C613-22104-00 REV B Packet Flow Architecture | Page 26
Selecting a Security Solution Advanced Network Protection
Firstly, let's take a look at the basic security architecture.
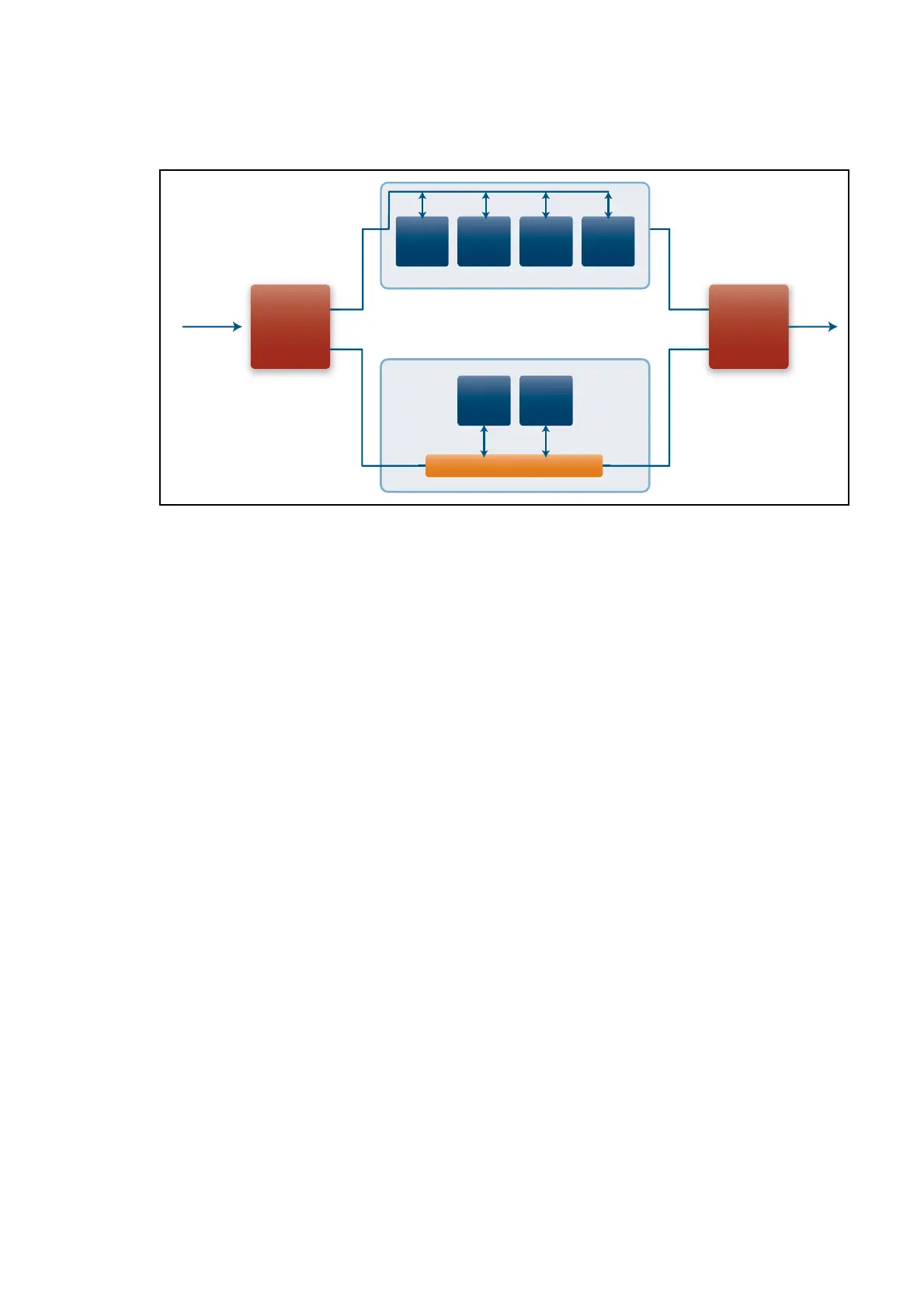
Figure 5: Firewall proxy and stream processing order
DPI
As data ingresses the firewall, it is first identified by the DPI application decoding engine if
application awareness feature is enabled. If selected, the inbuilt DPI engine contains a static library
of a around a 100 or so common Internet-based applications that it is capable of identifying.
However, if the Procera Networks' Network Application Visibility Library (NAVL) is selected as part of
Application Awareness feature then the number of identifiable applications added and stored in the
DPI engine library increases to many thousands.
Firewall, NAT, Traffic Shaping and SD-WAN policy-based routing rules can be optionally configured
to perform actions based on the application traffic identified via DPI.
DPI is not required for the proxy or stream-based security functions described in this guide to
operate.
For more information about Application Awareness and DPI (Deep Packet Inspection), see the
Application Awareness Feature and Configuration Overview Guide.
Stream and proxy engines
Once the application data is identified, it is processed via either the stream or proxy engine
forwarding path, and whether both stream-based and proxy-based security features are enabled.
If both stream and proxy-based security features are simultaneously enabled, then data will initially
be processed via the stream engine, and will subsequently be processed via the proxy engine.
All of the stream-based security features operate as a series of rule-sets within the Suricata Stream
engine. As each stream-based security feature is enabled, an associated set of rules is enabled and
applied in the stream engine. IP data is only processed by the security application rule-sets that it
FORWARDING
FIREWALL
NAT
SHAPING
IP REP IPS
MALWARE
PROTECTION
URL
FILTERING
WEB
CONTROL
ANTI-
VIRUS
PROXY ENGINE
PROXY
STREAM
IN
OUT
DPI APPLICATION
DECODING
ENGINE

 Loading...
Loading...