Configuring Secure Shell (SSH)
Configuring the Switch for SSH Operation
4. Add any data required by your SSH client application. For example Before
saving the key to an SSH client’s "known hosts" file you may have to insert
the switch’s IP address:
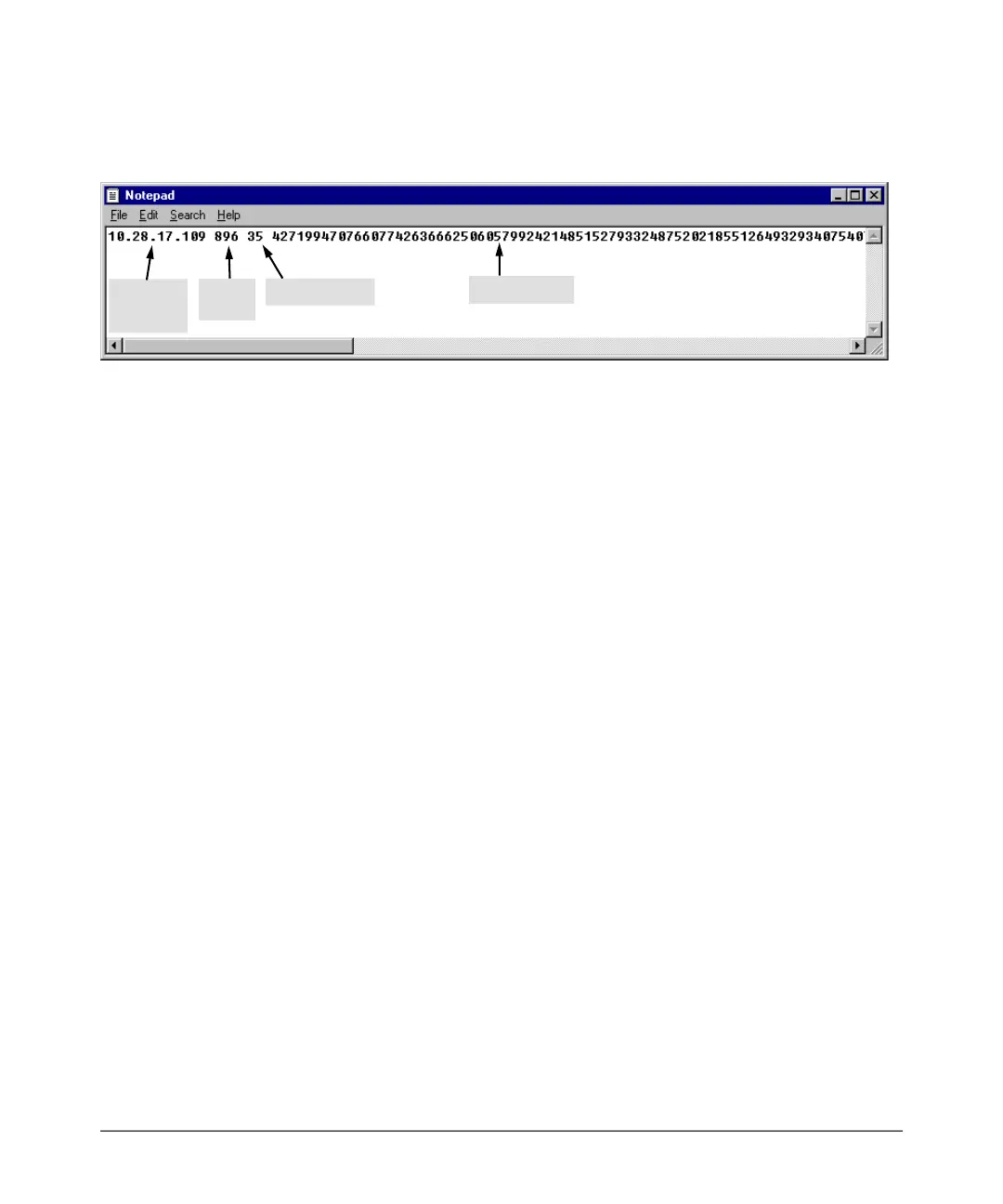
Size
IP
Bit
Exponent <e>
Modulus <n>
Inserted
Address
Figure 7-9. Example of a Switch Public Key Edited To Include the Switch’s IP Address
For more on this topic, refer to the documentation provided with your SSH
client application.
Displaying the Public Key. The switch provides three options for display-
ing its public key. This is helpful if you need to visually verify that the public
key the switch is using for authenticating itself to a client matches the copy
of this key in the client’s "known hosts" file:
■ Non-encoded ASCII numeric string: Requires a client ability to
display the keys in the “known hosts” file in the ASCII format. This
method is tedious and error-prone due to the length of the keys. (See
figure 7-8 on page 7-13.)
■ Phonetic hash: Outputs the key as a relatively short series of alpha-
betic character groups. Requires a client ability to convert the key to
this format.
■ Hexadecimal hash: Outputs the key as a relatively short series of
hexadecimal numbers. Requires a parallel client ability.
For example, on the switch, you would generate the phonetic and hexadecimal
versions of the switch’s public key in figure
7-8 as follows:
7-14
 Loading...
Loading...











