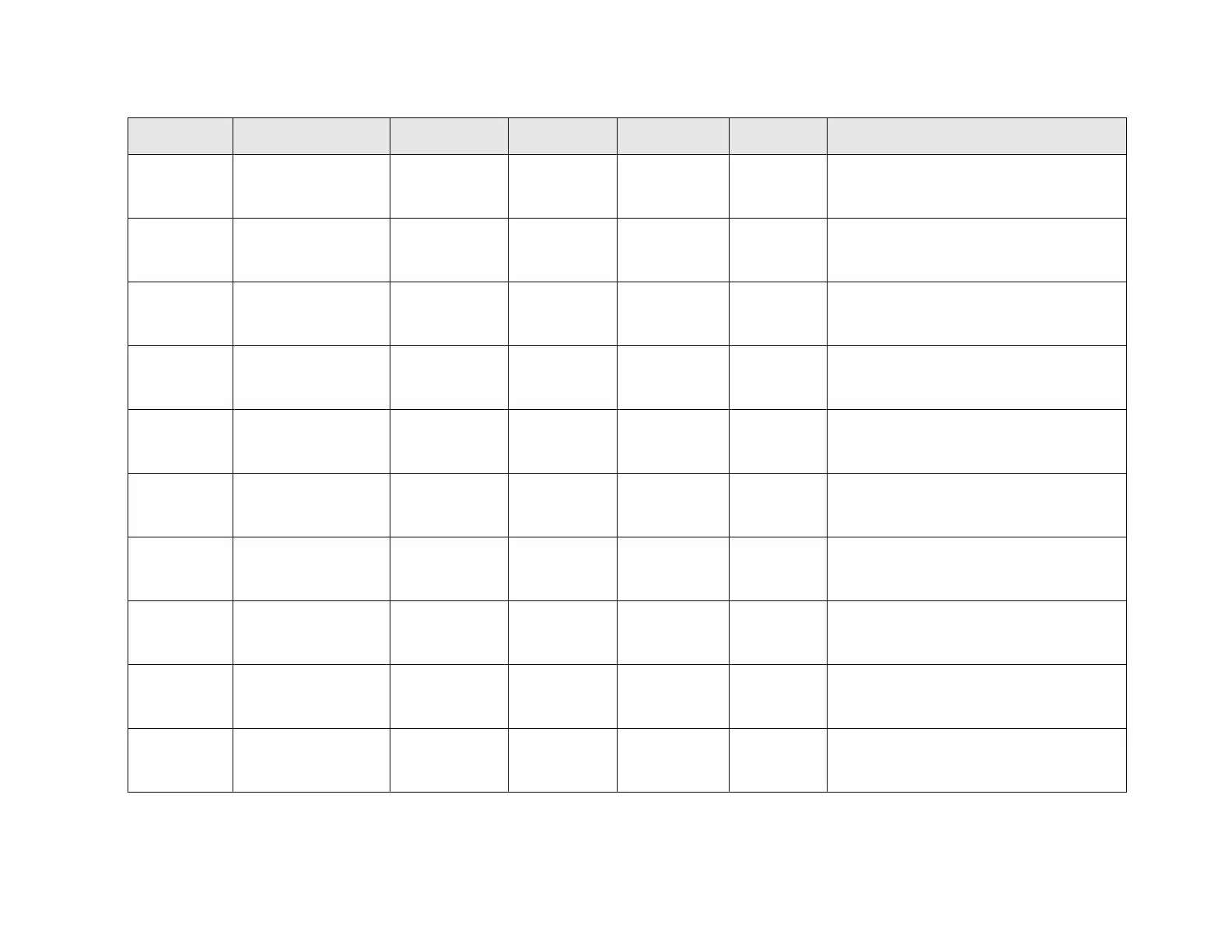
Allowed use in the certified configuration
High-Level Data Link
Control
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Layer 2 Tunneling
Protocol
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Point-to-point
protocol over Ethernet
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
Follow best practices for the secure usage as
there are no restrictions on use of these
protocols
 Loading...
Loading...















