Xerox Multi-Function Device Security Target
9
Copyright
2013 Xerox Corporation. All rights reserved.
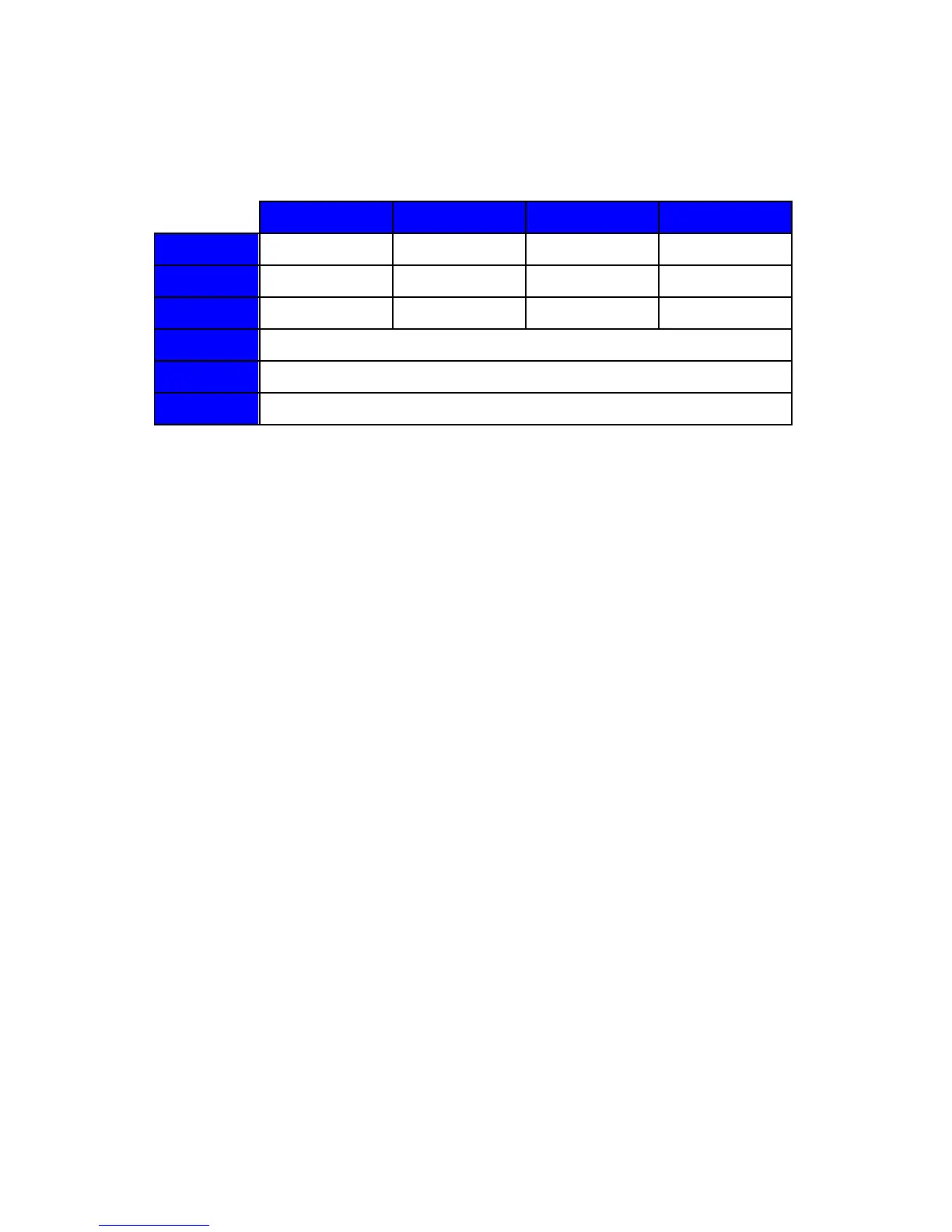
Table 2 below shows the various models and capabilities of the TOE. The
models vary in printing speed, paper capacity and available finsher options.
Table 2: Models and capabilities
Printing speed, paper capacity and available finsher options.
The TOE provides the following security features:
Image overwrite. This feature overwrites temporary image files
created during a copy, print, scan or fax job when those files are no
longer needed. Overwrite is also invoked at the instruction of a job
owner or administrator and at start-up.
Hard disk encryption. The TOE stores temporary image data created
during a copy, print, scan and fax job on the single shared hard disk
drive (HDD). This temporary image data consists of the original data
submitted and additional files created during a job. All partitions of the
HDD used for spooling temporary files are encrypted. The encryption
key is created on each power-up.
Audit. The TOE generates audit logs that track events/actions (e.g.,
print/scan/fax job submission) to identified users. The audit logs,
which are stored locally in a 15000 entry circular log, are available to
TOE administrators and can be exported in comma separated format
for viewing and analysis.
Network filtering. The TOE allows filtering rules to be specified for
IPv4 network connections based on IP address and port number.
Secure communication. The TOE provides support for a number of
secure communication protocols:
o Transport Layer Security (TLS) support is available for
protecting communication over the Web User Interface (Web
UI).
o Secure Shell (SSH) File Transfer Protocol (SFTP) and TLS are
available for protecting document transfers to a remote file
depository.
o Internet Protocol Security (IPsec) support is available for
protecting communication over IPv4 and IPv6 networks.
 Loading...
Loading...















