are external to the TOE and which interact with the
TOE. There may be two types of Users: Normal and Administrator, as shown
in Table 7.
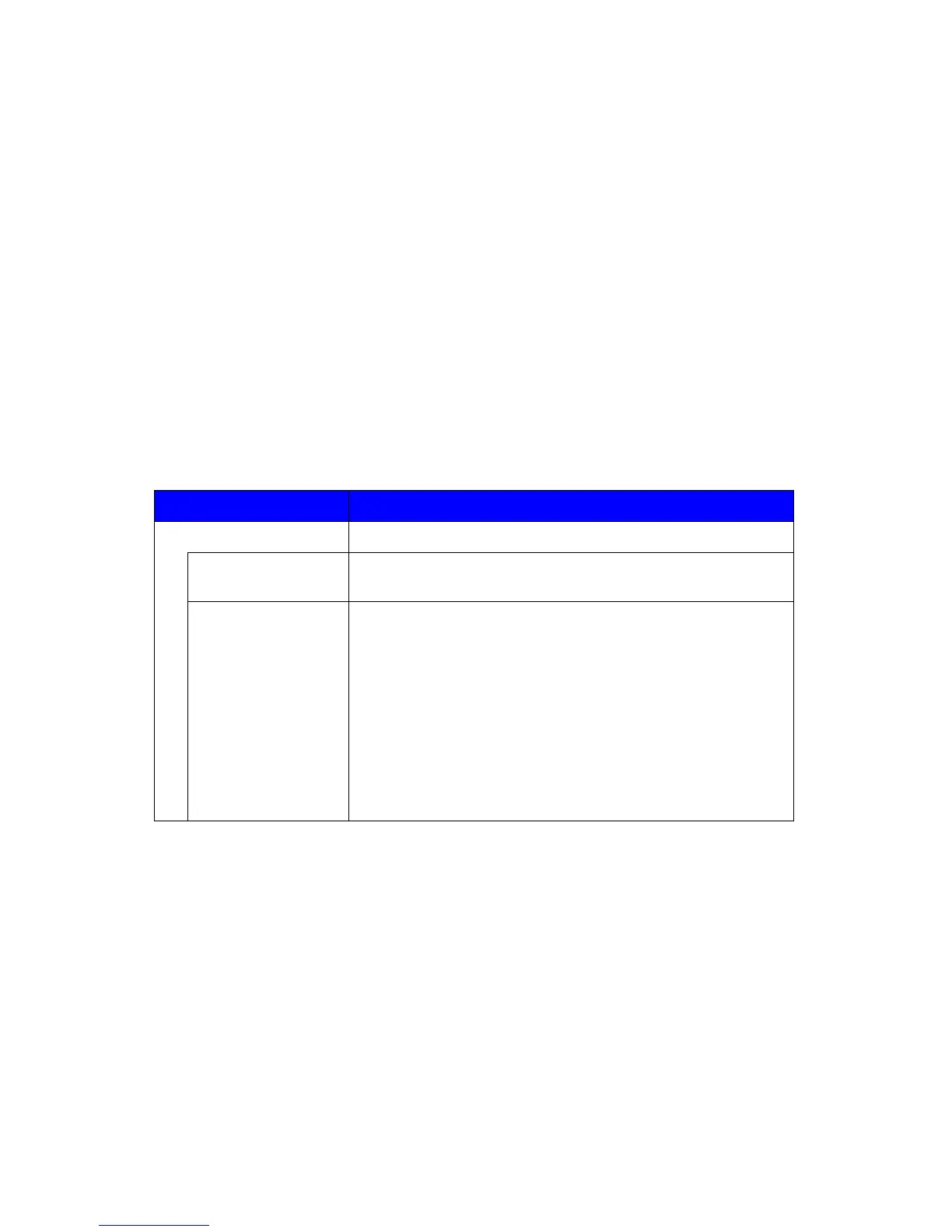
Table 7: Users
A User who is authorized to perform User Document Data
processing functions of the TOE
A User who has been specifically granted the authority to
manage some portion or all of the TOE and whose actions
may affect the TOE security policy (TSP). Administrators may
possess special privileges that provide capabilities to override
portions of the TSP.
This ST specifies:
U.ADMINISTRATOR (System Administrator)
U.ADMINISTRATOR (Accounting Administrator)
If U.ADMINISTRATOR is specified without identifying the
above, then it refers to both roles.
3.1.2. Objects (Assets)
Objects are passive entities in the TOE, that contain or receive information,
and upon which Subjects perform Operations. In this Security Target, Objects
are equivalent to TOE Assets. There are three types of Objects: User Data,
TSF Data, and Functions.
3.1.2.1. User Data
User Data are data created by and for Users and do not affect the operation
of the TOE Security Functionality (TSF). This type of data is composed of two
objects: User Document Data, and User Function Data, as shown in Table 8.

 Loading...
Loading...















