140
Cisco 3900 Series, Cisco 2900 Series, and Cisco 1900 Series Integrated Services Routers Generation 2 Software Configuration Guide
Chapter Configuring Security Features
Configuring VPN
Configure IPSec Transforms and Protocols
A transform set represents a certain combination of security protocols and algorithms. During IKE
negotiation, the peers agree to use a particular transform set for protecting data flow.
During IKE negotiations, the peers search multiple transform sets for a transform that is the same at both
peers. When a transform set is found that contains such a transform, it is selected and applied to the
protected traffic as a part of both peers’ configurations.
To specify the IPSec transform set and protocols, follow these steps, beginning in global configuration
mode.
SUMMARY STEPS
1. crypto ipsec profile profile-name
2. crypto ipsec transform-set transform-set-name
3. crypto ipsec security-association lifetime {seconds seconds | kilobytes kilobytes}
DETAILED STEPS
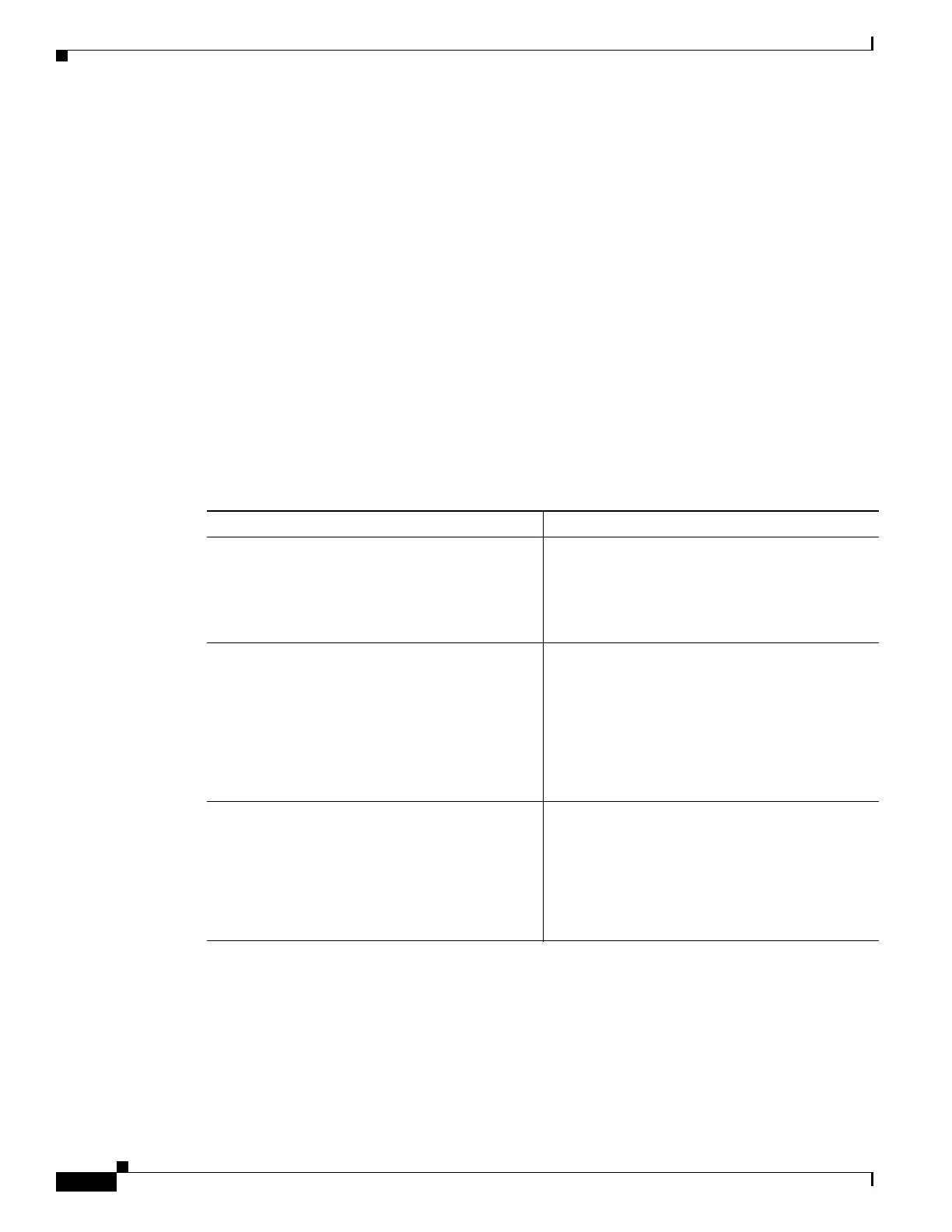
Command or Action Purpose
Step 1
crypto ipsec profile profile-name
Example:
Router(config)# crypto ipsec profile pro1
Router(config)#
Configures an IPSec profile to apply protection on
the tunnel for encryption.
Step 2
crypto ipsec transform-set transform-set-name
transform1 [transform2] [transform3]
[transform4]
Example:
Router(config)# crypto ipsec transform-set
vpn1 esp-3des esp-sha-hmac
Router(config)#
Defines a transform set—an acceptable
combination of IPSec security protocols and
algorithms.
See Cisco IOS Security Command Reference for
detail about the valid transforms and
combinations.
Step 3
crypto ipsec security-association lifetime
{seconds seconds | kilobytes kilobytes}
Example:
Router(config)# crypto ipsec
security-association lifetime seconds 86400
Router(config)#
Specifies global lifetime values used when IPSec
security associations are negotiated.
See Cisco IOS Security Command Reference for
details.
 Loading...
Loading...